1 Introduction
The reality of modern technology has changed the landscape of digital multimedia and created unexpected problems related to the security of sending and sharing data in the cyber world.
The number of theft cases in the cyber world makes the security of data a matter that needs special attention [–3]. One way to secure data is by cryptography. Cryptography is the science of data encoding to secure the data. In this way, the encoded data will change in form and meaning so that it cannot be read directly [4, 5]. The encoding process is called the encryption process, while the process to restore data is encoded into the original data decryption process. Both of these processes are the main processes in cryptography [6].
Various digital files can be used as objects to be coded with cryptographic methods in previous studies. Digital images are one of the most favorite objects used in cryptographic research today [7, 8], so did in this study used a digital image as an object for study. Many cryptographic methods have been applied to images such as scramble, stream and substitution methods. The scramble method is also often called the permutation or diffusion method[9] where, algorithms that are popular in this method are Chaotic Map [5, 10]. While the algorithms that are widely used in substitution methods are one-time pad (OTP), Vigenere, Hill cipher, etc. [1, 11, 12]. Some modern cryptographic methods are also applied in image encryption such as DES and AES [13, 14].
But in research [15, 16] it is said that the AES and DES methods are not suitable if implemented on the image due to some physical features of the image such as bulky data capacity, high redundancy and strong correlation between pixels. In a comparative study conducted by [17], it was stated that the scrambling method has advantages in diffusion and confusion properties, but this method is quite slow to compute especially if it has a large number of iterations. The lack of a scrambling method also produces the same image histogram as the original image. Whereas OTP has advantages in the results of image encryption based on several measurements such as entropy analysis, the unified average change in intensity (UACI), the Number of Pixel Change Rate (NPCR), Peak Signal to Noise Ratio (PSNR), and Structural Similarity Index (SSIM) and has faster computing processes.
OTP is a substitution cryptography algorithm also known as Vernam cipher. This algorithm uses XOR or modulo operations as its main operation [1]. Vernam algorithm is the development of the Vigenèrecipher algorithm that uses random keys in the process of encryption and decryption. The Vernam algorithm is strong against attacks and difficult to decrypt. But the toughness of this algorithm depends on the key used. In order to obtain encryption, the strong key must be completely random, only used once, and only known by the sender and receiver. Because the algorithm that has a simple, fast and powerful operation makes this algorithm much developed [18]. One of the algorithms derived from Vigenèrecipher is Beaufort cipher. Subtraction operations are carried out in the encryption and decryption process in Beaufort cipher, which distinguishes them from Vigenèreciphers [19]. To improve security, this study proposes a cryptographic method by modifying the modulus-based substitution cipher to hybridize the Vigenèreand Beaufort algorithm with two random keys followed by the chaos method.
2 Literature Review
Cryptography is a science that has been carried out to secure secret messages from ancient times until now. The substitution method is a cryptographic method that encrypts by changing the meaning and content of the message based on the key value. In the substitution method, the key will have an important role in the strength of the encoding, the better the key the stronger the results of encryption.
Vigenèrecipher is one of the cryptographic algorithms that applies the substitution method and was very popular in its time. Vigenèrecipher uses tabula recta tables for the encryption and decryption process, then was developed by Gilbert Vernam by modifying the use of keys, where the key used is random, then also known as Vernam cipher [1, 20]. Because the quality of this method is very dependent on the key, the use of random keys has better performance and is harder to solve. The Vernam cipher formula for the encryption process can be seen in formula (1) and for decryption, it can be seen in formula (2):
Beaufort cipher is a modification of the Vigenèrecipher that uses a subtraction operation as its main process [19]. The formula used in Beaufort cipher has similarities with Vigenèrecipher. The similarity between the two techniques is the use of the modulo function and the type of key used. The difference between these two algorithms is the key role, in the Vigenèrecipher, in the encryption process, the key is used as a plain text enhancer, whereas in the decryption process, the key is used as a subtraction of the ciphertext. Whereas in Beaufort cipher, the key used for the reduction operation is the encryption and decryption process. For more details, the Beaufort cipher encryption formula can be seen in Eq. (3) and decryption formula in Eq. (4):
Another cryptographic method that is popularly used today in image encryption is the scrambling method, one of the popular algorithms of this method is the Arnold Chaotic Map (ACM).
