1 Introduction
Society, per se, refers to a set of people who interact among themselves according to both judicial and moral laws with the goal of achieving a certain level of general well-being and collective development. However, divergence and atomization of interests among members of the same society causes various types of problems that negatively impact society’s desired well-being and development, for example, unemployment, health crises, kidnapping incidents, etc.
One of the main problems in Ecuador is the forced disappearance of individuals, especially vulnerable people such as children, adolescents, people with special needs, and senior citizens [1]. Under Ecuadorian law, kidnapping is considered a felony, since it violates human rights such as the personal liberty and physical and moral integrity of those affected, meaning not just those of the kidnapping victim but also those of family members and acquaintances [1].
In addition, victims of forced disappearance often repeatedly relive the traumatic sensations experienced during the attack, and suffer psychological problems such as loss of self-esteem, anguish, PTSD, etc. [2].
Kidnapping is not only a problem in Ecuador; it is also a problem in all of Latin America. The rate of forced disappearances of minors is alarming; it is linked to context, that is, the socio-economic conditions of each country. For example, in Mexico from 2005 to April, 2017, 5,865 minors younger than 17 years old were reported as missing [3]. In Guatemala, a 2006 statistical survey indicates that 6,005 minors disappeared [4]. In Colombia, where armed conflict has worsened the situation, 8,000 children have disappeared from 1985 until now [5].
The figures for Ecuador are equally disturbing. For the period from 1970 to 2017 [6], the number of missing persons reached 42,484. Monthly, an average of 500 reports are filed related this problem [7]. In Ecuador, Quito is the city registering the majority of occurrences [6]: 34% of the total amount of missing persons reported [8].
Between 2014 and 2017, there were 17,230 total missing person cases [7], of which 59% involved women. In addition, Ecuador’s Attorney General’s office [9], has reported that for the years 2013 and 2014, there were 18,681 total cases of missing persons, of which 67.71% involved minors.
To conclude, the disappearance of people in Ecuador, as well as in Latin America as a whole, is an alarming problem that demands a prompt and effective solution.
Since 2013, Ecuador has used an integrated security system called ECU-911 [10]. It was implemented in order to provide a solution to emergencies reported by citizens, such as searches for missing persons. ECU-911 uses a video surveillance system as its main tool in combatting the problem of missing persons.
This tool allows responders to track missing persons with security cameras installed throughout the city. It pinpoints their last known location and sometimes offers other clues regarding their last known whereabouts. However, the number of cameras deployed is too small to cover the entire urban area, much less the rural surroundings. In addition, in order to report an emergency and access ECU-911 services, citizens must dial the 911 emergency number, give their account of the incident, and the responder must direct the information to the solution providers.
This type of communications media does not support a multimedia exchange of information that includes photos or video that may help track or locate those involved in potential kidnappings. It also significantly lengthens the time needed to locate and recover any victims. It is important to keep in mind that time is the crucial factor in recovering missing persons.
The risk to the victim, including physical and psychological harm, increases exponentially in relation to time passed. For example, we should mention the case of a girl who was kidnapped in Loja, Ecuador [11], who died several hours after her kidnapping. This fatal incident could have been avoided by using a more effective search and location tool.
This article presents the QSSC (Quito Smart Safe City) solution. It describes a prototype for an alert and location system for missing persons, and uses Quito for its case study. It proposes the use of an innovative information distribution system that integrates agents of the National Police Force, who are responsible for responding to cases of missing persons, with the local community.
This system uses state-of-the-art technology, such as Cloud Computing [12], mobile applications [13] and IoT (Internet of Things) communications protocols, along with MQTT (Message Queuing Telemetry Transport). It thus takes advantage of the ubiquity of smartphones within the city’s current technology environment [14].
This article is divided into five sections. The Introduction describes the social context of the problem under study. It presents statistics that show that forced disappearances are a daily problem that requires an effective and economic solution tailored to the Latin American reality.
Second, the State-of-the-Art section reviews several similar projects around the globe that mitigate the problem of missing persons. It offers a comparative perspective on the issue.
Following that, the article presents a detailed proposal of the distributed system, including how IoT concepts [15], crowdsensing, and cloud computing are implemented.
Section 4 describes the testbed and includes a Technical Validation section that describes the raw data used in our final analysis.
The article ends with our conclusions and a brief description of projected follow-up work.
