INTRODUCTION
The Digital Imaging and Communications in Medicine (DICOM) file is a standard [1] with which sundry medical equipment work to produce digital images. In general terms is the way in which the stewardship of medical files services are defined, including the electronic patient record (EPR). In this context, a DICOM file is composed by a data set of pixels with metadata at the header which relates the image with its respective EPR [2] [3] [4] [5]. In this way, the enhancement in technologies like telecom have leave us the growth of services based on DICOM files for medical images transmission throughout Picture Archiving and Communication Systems (PACS), which is a technology that complies the DICOM standard, also allows the creation of different applications such as telemedicine, the remotely diagnose, among others, opening the possibility of give a better clinical analysis or treatment, in interest of the plan of patient’s care. Thus, during its lifetime, a medical image can be transmitted several times inside hospitals, or even, outside of them, however, this scenario can introduce some risks regarding to the management and information security that must be mitigated because medical data are confidential [2] [3] [4] [5], and the conventional informatics security tools such as antivirus, cryptography tools or firewalls, to name a few, cannot solve all security issues of medical data. In this way, data hiding is a research field that has been widely proposed for improving the management and information security of medical imaging, concealing mainly binary data to create a trustworthy link between these data and the image.
So, it is important to ensure that the internet exchanged images correspond from their original images as a malicious user can modify considerable evidence of a patient's condition when they are sent and change the outcome of the patient’s diagnosis as has been demonstrated by Yisroel Mirsky [6]. He modified 2D and 3D medical images by means of a generative adversarial network (GAN) deep neural network. As result the altered images presented variation in tonalities.
To preserve their integrity, various methods or techniques of cryptography [7] [8] [9] [10]11], visual cryptography and visual steganography have been developed, both of which are used to hide or protect the information in the images.
Naor and Shamir [12], first proposed visual cryptography to allow a user to share information through N shares of the secret image and its use has been extended to several applications [13], since it represents a simple and computationally uncomplicated way to exchange images. On the other hand, there are several techniques used for steganography of images where the information is hidden exclusively in the images, these techniques can be divided into two groups focused on the spatial or frequency domain [14] [15] [16] [17].
Cryptography differs from steganography in the sense that cryptography focuses on protecting the content of the information while steganography focuses on hiding the information. Both forms allow us to exchange information securely, however neither is perfect and information can be broken or compromised. There are several researchers who propose to implement both techniques allowing to protect and hide the information of an image to increase the security of conventional methods.
Vinothkanna [18], proposes to implement RSA cryptography incorporated into steganography for files in multiple formats applied to images, to increase security to common stenographic methods. Thus, provides a highly secure transmission of information, to validate his proposal performs PSNR and SSIM tests, ensuring the efficiency of the method. On the other hand, Gupta Shailender and Ankur Goya [19], explain that the use of least significant bit (LSB) as a steganography method, in which the LSB of the image is supersede by a bit of the data, is susceptible to steganalysis. However, encrypting the data and hiding it in an image increases the security of the LSB method, with their proposed method concluded that it leads to an increase in execution time, but the resulting level of security is worth it. Dhiman and Kasana [20], present two visual cryptography techniques, in this process the secret image, the cover image and the resulting image have the same dimensions, the pixels selected from the cover image are replaced by pixels from the secret image, this allows the recovered image is the same as the original image. Back to previous work, Richa and Ashwani [21], proposed to expand the cover image to make the embedded pixels as imperceptible as possible, as well as increasing the security of the method by encrypting the pixel values of the secret image (medical image), which makes the recovery process more complex.
Despite the above, there are several methods to improve security and, as mentioned above, steganography, cryptography and hashing by themselves may not solve all issues related with the information security. However, the combination of these techniques could improve security, making it more difficult to retrieve information in an unauthorized way. Therefore, the following system is proposed, which is versatile to implement in real scenarios and allows the system to be secure. Using conventional cryptographic techniques such as circular encryption and steganography techniques by substitution of the least significant bits to increase the security of both methods as proposed by Vinothkanna and Gupta.
Employing pixel replacement as proposed by Dhiman and Richa with the variant of considering a cover image, as well as an increase in information because the hidden image has grayscale bit-depth of 12 bits, averaging the replaced pixels to provide some degree of imperceptibility, and finally adding the metadata and providing a system to verify the integrity of the file received by a hash function.
Motivation and contribution
Although the DICOM file has several security standards, these standards do not guarantee that the information it contains cannot be modified. Nowadays, visual cryptography has focused on protecting the image of the DICOM file obtaining relevant results; however, these proposals leave aside the information related to the image, therefore, a method is proposed to hide both the medical image and its respective metadata in a color cover image of the patient.
