1 Introduction
The difference between steganography and cryptography is that the last one encrypts the files keeping the original file visible, however, when opening it, it will show a sequence of characters that do not allow its reading, and to access its original content it is necessary to know the key with which it was encrypted. In steganography, a file has a different format, and to know its original content it is necessary to know the key and the software with which it was hidden [1].
This area has attracted a lot of interest in recent years, especially in the area of computer security, because it has been used by criminal organizations for terrorist purposes. However, this is nothing new, as it has been used since ancient times, and has traditionally been used by police, military, and intelligence institutions, who want their information to travel securely and unnoticed by any curious onlookers [2].
The work presented in this paper makes use of steganography, which can be illustrated through the example of the Prisoner’s Problem where the following situation arises: How should two prisoners communicate to agree on an escape plan if they are in separate cells and all messages they exchange must pass through a guard? This scenario has the characteristic that pure cryptography cannot be used since it arouses the guard's suspicion, and he will not pass the message. As it was mentioned before, encrypting messages only hides the meaning, but not the existence of the message. If the guard notices that there is a message, even if he cannot understand it, he will immediately suspect the prisoners; the messages must appear innocuous. Only then will the guardian pass the message among the prisoners without realizing that they are up to something, and, at the same time, the scheme must be pre-agreed among the prisoners, so that they can decipher the message [3].
This paper presents the communication of a message embedded in sound, which constitutes Steganography, such a message will be handled by audio. Steganography is considered as the technique of hiding information in the presence of the adversary using various carriers.
2 Mono and Stereo Sound
2.1 Mono Sound
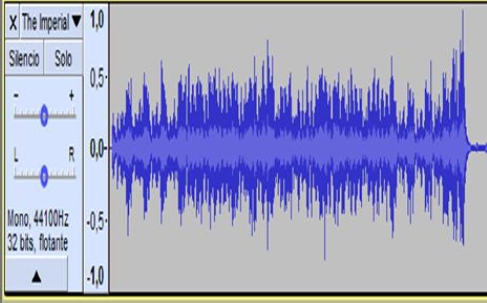
A monophonic signal is a signal recorded with one microphone. When listening to the recording with two speakers or headphones, the signal is duplicated and we hear the same on both sides [4]. When recording a voice with a single microphone, we will record it on a mono track of our recording program, which can be seen in Figure 1.
2.2 Estereo Sound
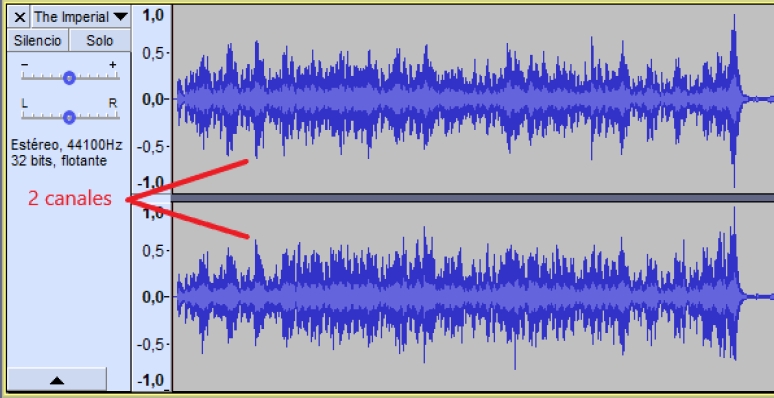
On the other hand, a stereo signal is a signal recorded with a "stereo pair" (a pair of two equal microphones). When listening to the recording, we hear the recording from one microphone on the left and the other on the right [5]. When recording an ambiance, the difference between mono and stereo is noticeable considerably. A stereo recording is much more realistic as humans hear everything through both ears.
When we record an acoustic drum, we use a stereo pair (aerial) to capture the cymbals and a bit of atmosphere (see figure 2).
2.3 Phase in Sound
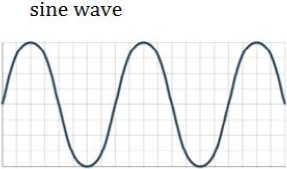
The most important thing to know about phase is that it is a relationship between two sounds, so if we only have one signal (one cable, one microphone, one channel), there is no phase [5,6]. To illustrate this, we will use a simplified sound: we will use a sine wave, a sound as simple as the tone produced by the telephone while we are waiting for a signal. It is a wave that repeats itself without change, with its peaks and valleys always at the same distance from each other as shown in figure 3.