2 State-of-the-Art
For our first comparison, several proposals have made inroads in manufacturing a bracelet for children [16] that monitors their geographic location using a mobile application [17] controlled by their parents or guardians. Some only bear an initial cost, while others require a monthly payment for services. However, the cost of these bracelets exceeds the economic capacity of the majority of Ecuadorian families, as well as of families in the rest of Latin America, where the minimum wage does not often cover the cost of staple foods [18]. For example, as measured in June, 2018, the poverty level in Ecuador stood at 24.5% [19]. The bracelet system is basically a preventive tool that incorporates bracelet tracking using a GPS-based interactive map [20]. It delimits safe areas and notifies a child’s guardians whenever a child leaves these zones, etc. [21]. Even though many parents wish for these bracelets, their distribution and use are limited due to the problems mentioned above.
The Natalia Project [22] is a good example of a proposal that uses trackable bracelets. The Natalia Project safeguards the lives of human rights workers that operate in conflict zones, in which politically motivated kidnappings are frequent. The Natalia Project provides users with bracelets that rely on geospatial positioning. It permits trackers to determine the real-time geographic location of its users. In the event of a kidnapping, it sends alerts to Facebook and Twitter [23] to maximize the number of people aware of the incident. Nevertheless, the indiscriminate use of social networks invites incidents of fake or outdated news, which increases a sense of social shock fatigue [24] and damages the credibility of these media.
In contrast with the Natalia Project, the system described in this article provides a reliable means of communication for its users. All information broadcast is verified beforehand by a police officer and/or other authorized users of the system. Likewise, the costs of the mobile application for a user with a smartphone are zero, since the system takes advantage of the mobile phones already deployed throughout society, especially their sensor and communications abilities
In 1996, a notification system for missing minors known as Amber Alert was developed for the USA [25]. Whenever a minor disappeared, this system alerted the adjoining community using a diverse array of communications media, such as radio, television, and/or public electronic billboards [25]. According to the 2017 Amber statistical report [26], in a majority of cases, an alert notification was issued one hour after the disappearance was reported. To this time an estimated one to three hours must be added for recovery of the missing minor.
The main difference between Amber and our proposal is that our system has been able to reduce the time for reporting a disappearance case to 10 minutes, and subsequent community notifications to under 20 minutes. In this way, search and rescue operations are initiated more rapidly, which generally leads to better results in terms of the victim’s recovery and exposure to harm.
In Mexico, researchers have devised an anti-kidnapping chip to mitigate the social problem of kidnapping. [27]. This chip is a crystal capsule embedded in the skin. It sends signals to an external device with a GPS sensor that is carried by the end user, who transmits the relevant geospatial data. Moreover, the external device has a button that can be activated manually, upon which it transmits the user’s current geographic location. The most obvious advantage of this device is that it can send an alert whenever the user suffers a significant change in vital sign activity, such as during a kidnapping or other type of emergency.
Nevertheless, its main limitation is its installation and maintenance price, which is in the range of thousands of dollars. Moreover, risk is involved in its surgical implantation and possible side effects, such as allergic reaction or bodily rejection [28]. In comparison, our system poses no risk to health, nor does it require a monetary investment. To access our system, one only has to install the mobile application.
Another example is the TrackChild [29] project from India. The goal of TrackChild is to reunite missing children with their families by using information technology (IT) before they are sold to sexual trafficking and prostitution rings. In India, more than 500,000 children disappear each year [30].
Time, resources, and money are needed to find them, but such resources are scarce in India. The Indian government has created a web application connected to a large database containing data on missing children. Photos of missing children can be uploaded to the site, where facial recognition software conducts a search against the database.
The application is used in Indian hospitals and other institutions. This project has been quite successful. One evaluation shows that approximately 3,000 children were found over a 4 day period [31].
The great advantage of TrackChild is that any citizen can use the software without having to go through bureaucratic steps. This open access accelerates the time needed to identify and locate missing children [32]. In short, this technology is useful for finding children that have not yet been identified. However, the goal of our prototype is a bit different: to enable real-time notifications for the community, converting each individual into a sensor and a potential participant in solving cases of missing persons. [33]. The QSSC project significantly scales up the number of sensors and reporting agents within the target range closest to the event.