This method is widely proposed for cryptography in images, because of its superiority against differential attacks. ACM can provide an efficient combination of the properties of confusion and diffusion. The scramble method differs from the substitution method, the encrypted image scramble method does not change the pixel value, only the randomness of the pixel is performed by a certain formula [21, 22].
This method has a sensitivity to the initial state and has ergodicity property so that it is strong against certain security conditions [5]. To encrypt images with ACM you can use Eq. (5), while the decryption process can use Eq. (6):
where 𝑥 and 𝑦 are the pixel coordinates, 𝑥’ and 𝑦’ are the new pixel coordinates, 𝑘 and 𝑙 are positive integer numbers, 𝑊 is the length or width of the image, where the length and width of the image must be the same.
For the record, Eq. (5) and Eq. (6) done in one iteration or one Arnold period. Iteration can be done several times as needed.
3 Proposed Method
The cryptographic method consists of two main stages, i.e encryption, and decryption. The proposed method uses a hybrid method of the Vigenèrecipher and Beaufort cipher algorithm which has been modified using two random keys. Then proceed with encryption using ACM to get the final cipher.
The stages in the encryption process can be seen in Figure 1. Based on figure 1 can be explained in more detail with the steps in the encryption process as follows:
1 Read the image as input, then save the image in a variable 𝐼.
2 Get the dimensions of the 𝐼 image and save it into variable 𝑚, 𝑛, 𝑜, where 𝑚 is the width, 𝑛 is height, and 𝑜 is the image layer (RGB).
3 Create a matrix with dimensions (𝑚 × 𝑛) then fill with random numbers in the range of 0 to 255 using a random generator, save this matrix as the first key (𝑟𝑘𝑒𝑦1).
4 Create a second matrix with dimensions (𝑚 × 𝑛) then fill with random binary numbers using a random generator, then save this matrix as the second key (𝑟𝑘𝑒𝑦2).
5 Perform hybrid encryption using formula (7):
As for the stages of image decryption, see Figure 2 below. Based on figure 2, it can be explained in more detail with the steps in the decryption process as follows:
Read the encrypted image, save the image in variable 𝐸.
Get the dimensions of the 𝐸 image and save it to 𝑚, 𝑛, 𝑜, where 𝑚 is the width, 𝑛 is height, and 𝑜 is the image layer (RGB).
Descramble the matrix 𝐸 with Eq. (6) for each layer.
Read the first random key (𝑟𝑘𝑒𝑦1) and the second random key (𝑟𝑘𝑒𝑦2).
Perform decryption using Eq. (8), based on both random keys.:
4 Results and Discussion
A standard image dataset in the RGB (24-bit) channel format is used at this stage. This image is a standard testing image for digital image processing which can be downloaded on the SIPI image database page [23]. Figure 3 presents some sample images used for the images used in this study. After the image is downloaded, the image is used directly as a dataset to be tested on the proposed encryption method. All images do not undergo preprocessing, so the pixel values, dimensions, and image extensions are the same as the original version. This is done so that it is easy to compare with subsequent research. All images used have dimensions of 512 × 512.
The first step before starting the encryption process is to create two random keys. Create two random keys according to the dimensions of the image to be encrypted, for more details see steps 3 and 4 of the method proposed in section 3. Figure 4 is an example of a random key generated by a random generator and tested in this research.
The first random key is a grayscale image (8-bits) and the second random key is a binary image. Next, use the two random keys for the encryption process using formula (7). The encryption results were then randomized again using ACM with the formula (5) so that the encrypted image is generated. The results were then tested for encryption quality using several measuring devices such as entropy, MSE, PSNR, SSIM, UACI, and NPCR. Entropy (H) is a feature that is used to measure the randomness of probability (p) encrypted images that can be decrypted [24]. Entropy can be calculated by the formula (9):
MSE, PSNR, and SSIM are used to measure the quality of image encryption based on errors, noise, and structural changes in the image. Formulas (10, 11, 12), each of which is used to calculate MSE, PSNR, and SSIM. UACI and NPCR are used to measure the encryption strength of differential attacks [24, 25]. Where the formula used to calculate UACI and NPCR is shown in formulas (13, 14):
where 𝐸 is an encrypted image, 𝐼 is the original image, 𝑚 is the image width, 𝑛 is the image height, and 𝑜 is the number of layers, 𝜎𝐸𝐼 is the image covariance 𝐼 against 𝐸;
The measurement of encryption quality is shown in table 1 and table 2. In table 1 there are several measurement results such as Entropy, MSE, PSNR, and SSIM, then in table 2, there are NPCR and UACI. The entropy value produced from the whole image is very good because the entropy produced is close to 8 (maximum value) [17]. Based on the entropy value, it can be concluded that the encrypted image will be very difficult to decrypt without knowing the key used. Visually encrypted images also show very significant changes when compared to the original image, there is no correlation or meaning related [26].