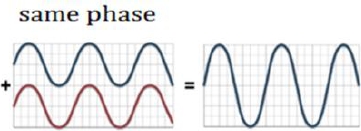
If we have two equal waves and we mix them, we will have a resulting wave with twice the volume, then we will say that the phase of the two initial waves was the same, that is, the peaks of one coincided with the peaks of the other, and the same it happened with the valleys (see figure 4).
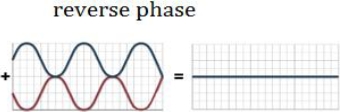
But if we delay half a wave in one of the two signals, and we make the peaks of one coincide with the valleys of the other, we will have that when we mix them the result will be silence. We will say that the phase between these two signals is inverse, or that one has the phase inverted with concerning the other.
Initially, their sounds heard separately, are still the same as before, having delayed one of the waves has not changed its sound; however, when listening to them together their intensities have been canceled by having the phase reversed, as shown in Figure 5.
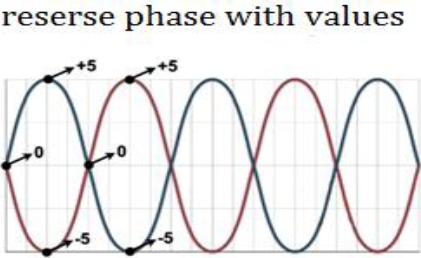
If we assign a value of 0 to the vertical center point of the waves, and we assign fixed values to the peaks and valleys, for example, +5 and -5, respectively, we will get that the peaks of a signal have a value of 5 and