The purpose is to briefly identify the user who owns the medical image, as well to allow the medical image to be hidden within an identification image so that it can be sent as a secure transmission media protecting the integrity of the hidden image. An important contribution is related to the recovered medical image having the same bit depth as the original image, this is because the system allows working with medical images with a bit depth equal to or less than 12 bits regardless of whether the bit depth of the covered image is 24 bits/pixel.
On the other hand, the metadata contains information that may be relevant to whoever performs a study on the image, as it contains both medical information and personal information that may be of use to the medical staff, as well as to ensure again that the retrieved DICOM file belongs to the person who appears in the cover image. Including an ID image as a cover image allows both medical institutions and physicians to verify immediately that the face of the person in the image corresponds to the person receiving the studies or being diagnosed is the same, thus allowing a study-patient linkage.
MATERIALS AND METHODS
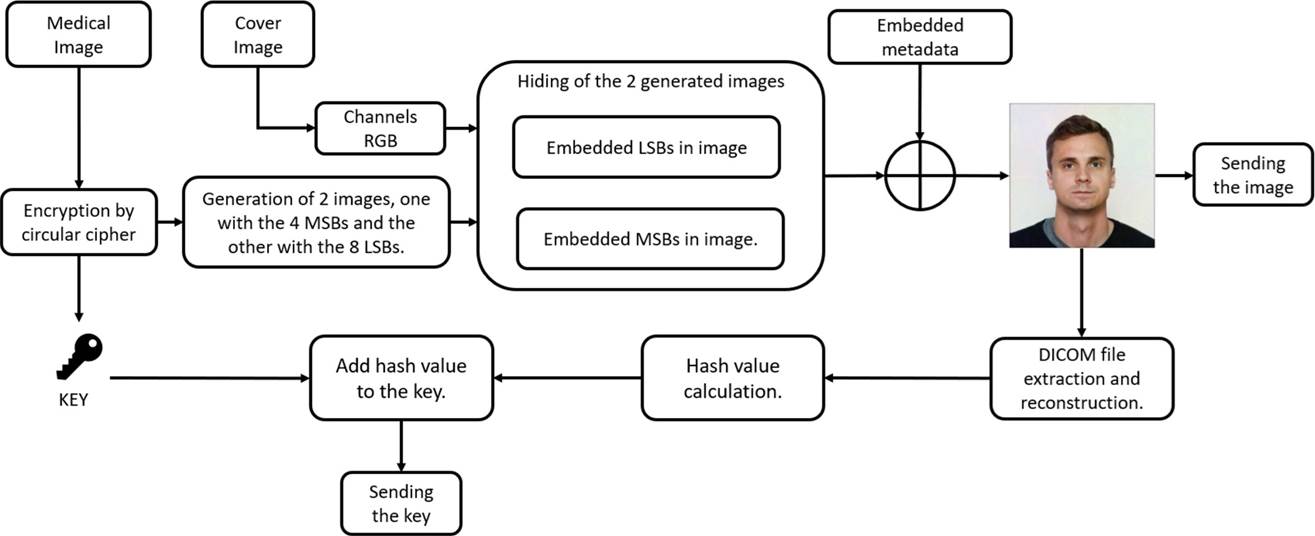
The DICOM file hiding process is shown in Figure 1, where the medical image and metadata are separated. The medical image is encrypted by the circular encryption method, two images and a key are obtained. The first image contains the four most significant bits, the second one the eight least significant bits. On the other hand, the cover image is splitted into its RGB channels, to hide the data.
The obtained two images and the metadata are hidden into the RGB channels of the cover image, resulting in the entire DICOM file embedded into the cover imagen. To validate the integrity of the DICOM file, it is retrieved to obtain its hash value and add it to the key.