Table 1 Image Encryption Measurement (Entropy, MSE, PSNR, SSIM, Time)
| Image Name |
Entropy (Red) |
Entropy (Green) |
Entropy (Blue) |
MSE | PSNR | SSIM | Time (seconds) |
| Airplane | 7.9993 | 7.9992 | 7.9992 | 10363.3117 | 7.9758 | 0.0005 | 2.196500 |
| House | 7.9992 | 7.9992 | 7.9993 | 11200.3896 | 7.6385 | 0.0006 | 2.020584 |
| Lena | 7.9994 | 7.9993 | 7.9993 | 11215.9747 | 7.6324 | 0.0007 | 2.289976 |
| Mandrill | 7.9994 | 7.9993 | 7.9992 | 10106.1305 | 8.0850 | 0.0004 | 2.261854 |
| Sailboat | 7.9993 | 7.9994 | 7.9993 | 11222.3829 | 7.6300 | 0.0009 | 2.194902 |
| Splash | 7.9993 | 7.9993 | 7.9993 | 11231.1979 | 7.6265 | 0.0004 | 2.325276 |
Table 2 Image Encryption Measurement (NPCR and UACI)
| Image Name | NPCR | UACI | ||||
| Red | Green | Blue | Red | Green | Blue | |
| Airplane | 99.6174 | 99.6178 | 99.6258 | 31.9945 | 33.1712 | 32.7779 |
| House | 99.5952 | 99.6155 | 99.6025 | 30.2055 | 31.3364 | 31.2868 |
| Lena | 99.5956 | 99.6223 | 99.6227 | 32.9805 | 30.5929 | 27.6362 |
| Mandrill | 99.6311 | 99.6318 | 99.6150 | 29.9489 | 28.7772 | 31.8353 |
| Sailboat | 99.6140 | 99.6204 | 99.5899 | 27.9453 | 34.3163 | 34.3236 |
| Splash | 99.6177 | 99.6021 | 99.6288 | 34.2339 | 35.6784 | 31.9677 |
This is evidenced by a large MSE value and a very small PSNR value, the square of the error is very high so that it directly impacts the amount of noise that distorts the image. The image structure also changed significantly, which is indicated by an SSIM value close to 0. Besides the combination of hybrid substitution and scrambling methods with ACM produces ideal UACI and NPCR values, so it can be concluded that the encryption results are also strong against differential attack attacks.
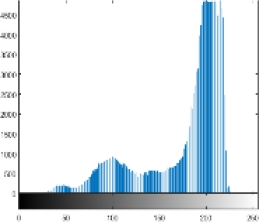
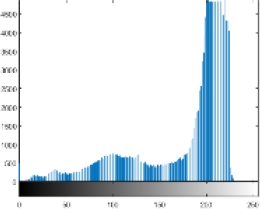
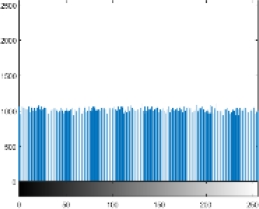
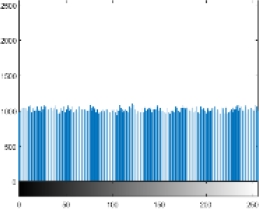
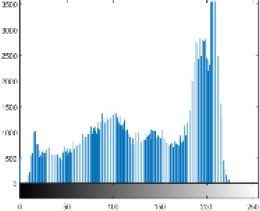
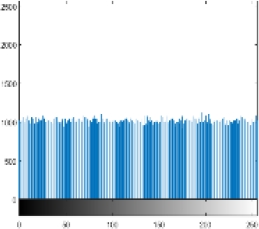
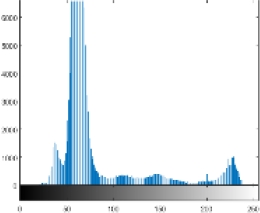
Other tests are also carried out, i.e. the computational time needed. The tic toc function on Matlab R2015a is used as a measurement tool, based on the measurement results it takes about 2 seconds for encryption and decryption of each image tested in this research. As a note in this research used hardware with specifications: AMD A12 7th processor and 4GB RAM. Of course, this performance is relatively very fast and relevant if later implemented in a real application. The last test conducted was a histogram analysis. This test has an important role in knowing how much the encryption strength of images against statistical attacks [24, 25]. Table 3 presents a comparison of the histogram of the original image and the encrypted image if the histogram is observed from the encryption results all images have a similar form. It seems that the value of each pixel has almost the same intensity or uniformity.