It can contribute relevant information from any point in the network, thus augmenting the situation awareness of incidents, something that other projects, up until now, have not considered.
Table 1 presents a brief summary of the related projects described in this article in order to facilitate their comparison. It shows that Amber Alert is the solution that most closely shares QSSC’s goals. Moreover, it has been implemented in several nearby countries, but not always with favorable results. Amber Alert is not as flexible in terms of community participation, since it does not allow community members to make direct contributions to missing persons cases.
Table 1 Comparison between the proposed QSSC solution and other similar projects
| QSSC | Amber | Bracelets | |
| Linked to Community and Authorities? | Yes | Yes | No |
| Cost to participants: | Zero | Zero | Zero |
| Provides reporting capability on missing child? | Yes | Yes | No |
| Can attach data on a missing person’s case? | Yes | No | No |
| Is the notification range limited? | Yes | No | No |
| Required sensors | Smartphone with GPS and Internet connection | Within the range of the transmission medium | Bracelet and Smartphone with GPS and Internet connection |
| Maximum range | Configurable | Natl. (Ave. 195,628.92 km2) | NA |
| Message recipient | Authorities and the community | Authorities and the community | Child’s guardian |
In contrast, the QSSC Project would allow this. The other solution that stands out is the use of georeferential bracelets, but these do not link directly to police detective services. Moreover, their real-world cost is prohibitive. In contrast, the cost for developing and distributing the QSSC mobile application solution to our community is practically null, and therefore we expect that its adoption will be widespread in the community. 3 Proposed Architecture.
The QSSC project bases its requirements on operations conducted at Ecuador’s National Board on Attempted Murder, Violent Death, Missing Persons, Extortion, and Kidnapping (DINASED in Spanish) [34], DINASED’s activities include receiving reports on missing persons, initiating investigations, and searching for disappeared individuals. We should underscore the fact that this agency has worked actively to develop the notification system prototype. In alignment with DINASED requirements, we decided that, first of all, our system needed a configurable notification zone that would cover the territory of any city where the system will be used.
Second, we needed to define the set of Authorized Users (AU), which in the final system correspond to DINASED agents, or those who will perform administrative functions on registered cases using the mobile application. Third, there is also a set of Non-Authorized Users (NAU), who in the final system correspond to community members, that is, any individual who wants to participate in the system. Both types of users send notifications when they have information on a missing person within a limited geographic area centered on a specified urban area; the characteristics of the “city” are modifiable.