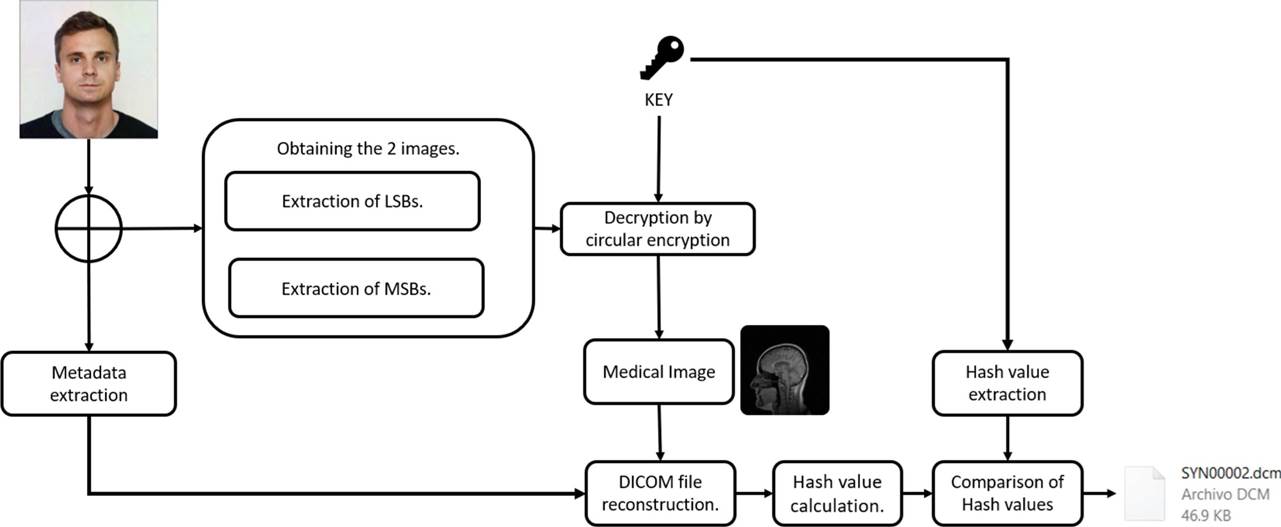
The extraction process shown in Figure 2, retrieves the metadata the Most Significant Bits (MSB's) and Least Significant Bits (LSB's) images. Then, the images are joined and decrypted, reconstructed DICOM file adding the metadata and then compared with their hash function. The quality of the retrieved medical image is compared with the original, the results are shown in section “Simulation, analysis and results”.
To have a better understanding of the methodology, the following subsections describe in greater detail each stage that makes up the proposal.
The encryption is described in subsection “Circular shift encryption”. The embedding of image with the remaining most significant bits is described in subsection “Embedded MSBs in cover image” and the leas significant bits in subsection “Embedded LSBs in image”, the embedding of metadata information in subsection “Embedded metadata”, obtaining the SHA256 of the resulting DICOM file in subsection “Digital signature”. Finally, the extraction process of medical image and metadata information in subsection “Extraction Procedure”.
Circular shift encryption
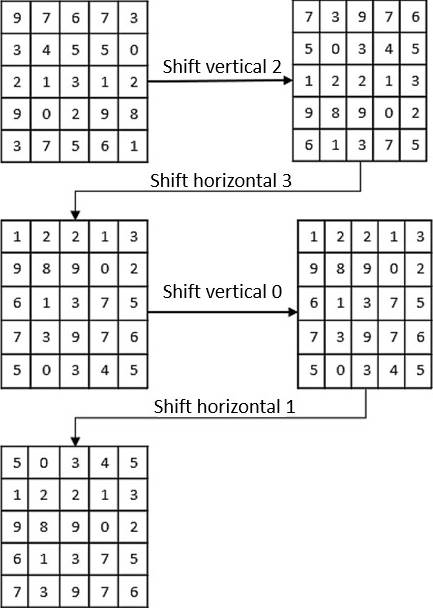
The circular Shift Encryption process shifts the columns and rows n positions to right and down respectively [22]. The number of shifts depends on certain values contained on a previously defined key. E.g., assuming a small key, which value is (2,3,0,1) applied to an (5*5) array; the following steps are showed:
The first digit (2) performs a circular right shift.
The second digit (3) performs a circular down shift.
Steps 1 and 2 are looped until completing all digits
If the digit is zero, no shift is performed. Show Figure 3.
The key is pre-computed through a series of random numbers stored in a one-dimensional array, the length of the array corresponds to the width of the cover image, and the maximum number stored corresponds to the maximum value of the dimensions of the cover image.
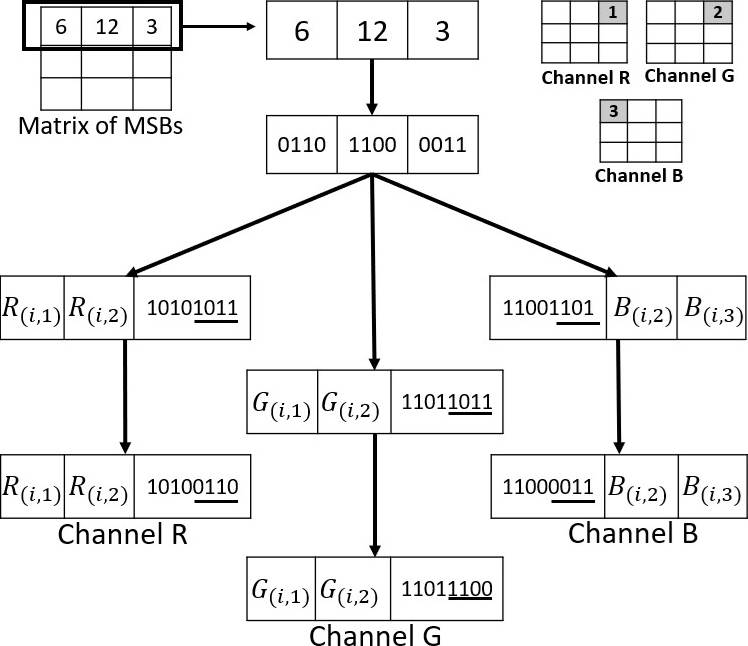
It is important to assume that the maximum depth of the medical image is 12 bits, with the selected image, the circular encryption process is performed. The resulting medical image is converted into two arrays (images) one of 4 bits most significant bits (MSB) and the other of least significant bits (LSB) 8bits.