match the valleys that have – 5. When mixing the waves we will have a cancelation, as we see from the result 5 – 5 = 0. The same happens for the valleys of the first wave matching the peaks of the second one. Each wave point matches another point in the other wave with the same value, but with an opposite sign. The result is always zero (see Figure 6).
The phase can be measured in degrees or radians as if they were angles: in the first example the two waves had the same phase, therefore, the difference between them was 0º. In the second example, the waves canceled each other because they had a phase difference of 180º, half a wave. An offset with a value of 180º is as different as two equal waves can be. If we add two waves with a phase difference of 90º between them, a more complex wave than the initial ones will be produced, they will only cancel each other at some points, and at others, and the amplitudes will be added [5, 7, 8].
3 Hiding Audio Messages by Phase Reversal and Using Audacity
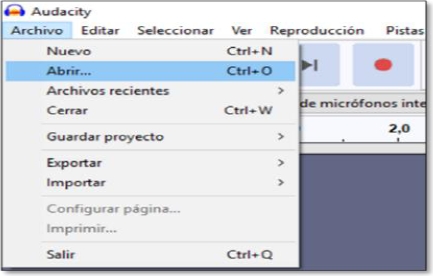
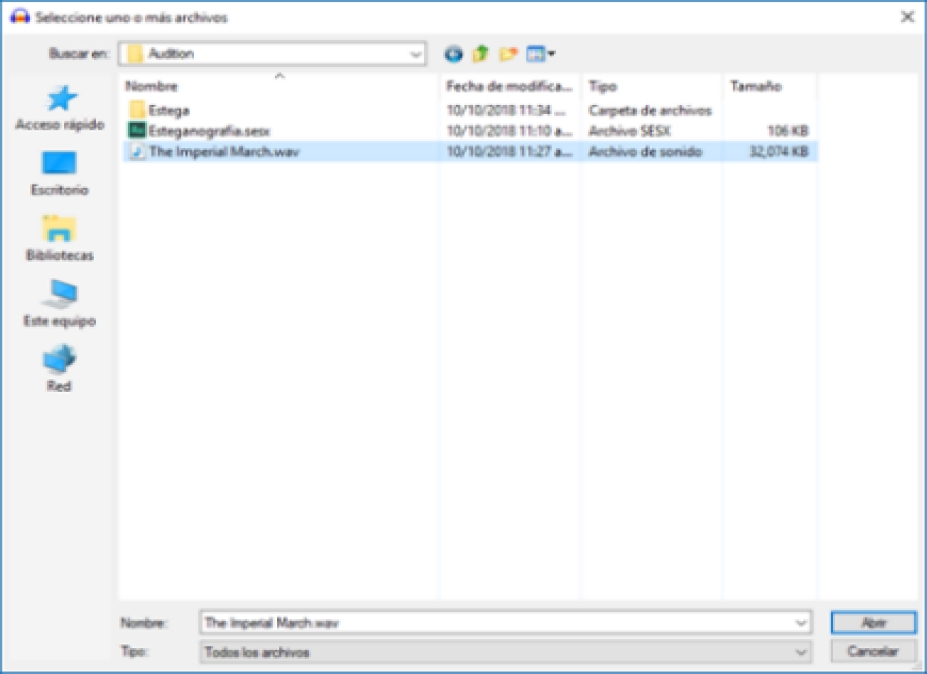
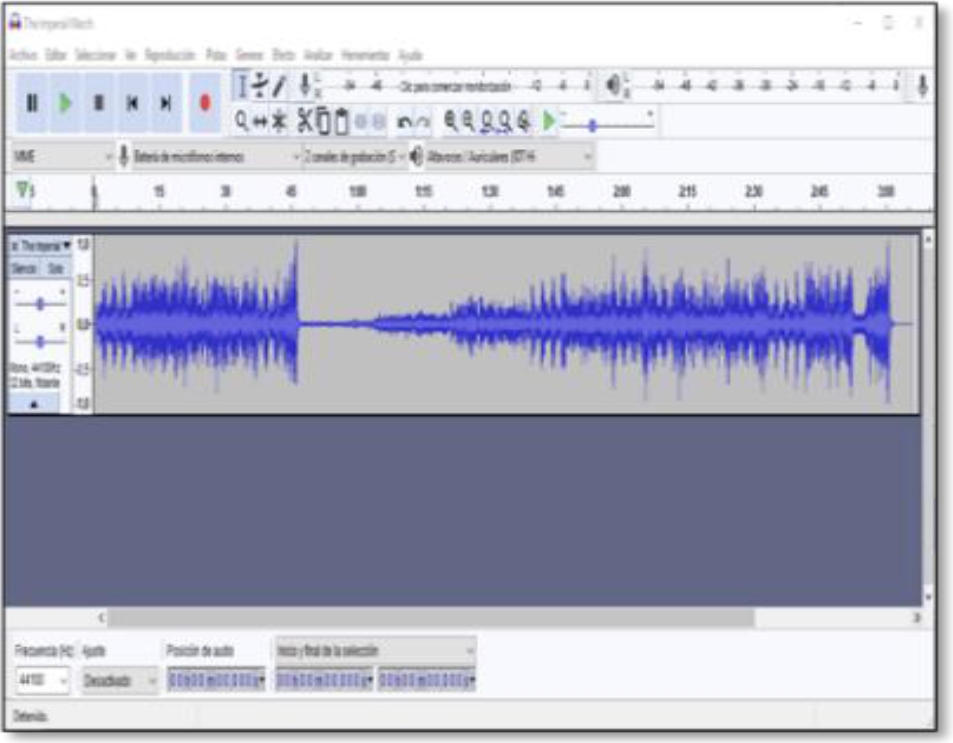
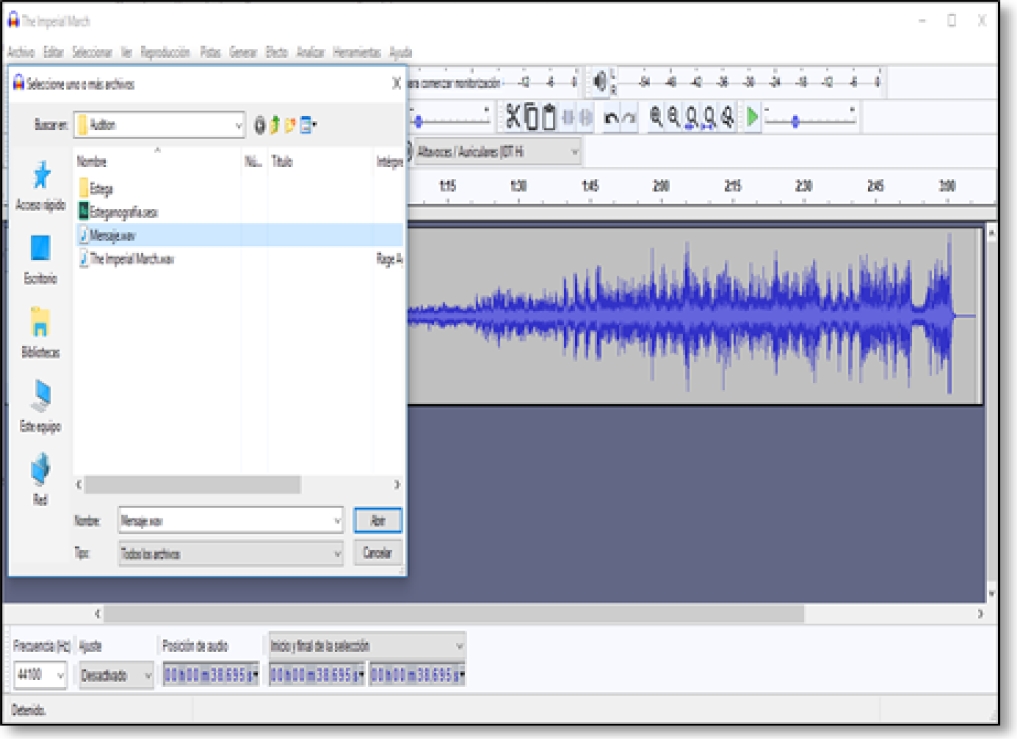
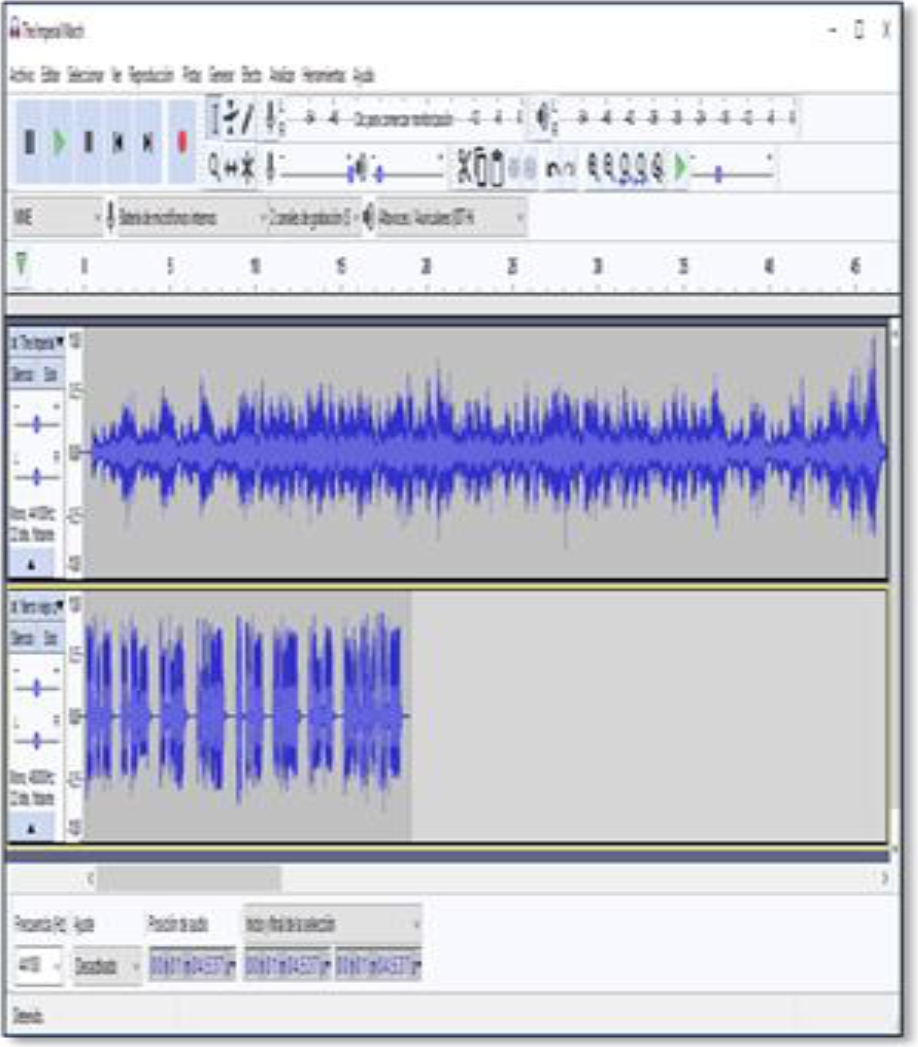