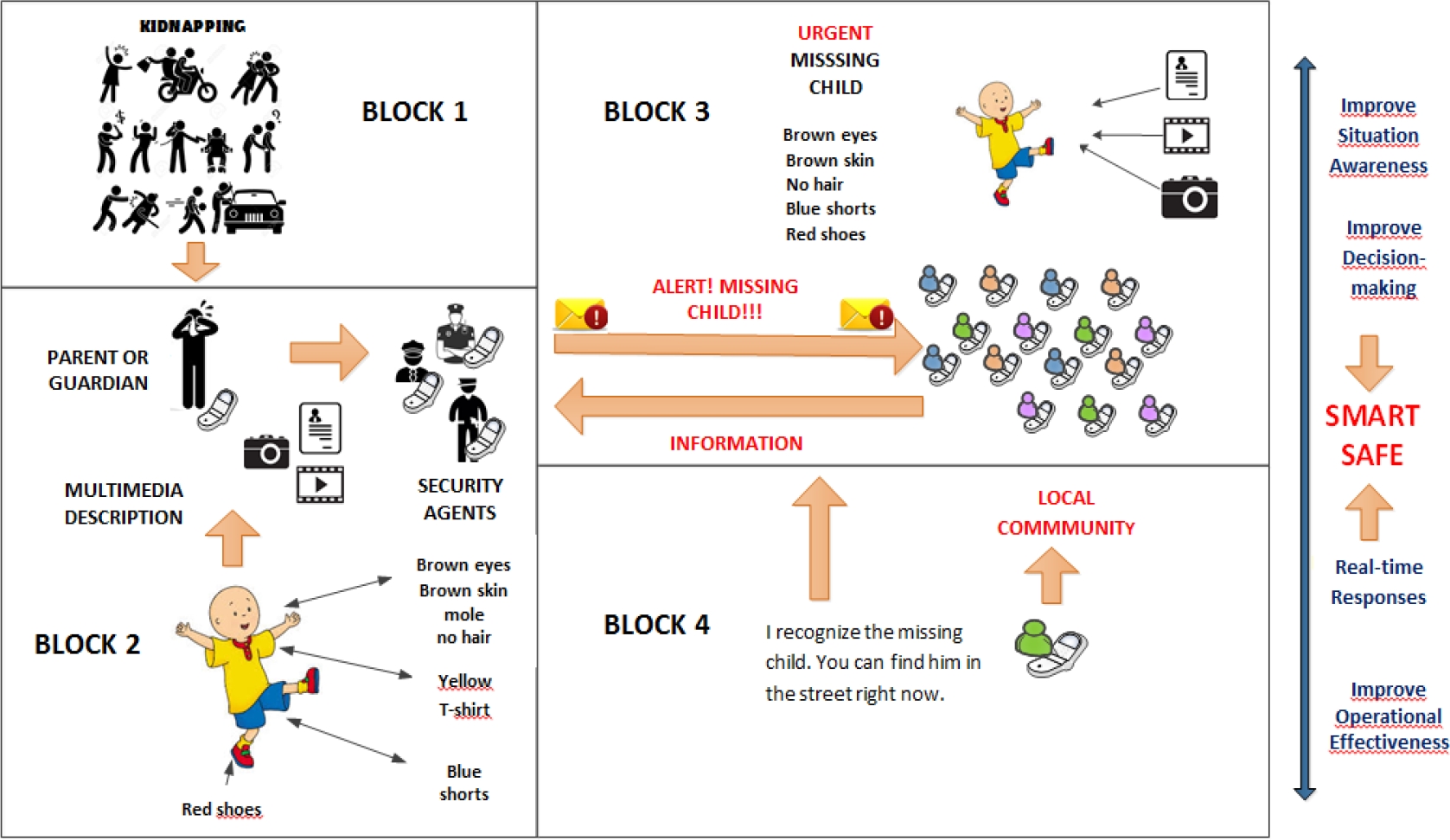
The system’s functionality is grouped according to its major system processes: User Functions – users can create, read, update, erase, search, and block other users; Multimedia Evidential Data – with the mobile application, users can append photos, videos, or text to registered cases; and Missing Persons Registration Functions – any user can register a missing person’s case in the system, but only AUs can manage the case. Fig. 1 presents a prototypical logistical scenario for the QSSC project. It begins when a vulnerable person goes missing (is kidnapped) [BLOCK 1].
Next, that person’s guardian uses the mobile application to enter a general description of the child for identification purposes, such as the color of their clothing at the time of the disappearance, and a description of what happened. The description may include uploaded multimedia files that enhance the text [BLOCK 2]. This data is sent to the closest public safety agents (AU), who are also notified by the same mobile application. The AUs conduct a brief police investigation to determine the veracity of the reported case. If they determine that the missing person’s case has no merit, they discard it. If the case appears to be valid, they notify the surrounding community [BLOCK 3]. Therefore, all people within a limited range who are using the mobile application essentially become new agents in the solution of the missing person’s case. A missing person’s alert notification must be sent to the community within the first few minutes of the disappearance, since that is the crucial time period.
Presumably, the missing person is still in the vicinity. Once the community is notified about the event, each community member can review the case in detail, including the description of the missing person and of what happened. NAUs can then publish evidential data that clarifies what happened in the case [BLOCK 4].
The evidence can consist of multimedia content, and users can tailor the information sent. For example, NAUs can enter comments that say that they have recognized the missing child, and that they have information about her or his whereabouts. They can describe the individual’s characteristics, add photos of the suspect, or upload a video of the missing child in an identifiable place.
The advantage that the community receives is that this system enhances the situation awareness that leads to making better decisions under emergency conditions. Low levels of information on an incident can introduce untimely or irremediable actions into a solution [11].
In addition, the real-time response, both on the part of security agents who verify missing persons’ cases, as well as from the general community who provides evidence, encourages rapid resolution of cases. For any given city, the system optimizes rescue times by improving operational efficiency, since it can count on community support. This combination of forces: security agents (AU), the community (NAU), and information technology (ITC), creates an intelligent and safe city. Thus, Quito falls within the Safe Smart paradigm.