Embedded MSBs in cover image
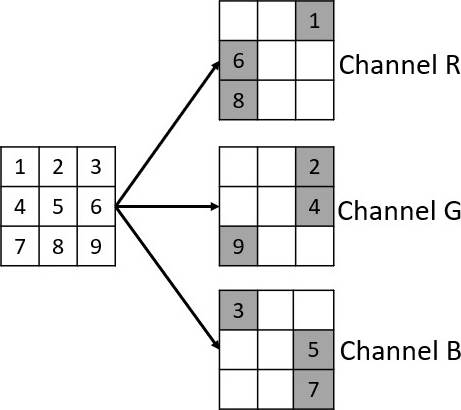
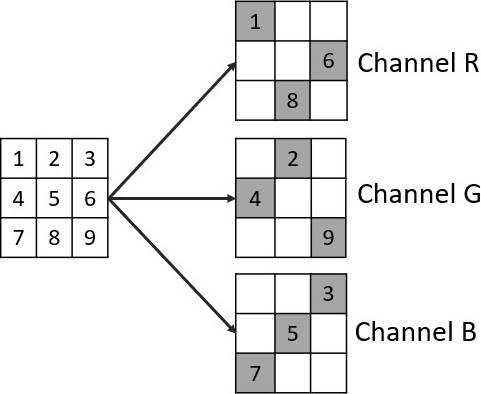
In order to embed an MSB array, we select a 3×3 pixel array of each RGB channel from the cover image. From each RGB arrays, 3 non-deterministic selected pixels will be used to embed the values of the MSB array as shown in Figure 4.
The pixel values in the MSB group will be embedded by modifying the last 4 bits of the selected pixels in each of the RGB channels, as shown in Figure 5, where the first row of the MSB array was selected and the last 4 bits of the selected pixels in the RGB channels were replaced.
Embedded LSBs in cover image
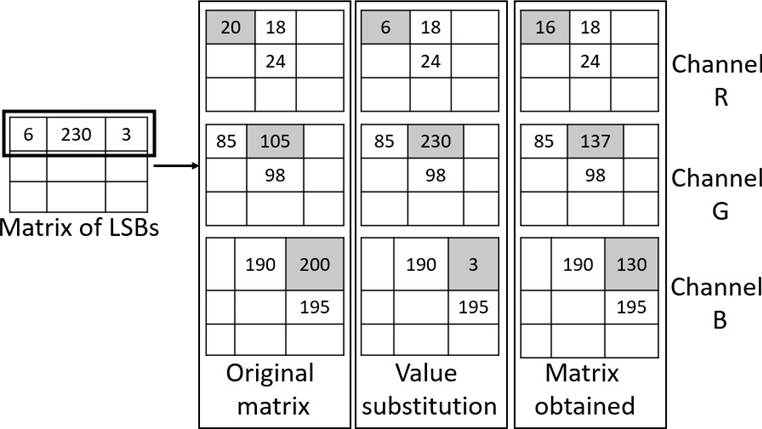
Same as the MSB embedding process, a 3×3 pixels array is selected for the LSB group. Then 3 non-deterministically selected pixels of each RGB channels, excluding those pixels that were already modified previously, as shown in Figure 6.
The values of the LSBs are embedded by replacing them with the value of the selected pixels, then each value inserted is averaged with the neighboring pixels whose values have not been modified. Considering that the embedded LSBs pixels have a value within the range of 0 to 254, averaging makes the value be imperceptible as well as being in the range of values allowed in the 8-bit cover image, as shown in Figure 7.
Embedded metadata
The DICOM file's metadata are relevant, since may contain patient ID information, the performed study; the medical equipment used; the medical institution information; image characteristics such as color, model, dimensions, bit resolution, etc. Therefore, it is crucial select the data that may be helpfully for the diagnosis.
