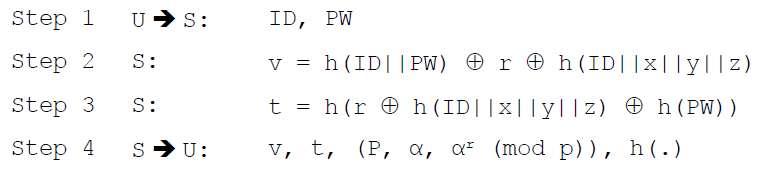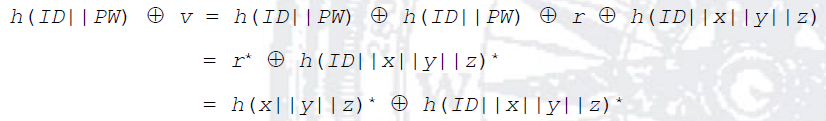Introduction
Remote user authentication scheme is a key security component for electronic services and it must provide the following security requirements (Madhusudhan and Mittal, 2012): 1) no verification table, the server should not store any information about the user in a database; 2) users can choose and change their password freely, users should have the option to create and to modify their password without assistance; 3) mutual authentication, user and server must be authenticated by each other; 4) password dependent, the user’s smart card should not compute a login request message without the previous verification of user’s identity; 5) session key agreement, after the successful authentication phase, the user and the server should share a session key; and 6) user’s anonymity, the login request message should not contain the user’s identity.
In 1981, Lamport (1981) proposed the first remote user authentication scheme based on one-way hash function. However, the server needs to maintain a verification table, making it susceptible to steal or to modify information stored in a database (Chang and Wu, 1991; Hwang and Li, 2000). Later, Hwang, Chen and Laih (1990) introduced the use of smart cards. They proposed the first remote user authentication scheme without the existence of verification table.
Ten years later, Chang and Wu (1991) proposed a scheme based on the Chinese Remainder Theorem. Their scheme was inspired from Shamir’s identity-based signature scheme (Shamir, 1984). Later, Chang and Liao (1994) proposed the first remote user authentication scheme based on ElGamal’s public key cryptosystem (ElGamal, 1985) and time-stamping. Since 1994, many schemes based on ElGamal’s public key cryptosystem have been proposed (Awasthi and Lal, 2005; Chan and Cheng, 2000; Chang and Hwang, 2003; Hölbl and Welzer, 2009; Hwang and Li, 2000; Kumar, 2004; Lee and Chiu, 2005; Ramasamy and Munivandi, 2009; Rhee, Kwon and Lee, 2009; Shao, 2004; Shen, Lin and Hwang, 2003; Tseng, 2007; Wang and Chang, 1996; Yoon, Ryu and Yoo, 2004) to enhance security.
However, previous works do not maintain the user’s anonymity during the login phase because each user sends its identity in clear text to the server, making the schemes susceptible to identity theft, impersonation attack, and forgery attack (Chan and Cheng, 2000; Das, Saxena and Gulati, 2004; Hölbl and Welzer, 2009; Leung et al., 2003; Shen, Lin and Hwang, 2003). Moreover, some schemes are based on time-synchronization which it is still a problem Juang, 2004; Lee, Kim and Yoo, 2005a; Liaw, Lin and Wu, 2006) in existing networks environments because the data transmission and processing delay is uncertain. Furthermore, previous works do not give the option to users to choose and to change their password freely (Lee, Kim and Yoo, 2005b).
In this paper, we point out that previous works are unsecured for electronic services because such works do not achieve the security requirements explained by Madhusudhan and Mittal (2012). For that reason, we propose a new scheme which provides all the security requirements for an ideal remote user authentication scheme (Madhusudhan and Mittal, 2012) and withstand very well known attacks to enhance the security. Moreover, we compare it with other related works in terms of security, demonstrating that the proposed scheme is more secure. Our scheme is inspired by the idea of Das, Saxena and Gulati (2004). The rest of this paper is organized as follows. In Section 2, we explain the proposed scheme. In Section 3, we carry out the security analysis and comparison of the proposed scheme with other related works. Finally, conclusions are given in Section 4.