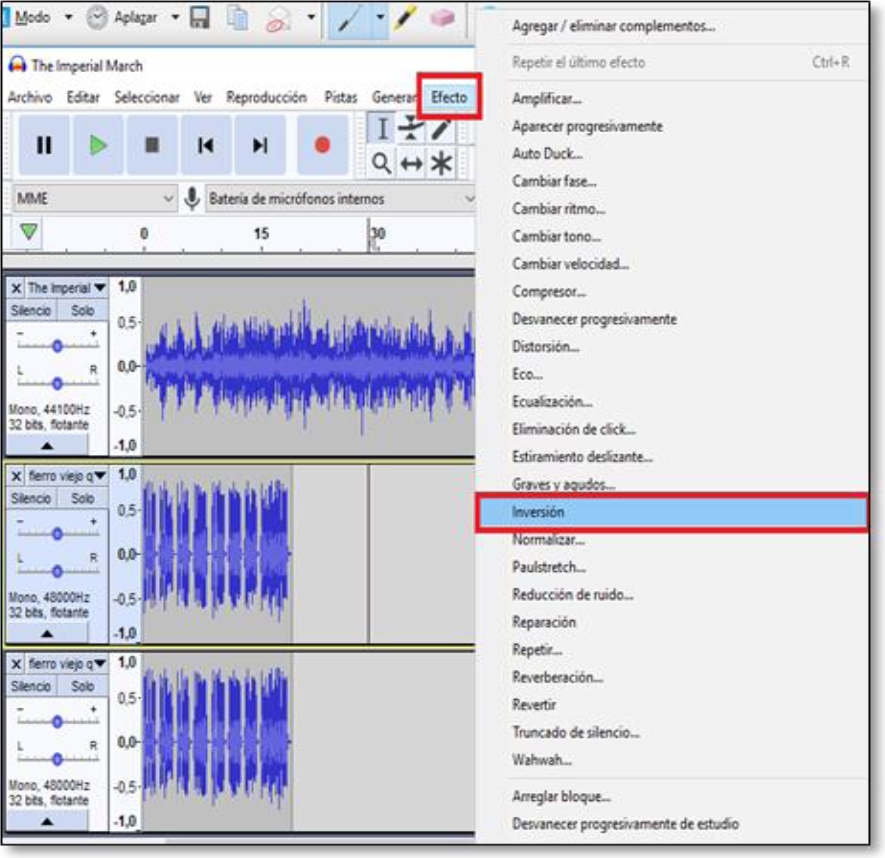
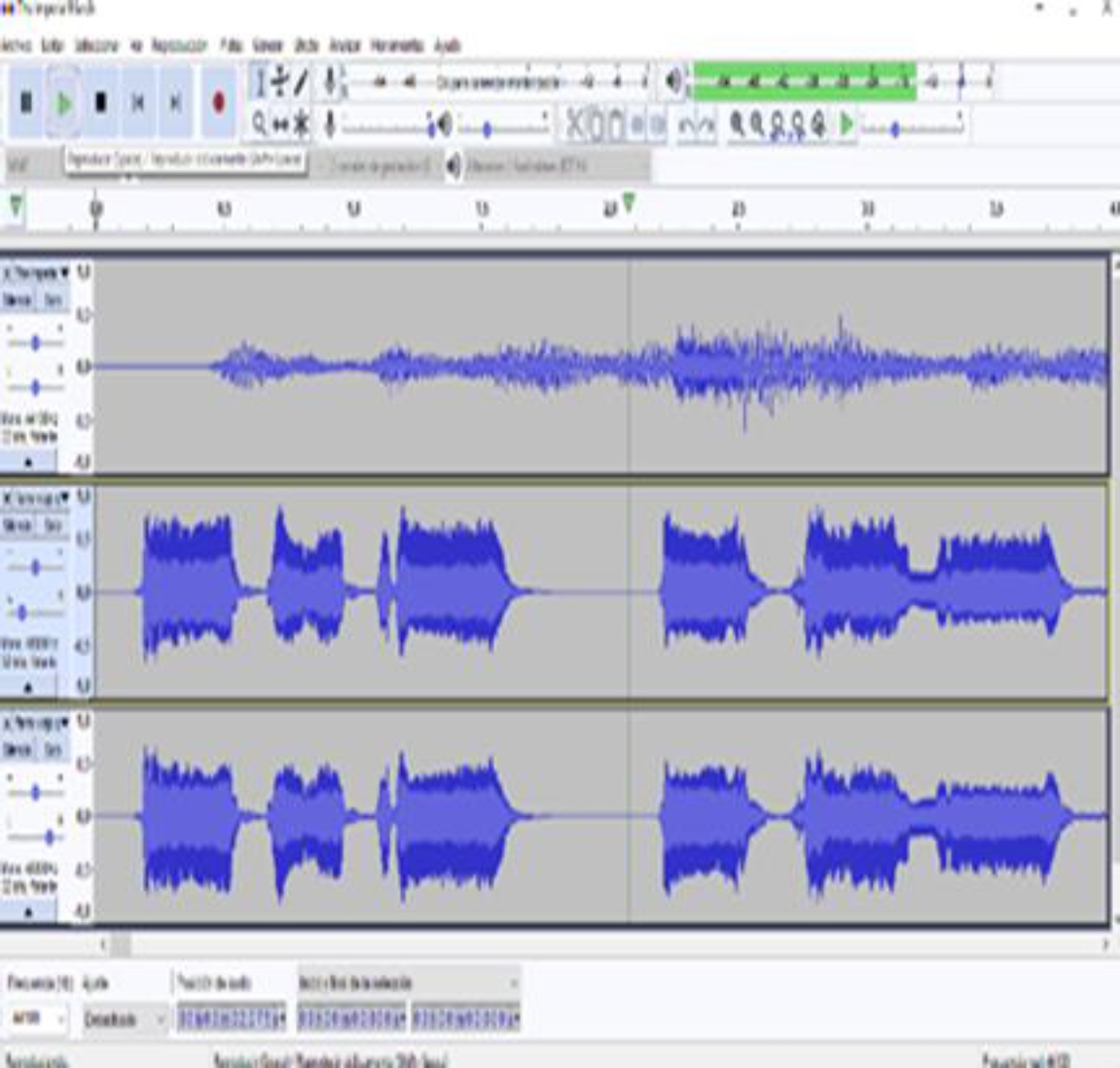
In the File menu we select Open and then a dialog window is displayed to select the file (see figure 7). We choose the file The Imperial March.wav which contains a single audio channel (mono), which will serve as background to hide the message (see figure 8). This window will display the selected file and show its waveform (see figure 9). Next, we add another audio track which will be our message to hide (see figure 10). The file Message.wav also contains only one audio channel (mono). When playing both tracks