For this proposal, selected data include ID data and data on the study performed, to be useful for the physician or medical institution.
Before performing the embedding, first an array of the same medical image dimensions is generated. The ni × m i position of the array will contain the ASCII value of each of the i - th letter information.
To embed the information, two pixels are selected at position ni, mj of each of the RGB channels. The selected pixels should not be those whose value has been changed during the embedding process of the medical image.
Each letter has an 8 bits assigned in the ASCII code. Therefore, the process modifies the last 4 bits of the selected pixels in the position ni, mj of the cover image.
There must be 2 pixels in the position n i, mj whose value had not been modified in the RGB channels, this ensures to hide a letter of the metadata in that position for the RGB channels. Modifying the last 4 bits of the cover image allows to preserve an imperceptibility at the moment of viewing the image.
Digital Signature
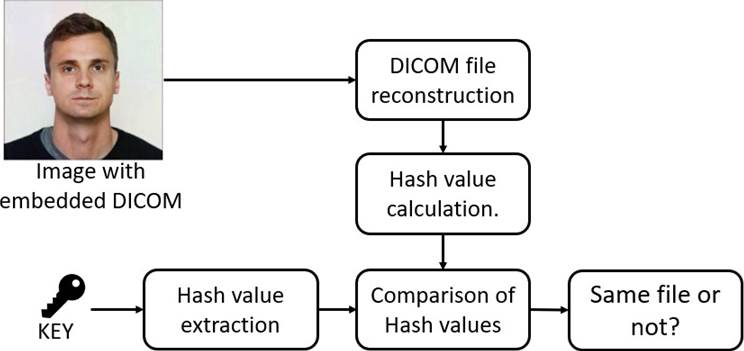
After the reconstruction of the DICOM file, it must be verified to make sure that it has not been altered. To verify the information's integrity, it is proposed to use the Secure Hash Algorithm (SHA-256) [23], of the sent file. Once the hash has been calculated, the hash is compared with hash that was received, as is shown in Figure 8.
In the process of reconstructing the DICOM file by the receiver, the SHA256 of the received file is recalculated and compared with the signature of the key file.
The objective of this process is to ensure that the reconstructed file was not modified by an external person, if the result of the comparison of both hashes match, it can be concluded that the DICOM file sent and the one obtained by the receiver are the same. In case of a function comparison mismatch, the received file should be discarded, which means that has been altered.
Extraction procedure
Once the cover image is received, the process to reconstruct the DICOM file starts. The steps for the extraction procedure are given below and show in Figure 2.