Proposed scheme
Table 1 shows the notations used throughout this paper.
| U | User |
| ID | Identity of U |
| PW | Password of U |
| SC | Smart card of U |
| S | Server |
| x, y, z | Secret numbers of S |
| h( ) | One-way hash function |
| SKUS | Session key between U and S |
| ESK( ) | Symmetric encryption using SK |
| DSK( ) | Symmetric decryption using SK |
| NU, NS | Nonce of U and Nonce of S |
| ZP* | Multiplicative group |
| α | Generator of ZP* |
| a | Random exponente of U |
| ( | Exclusive-OR operation |
| || | Concatenation operation |
| → | Secure cannel |
| → | Open cannel |
Source: Own elaboration
Our scheme is composed of the following phases:
Phase 1- Initialization. In this phase, S computes public parameters used by each user in the scheme.
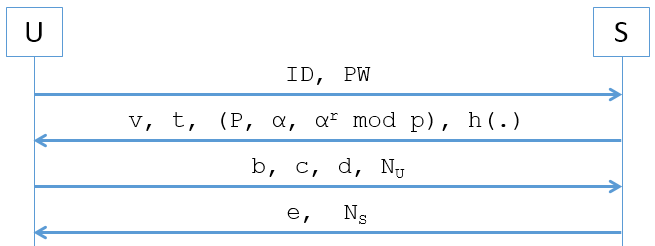
Phase 2- Registration. In this phase, U shares personal information with S to be part of the system. As a result, U obtains its smart card with security parameters (v, t, (P, α, α r (mod p)), h(.)).
Phase 3- Login. In this phase, U computes the login request message (b, c, d, N U ).
Phase 4- Mutual authentication and session key. In this phase, U and S verifies the identity of each other and creates a session key (SK US ).
Phase 5- Password change. In this phase, U can choose a new password whenever and wherever it wants.
The protocol is presented in Figure 1.
Now, we describe each phase of the proposed protocol.
Phase 1: S generates two public parameters P and α, where P is a large prime number and α is a primitive root in Galois Field GF(P). Then, S chooses three numbers (x, y, z) with a length of 256 bits. Next, S computes r = h(x||y||z) creating its secret key. Later, S computes α r (mod p) creating its publick key. In this scenario, the triplet (P, α, α r (mod p)) are the public parameters of S. Moreover, S publishes the one-way hash function h( ) used in the scheme.
Phase 2: S creates the security parameters of U as follows:
U sends ID and PW to S through a secure channel. Afterthat, S calculates v computing two hash functions and two XOR operations. S uses the information received from U, the three numbers (x, y, z) and secret key r. Then, S calculates v computing two hash functions and one XOR operation. Finally, S stores the security parameters (v, t, (P, α, α r (mod p)) and one-way hash fuction h( ) in U’s SC.
Phase 3: This phase is invoked whenever U wants to login S. First, U inserts its SC into the smart card reader and keys its ID and PW. Then, SC carries out the following steps:
After U keys its ID and PW, its SC computes the following hash values: h(ID||PW) and h(PW). Then, SC recovers r * ⊕ h(ID||x||y||z)* from v as follows:
Later, SC verifies the identity of U by means of the comparison between t * and t. If the verification is positive, the identity of U is verified and the process continues; otherwise, SC closes the session. Next, SC generates the secret key a, and it computes b and c using ElGamal cryptosystem. Then, SC generates a random number N U . Later, SC computes d using the information recovered in step 2 and the U’s ID. Finally, U sends the login request message (b, c, d, N U ) to S through an open channel.
Phase 4. After the login request message (b, c, d, N U ) is received, S performs the following operations:
S decrypts ID as follows:
Then, S computes d * and uses it to verify the identity of U comparing d * and d. If they are equal, U is a legal user; otherwise, the session is closed. Next, S computes the session key SK US using secret information known only by it h(x||y||z)||h(ID||x||y||z), information received from U (h(ID)) and information generated by each other during the current session N U and N S . Later, S encrypts N U and N S using the session key E SK (N U + N S ) as verification proof. Finally, S sends the login response message (e, N S ) to U through an open channel.
Upon receiving the login response message (e, N S ), U performs the following operations:
U computes the session key SK US and decrypts e. As result, U knows (N U + N S )* and verifies the validity of the session key by means of the comparison between (N U + N S )* and (N U + N S ). If the comparison is correct, the session key is accepted and the legitimacy of S is validated.