Because the better the quality of encryption, the histogram will show a more uniform intensity of values across all pixels. The distribution of pixel values will also be more evenly distributed across all values in the range of 0 to 255, [1, 17].
Figure 5 shows a sample of the results of the encryption process that has been applied to the original image. Visually, the image encryption process is very random and does not correlate with the original image.
The next step is testing the image decryption process. At this stage, it can be done without any errors so that the decrypted image has a value that is the same as the original image.
To measure the results of decryption, MSE, PSNR, and SSIM are measured. Besides, computational performance is also measured using the decryption algorithm with the tic toc function in Matlab. The results of measuring the decryption process are shown in table 4.
The results shown in table 4 show that the decryption process can be done well without any errors. This is evidenced by the value of MSE = 0, which means that there is no single error in the reconstruction of the decrypted image. PSNR value = inf, this means there is no noise entering the image. The SSIM value is also equal to 0, this shows that the similarity of the image structure is encrypted with the original image. The time needed for the decryption process is also almost the same as the extraction process, which is about 2 seconds
After measuring the quality of encryption, and the performance of the proposed method. Furthermore, a comparison of the results was carried out with some research on image encryption that had been published previously. Comparison is done based on several measuring devices such as entropy, NPCR, and UACI. Some research that is used as a comparison is [ - 29], where the comparison is done with the same image dataset, namely Lena's image, the comparison is presented in Table 55 Conclusion.
This study proposes a combination of the substitution and scramble encryption method by hybridizing the Vigenère and Beaufort algorithm combined with ACM encryption. Hybrid is done by using modulus operations and two random keys. The encryption results from the hybrid substitution method are then encrypted again using ACM to get multiple layers of protection. The aim is to improve image security.
To measure the quality of encryption, several tests are carried out, such as entropy analysis to measure the randomness of images and decrypted probabilities, histogram analysis to measure the strength of encryption from statistical attacks, UACI and NPCR to measure unawareness of differential attacks. Besides that, the level of error, noise and structural changes in the image were also measured using MSE, PSNR, and SSIM to determine the level of image randomness visually. All measurement instruments show that the proposed encryption method is of very good quality. Likewise, the decryption process can work well without errors which can change the meaning of the original image.
When compared with some of the previous methods presented in Table 5 it appears that the UACI and Entropy values of the proposed method are superior, even though the NPCR value is still not more effective and can be used as something that should be improved in further research. This method also has relatively simple and fast but powerful computing against various attacks, so it is very relevant if it will be implemented in various applications.
Table 5 Comparison with the previous method based on NPCR, UACI, and Entropy
| Measurement Tools | Ref [27] | Ref [28] | Ref [29] | Proposed | |
| NPCR | Red | 99.6475 | 99.6836 | 94.6836 | 99.5956 |
| Green | 99.6231 | 99.6836 | 95.6836 | 99.6223 | |
| Blue | 99.5941 | 99.6810 | 98.6810 | 99.6227 | |
| UACI | Red | 33.5328 | 33.4647 | 33.4647 | 32.9805 |
| Green | 33.2752 | 33.5048 | 34.5048 | 30.5929 | |
| Blue | 33.4394 | 33.4999 | 35.4999 | 27.6362 | |
| Entropy | Red | 7.9808 | 7.9992 | - | 7.9994 |
| Green | 7.9811 | 7.9992 | - | 7.9993 | |
| Blue | 7.9814 | 7.9991 | - | 7.9993 | |











 text new page (beta)
text new page (beta)