For every cover image’s RBG channel, LSBs and MSBs images are extracted.
Both images are combined according to the position of the MSBs and LSBs.
The resulting image is decrypted with the key.
Metadata is extracted from the cover image.
The DICOM file is reconstructed with the metadata and the resulting medical image.
RESULTS AND DISCUSSION
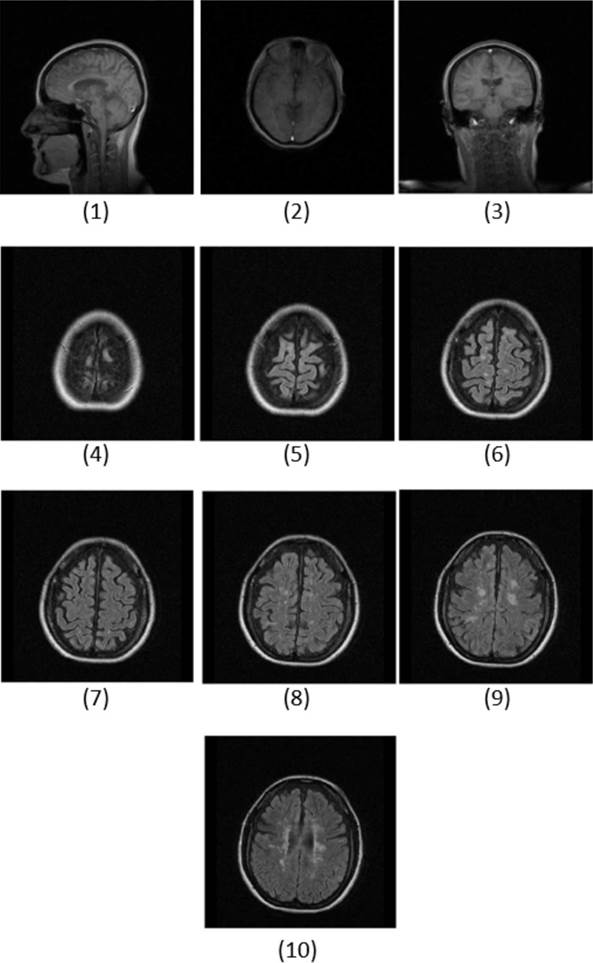
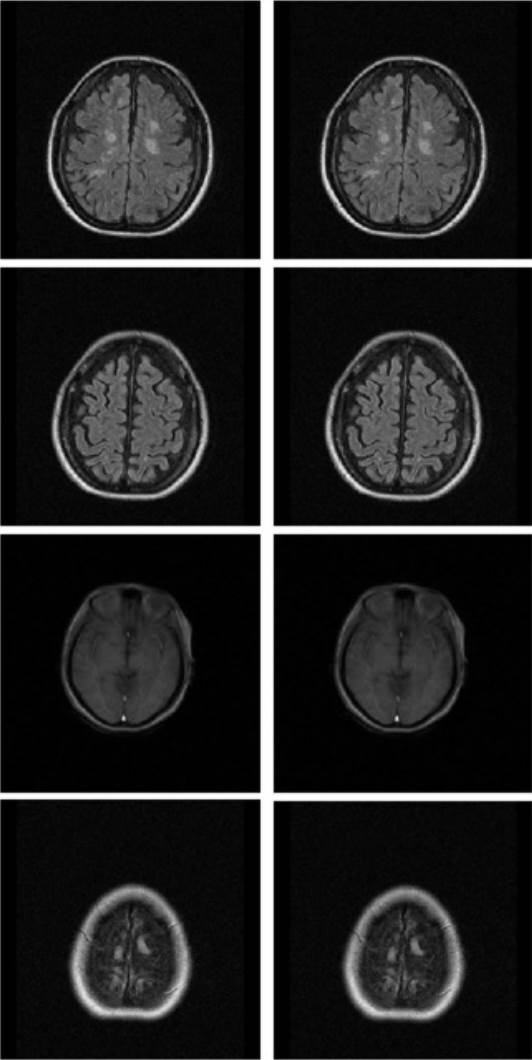
The proposed method was tested in MATLAB, in a 16 GB RAM machine and 3Ghz processor. The tests were performed using a set of 10 MRI images consisting of 2 body parts, side view of the head and brain, with a depth of 12 bits or a maximum hue level of 4095. The images in Figure 9, constitute the set of medical images corresponds to a dataset provided by Instituto Mexicano del Seguro Social (IMSS) for research purposes.
On the other hand, the patient identification images used as cover images, have different background colors, clothing, as well as different skin and hair tones, shown in Figure 10 (a). The images used in this process are 255x255.

Figure 10 (a) Cover images, (b) Resulting cover images with only embedded DICOM image, (c) Resulting cover image with DICOM imagen and metadata.
The dimensions of the test images are multiples of 3, in case both images are not multiples of 3, both images are analyzed to eliminate those rows and/or columns that contain little or no relevant information in order not to distort both images.
The medical image of dimensions 255x255 with a depth of 12 bits contains approximately 780,300 bits as shown:
While the color cover image with the same dimensions and a depth of 8 bits in each of the RGB channels contains 1,560,600 bits as shown below:
It can be concluded that the cover image has the capacity to store the medical image as well as the respective metadata.
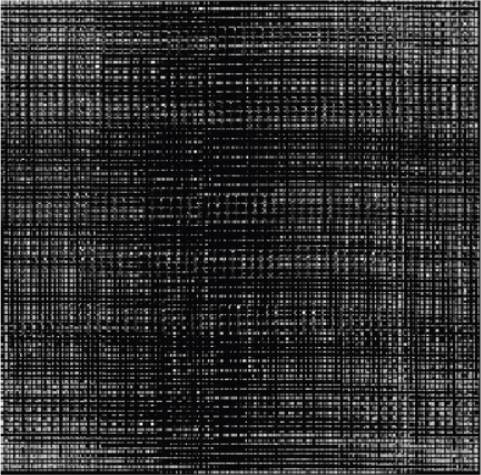
From the test DICOM file, the medical image is extracted to begin the image and metadata embedding process, as is described in section “Proposed methodology”. After the encryption, the image is shown in Figure 11.