Note: U and S can exchange messages using the session key SK US .
Phase 5. When U wants to change its PW with a new password PW new , it needs to carry out the following process.
Security Analysis
In this section, we discuss the security features of the proposed scheme. The security analysis corroborates the security advantages of the proposed scheme.
Resist off-line guessing attack: in the proposed scheme, U’s smart card contains (v, t, (P, α, α r (mod p), h( )) after registration phase. Assuming that an adversary is a legal user of the system, it can obtain r ⊕ h(ID||x||y||z) from v = h(ID||PW) ⊕ r ⊕ h(ID||x||y||z) because the attacker knows ID and PW. Unfortunately for the adversary, r ⊕ h(ID||x||y||z) does not provide any sensitive information. In this case, S uses four pieces of secret information instead of one. Moreover, h(ID||x||y||z) is personalized by ID, making it unique in the scheme.
Resist impersonation attack: if the adversary knows the login request message (b, c, d, N U ), the attacker cannot compute a valid login request message (b *, c *, d *, N U *) without knowing the correct ID and h(ID||x||y||z) because c and d requires the knowledge of both values. Moreover, S checks the validity of d in the mutual authentication and session key agreement phase.
Resist server spoofing attack: in this case, the adversary cannot compute a valid login response message (e, N S ) because the attacker needs to know the secret numbers of S. Moreover, the attacker cannot compute a valid session key SK US = h(h(ID)||h(x||y||z)||h(ID||x||y||z)||N U ||N S ) because it does not know the values of ID, h(x||y||z) and h(ID||x||y||z) corresponding to the legal U.
Resist recovers private data attack: if the adversary tries to recover encrypted information, it needs to compute the correct SK US . In this case, the attacker cannot compute the correct session key because it does not know the correct values of ID, h(x||y||z) and h(ID||x||y||z). Moreover, the adversary can find a if it can compute a discrete log in the large prime modulus p, where in practical situation is a hard problem.
Avoids inefficiency for error password login: in the proposed scheme, U’s smart card verifies the identity of U by means of two process: 1) knowledge of ID and PW to recover r ( h(ID||x||y||z) and 2) knowledge of PW to compute a valid t = h(r ⊕ h(ID||x||y||z) ⊕ h(PW)) in order to validate the identity of U.
Provides user’s anonymity: in the proposed scheme, U’s anonymity is preserved at each login request because U does not send its ID in clear over an open network. The login request message (b, c, d, N U ) does not provide information about the U’s identity. Moreover, the value of d is dynamic every time because this value is computed using a nonce N U . Hence, the adversary cannot identify the victim trying to login into the server.
Formal security analysis
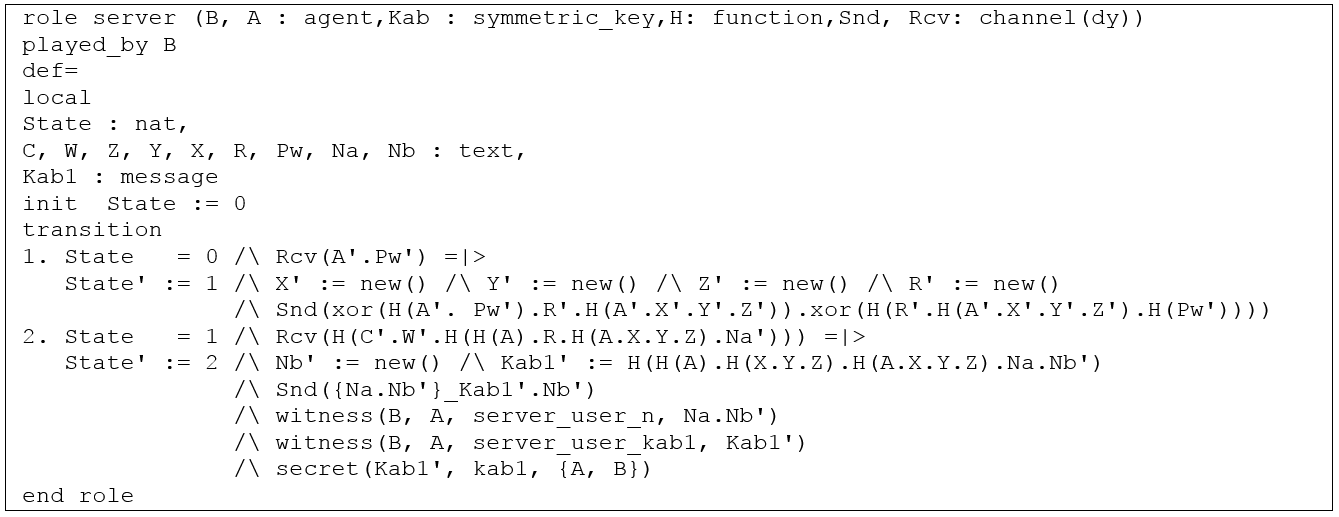
In order to verify the security goals of the proposed protocol - mutual authentication and secrecy of the session key - we have modelled and analysed it using High-Level Protocol Specification Languange (HLPSL) (Chevalier, 2004) and Automated Validation of Internet Security Protocols and Applications (AVISPA) tool (Armando, 2005). HLPSL is a modelling language to write specifications for security protocols based on roles. Each role contains a set of actions of a single agent, which its transitions is indicated as a state. On the other hand, AVISPA tool consists of four back-ends called: Constraint-Logic-Based Attack Searcher (CL-AtSe), On-the-Fly Model-Checker (OFMC), SAT-Based Model-Checker (SATMC), and Tree Automata-Based Protocol Analyser (TA4SP).