the two audio channels will be mixed and we will be able to distinguish between one and the other [9,10]. We need to duplicate the second track to be able to apply the inversion, to do this, simply repeat the previous step and the track will be added again, but this time in another channel as shown in figure 12.
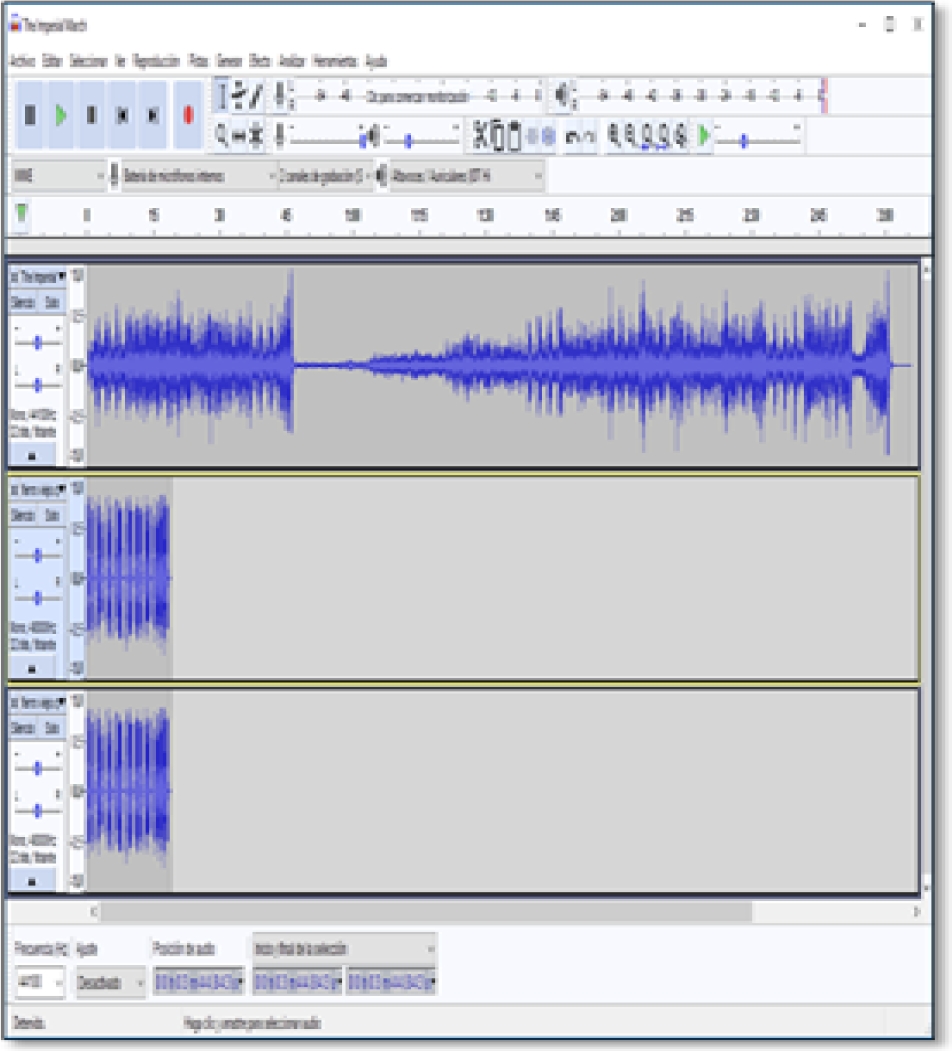
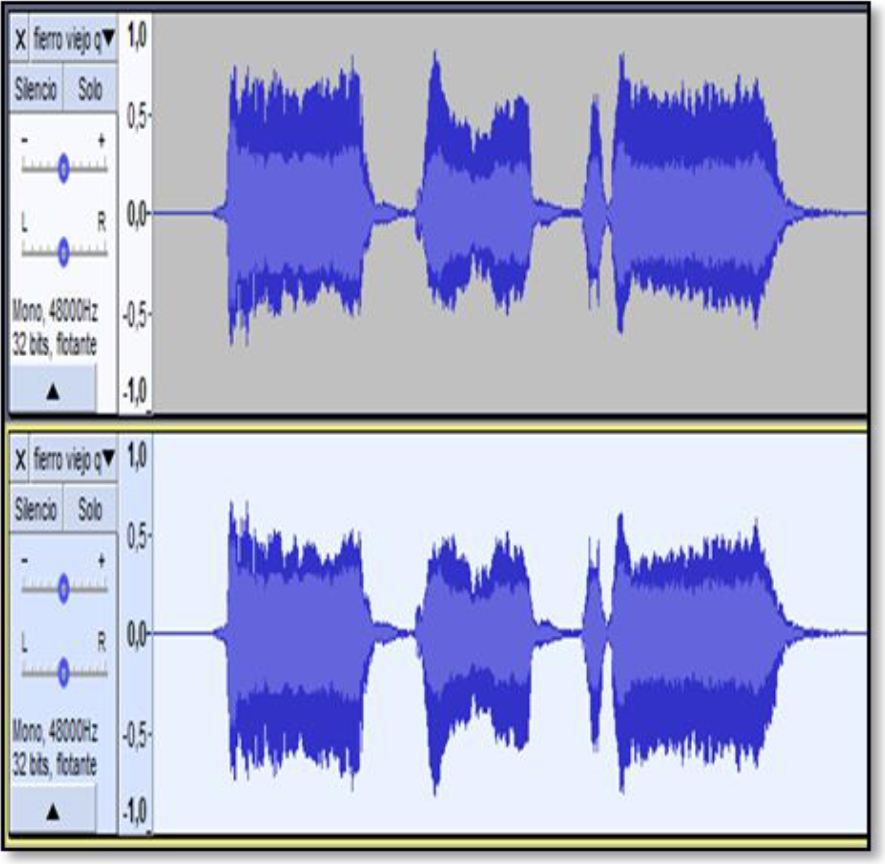
Then, we select the third track and in the effect menu we apply the Inversion option (see figure 13). When applying the inversion effect we notice how the waves of the third track are inverted (see figure 14).