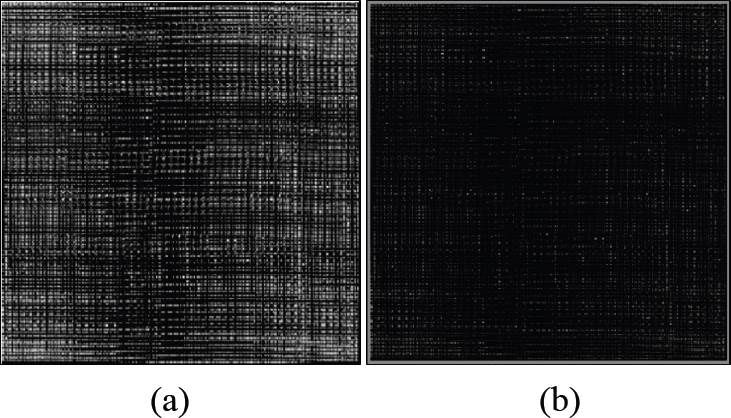
Then is converted to a 12-bit image and splitted into two images with a resolution of 8 bits and 4 bits the resulting images are shown in Figure 12, respectively.
With both resulting images, the embedding process is performed. Since in the MSB process the values of certain pixels are modified and in the LSB embedding process, the adjacent pixels of which some pixels were previously modified are considered, this order allows the hue level of the recovered pixel be like the original pixel and the changes made in the patient identification image to be less visible. The resulting image of the patient once the embedded process was performed shows in Figure 10 (b).
In the LSB embedding process, it is considered that one third of the cover image will be modified, so calculating the number of bits to be modified, the following result is obtained:
On the other hand, if we calculate the number of bits contained in the LSB image, we obtain the following result:
As can be observed, the space available in the cover image coincides with the space used to hide the bits in the LSB image. From the MSB embedding process, if we calculate the number of bits in the MSB image, we obtain the following result:
Adding the values of (4) and (5) gives the number of bits to be hidden calculated as (1), so there is no loss of bits.
As is previously mentioned, the DICOM formats contain a diverse collection of data from which it will be select the crucial data needed a correct diagnosed, Table 1, shows the selected data in the test DICOM file.
Table 1 Selected data.
| DICOM metadata field | Type |
|---|---|
| Format | CHAR |
| Width | INT |
| Height | INT |
| Bit Depth | INT |
| Color Type | CHAR |
| Study Date | INT |
| Accession Number | INT |
| Modality | CHAR |
| Study Description | CHAR |
| Code Meaning | CHAR |
| Resolution Factor | CHAR |
| Private Creator | CHAR |
| Manufacturer | INT |
| Institution Name | INT |
| Name | CHAR |
| Last Name | CHAR |
| Patient ID | INT |
| Patient Birthday | INT |
| Patient Sex | CHAR |
| Image Text | CHAR |
With the selected data the array is generated, with n×m dimensions like the cover image where in the position ni, mj it will contain a character, corresponding to the data. Once the array is filled, the data is inserted in the cover image as indicated section “Embedded metadata”. The resulting image is shown in Figure 10 (c). Once the DICOM file embedding process is finished, the resulting image is sent to the receiver, who then extracts the medical image as well as the metadata and reconstructs the DICOM file, calculates its SHA256 value and extracts the one contained in the key, compares both values to verify that the file preserves its integrity and was unmodified during its sending.
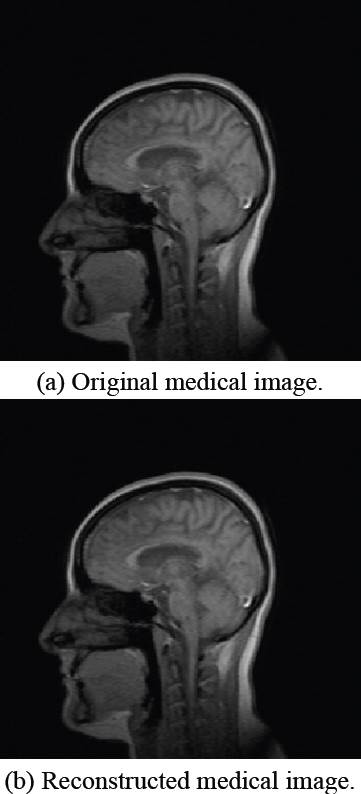
After verifying the integrity of the DICOM file, the similarity as also the quality of the recovered image with respect to the original medical image is determined by Peak Signal to Noise Ratio (PSNR) and Similarity Index Metrix (SSIM) tests [24], the original medical image and the recovered image are shown in Figure 13.
PSNR test is measure of reconstruction quality of an image, if the calculated value for PSNR is high or tends to infinity it is concluded that the image recovered quality is similar compared
PSNR calculates the image quality ratio between the signal power and the distorting noise. This ratio is in decibels and the equation is expressed as [21]:
From (6) peakval (Peak Value) is the maximum pixel value of the image, if it is an 8-bit image, the maximum value is 255, and MSE is the Mean Square Error defined as follow:
On the other hand, the SSIM[25] [26] is used to measure the similarity between two images with respect to 3 factors which can be expressed as:
from which:
l is the brightness between two images comparation
c is the contrast distortion, which differs the brightest and darkest ranges
s is the correlation loss, it compares the pattern of local luminance
The luminescence distortion, contrast distortion and correlation loss can be expressed separately as:
If the value of SSIM is close to 1 it is concluded that the original image and the recovered image are structurally similar.