We have considered two players - user (A) and server (B) -, symmetric key (Kab) and one-way function (H) knowledge by each player, and communication channels - user (SA, RA) and server (SB, RB) -, where each communication channel assumes the presence of a Dolev-Yao Intruder (Dolev and Yao, 1983). The Dolev-Yao Intruder (dy) implies the following assumptions: 1) the adversary or attacker can capture any message in the network; 2) the adversary or attacker can impersonate any legitimate user in the system; and 3) the adversary or attacker can execute many concurrent instances of the protocol. Under this circunstances, we have modelled the role of user and server as follows:
We tested our protocol using OFMC and CL-ATSE models in order to verify that it achieves the following goals:
As a result, the outputs returned a “SAFE” state under the OFMC model and “No Attack Found” under the CL-ATSE model.
Security Comparison
We summarize the security and functionality of the proposed scheme, making comparison with related works in Table 2. It demonstrates that our scheme can achieve the essential security requirements mentioned in Section 1.
Table 2. Comparison with related works
| Security requirement | Chang and Liao, 1994 |
Hwang and Li, 2000 |
Yoon, Ryu and Yoo, 2004 |
Ramasamy and Muniyandi, 2009 |
Our scheme |
|---|---|---|---|---|---|
| No verification table | Yes | Yes | Yes | Yes | Yes |
| User chooses and changes her password freely | No | No | Yes | No | Yes |
| Mutual authentication | No | No | Yes | Yes | Yes |
| Session key agreement | No | No | Yes | No | Yes |
| User’s anonymity | No | No | No | No | Yes |
| No time-synchronization | No | No | Yes | No | Yes |
Source: Own elaboration
Table 2 demonstrates that users can choose and change their password whenever they want, in our proposed scheme, whereas the schemes proposed by Chang and Liao (1994), Hwang and Li (2000) and Ramasamy and Muniyandi (2009) do not provide this security requirement. Moreover, the schemes proposed by Chang and Liao (1994) and Hwang and Li (2000) do not provide mutual authentication and session key agreement, making their scheme unsecured for electronic services. The main advantage of the proposed scheme is based on the concept of dynamic identity introduced by Das et al. (2004), where the user does not send its ID, in clear, over an open network.
Conclusions
In this paper, we proposed a secure remote user authentication scheme based on ElGamal Public Key Cryptosystem, one-way hash function and nonce. Security analysis proved that our scheme prevents very well-known attacks and maintains the user’s anonymity. Moreover, we have carried out formal security analysis of our protocol using the popular automated tool AVISPA. The formal security analysis proved that our protocol is safe. Furthermore, security comparison between our protocol and previous works showed that our scheme is more secure, making it feasible for electronic services.











 text new page (beta)
text new page (beta)