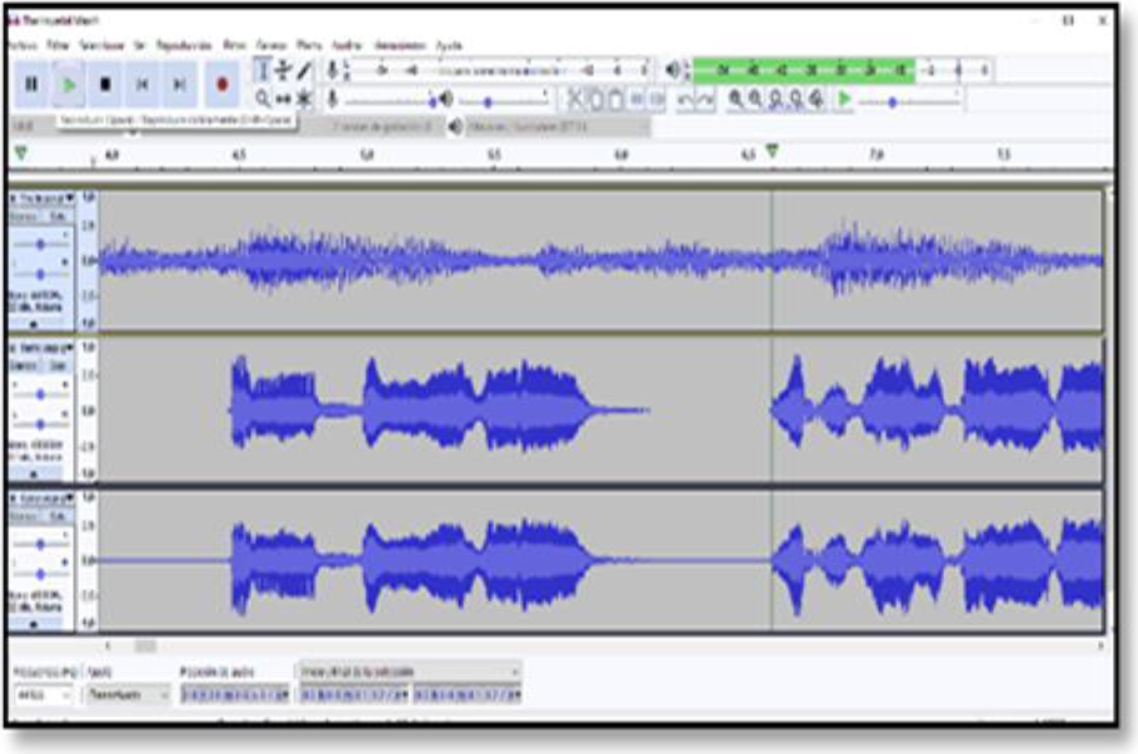
Therefore, when playing the complete project, only the background track will be heard, since the second and third tracks will enter in the reverse phase case and when the values of both tracks are added together they form a plane wave as explained above [11,12]. (See figure 15).
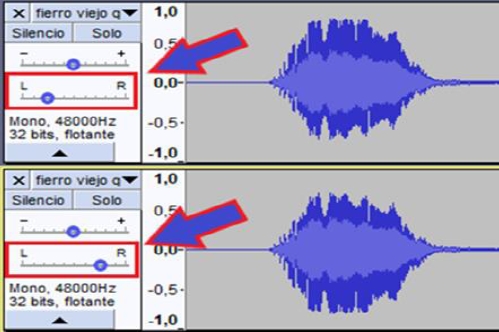
To listen to the message in a stereo system, it is enough to assign values to the left for the second track and values to the right for the third track (see figure 16). When playing it back, we will again be able to hear the background track together with the message, but we will only be able to distinguish the message in a stereo system, as shown in figure 17.
4 Conclusions
If we export the hidden message as an mp3 file and play it on a system that has mono sound, like most cell phones, tablets, and current pocket players, we will not be able to hear the message that we have hidden, therefore it will travel safely because, since the channels are mixed, this message cannot be played. This allows the message that we hide by this technique to travel safely through mono sound devices. To retrieve the message it is necessary to pass the information from a mono device to a stereo device.











 nueva página del texto (beta)
nueva página del texto (beta)