The results obtained by implementing the proposed method are shown in Table 2.
Table 2 Imperceptibility results.
| PSNR | SSIM | |
|---|---|---|
| Cover Image 1 | 94.6233 | 0.9876 |
| Cover Image 2 | 94.600 | 0.9875 |
The proposed method was applied to the rest of the medical images using only the cover image 1, the PSNR and SSIM tests were performed, the values obtained are shown in Table 3.
Table 3 Visual quality results in terms of PSNR and SSIM.
| DICOM images ID | PSNR | SSIM |
|---|---|---|
| 1 | 94.6233 | 0.9876 |
| 2 | 94.5824 | 0.9843 |
| 3 | 94.5699 | 0.9867 |
| 4 | 86.5022 | 0.9898 |
| 5 | 89.7878 | 0.9884 |
| 6 | 86.4916 | 0.9896 |
| 7 | 92.3604 | 0.9885 |
| 8 | 89.7604 | 0.9876 |
| 9 | 92.3575 | 0.9891 |
| 10 | 86.9698 | 0.9874 |
| Average | 90.8005 | 0.9879 |
| DICOM images ID | PSNR | SSIM |
In the same way, Figure 14, shows some results of the tests performed, on the left the original images and on the right the reconstructed images, where at first sight they do not present any alteration now of being recovered by the receiver.
Table 4, compares the PSNR obtained from the original medical image and the encrypted image with the results obtained by implementing the proposal of Richa and Ashwani [16]. In this case, a minimum value of PSNR is expected since it ensures that the original medical image and the encrypted image are no correlated and as can be appreciated our results obtain lower values, inferring that the correlation between the two images is lower with the results previously published.
Table 4 PSNR (dB) of original images vs encrypted image.
| DICOM Image ID | Proposed method | Richa [(21)] |
|---|---|---|
| 1 | 56.1543 | 56.4547 |
| 2 | 56.0163 | 56.2816 |
| 3 | 56.4283 | 56.6693 |
| 4 | 52.4912 | 52.6509 |
| 5 | 52.3014 | 52.4326 |
| 6 | 51.4581 | 51.5942 |
| 7 | 51.0167 | 51.2845 |
| 8 | 50.6105 | 50.8029 |
| 9 | 50.0141 | 50.1966 |
| 10 | 50.8472 | 50.9351 |
Although Richa only evaluates in terms of PSNR, based on the contributions presented here, it is possible to have a very detailed comparison of the processes performed, for example, Richa considers medical images with a depth of 8 bits and 3 cover images, expanding them to have a greater hiding capacity. On the other hand, the methodology proposed in this paper allows hiding medical images up to a bit depth of 12 bits and adding the metadata, only one cover image is considered without expanding it and finally a way to verify the integrity of the file sent by a HASH function is included, adding value to the results obtained.
CONCLUSIONS
The proposal provides a way to embed a medical image, as well as its respective metadata in the RGB channels in an identification patient’s image. Allowing medical institutions securely share the DICOM file to preserve its integrity. For this purpose, stenographic and cryptographic techniques were combined, which proves to increase the security of conventional methods as supported in the previous research, making tough the information retrieval by malicious users.
On the other hand, the proposed method allows working with medical images with a bit-depth of more than 8 bits/pixel and incorporates the metadata, allowing a greater capacity to hide data within the color image, compared to the methods already proposed, because these methods only work with medical images with a bit-depth of 8 bits/pixel and without considering the metadata hiding.
The fact of using an ID image allows the medical institutions in responsible for delivering and evaluating the medical images to verify at a naked eye that the face of the person in the ID image corresponds to the actual patient receiving the studies, thus allowing the study-patient linkage.
Finally, experimental results prove that the proposed methodology allows the resulting image (ID image with the hidden medical data) in comparison with the original image, to have changes in tonalities that are the least perceptible to the human eye, in addition to providing an outstanding level of medical image recovery in terms of visual quality and similarity as demonstrated in the resulting PSNR and SSIM tests.
As part of future work this methodology is proposed to be applied to other color models to increase the level of security and to make it more difficult to obtain the data embedded in the cover image as well as to improve the resulting visual quality. On the other hand, it is considered to implement it in other medical imaging modalities as well as its application to 3D medical imaging.











 nueva página del texto (beta)
nueva página del texto (beta)