4 Technical Proposal
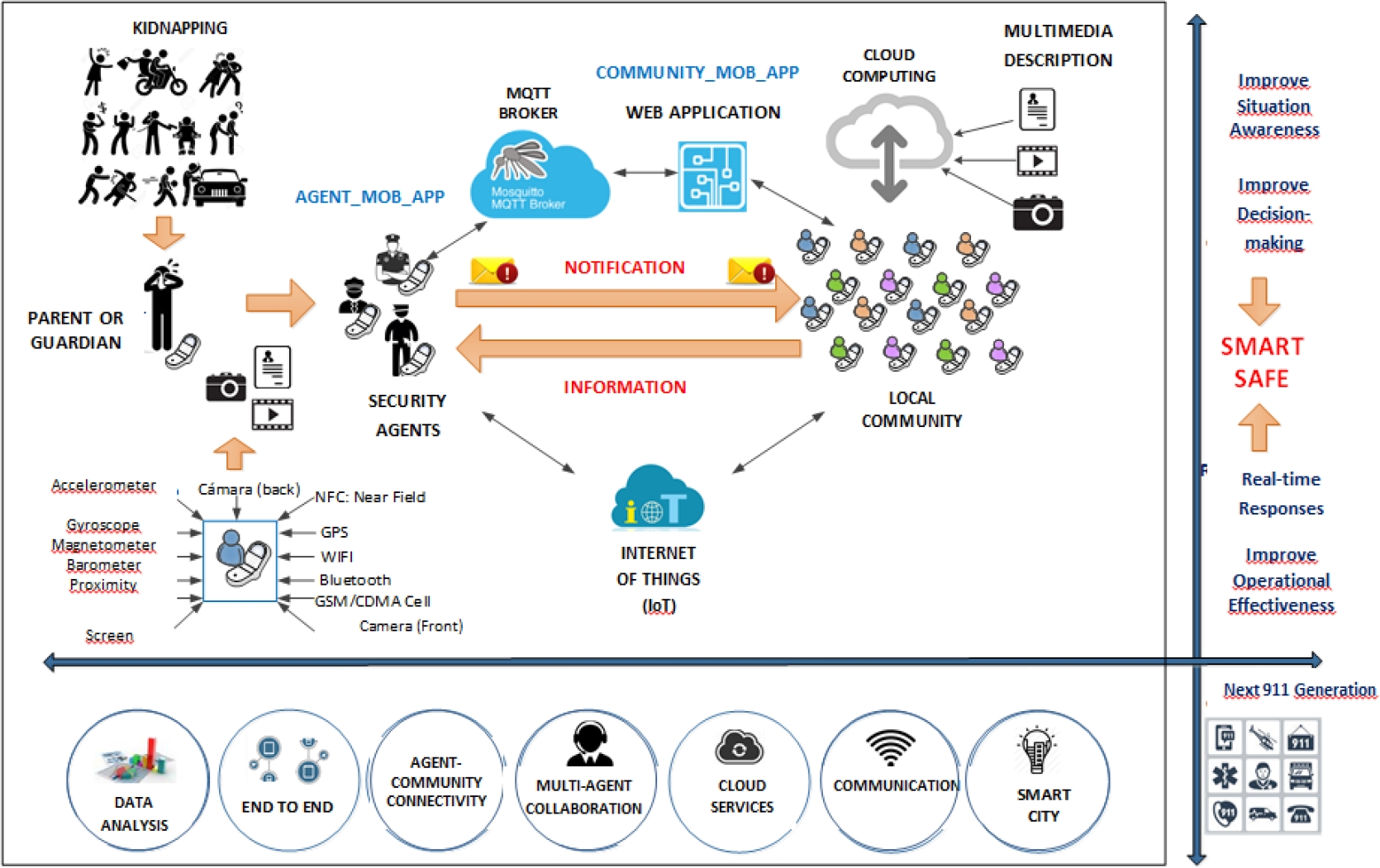
Fig. 2 presents the technical schema corresponding to Fig. 1 (described above). Fig. 2 shows the role that each technology plays to achieve optimal functioning of the system.
First, IoT plays a crucial role in this system. IoT supports digital interconnectivity between smartphones and the data server.
It uses a communications protocol that minimizes hardware resource consumption on the storage device. We have chosen the MQTT communications protocol to report cases of missing persons to the general community. Specifically, our system uses the Eclipse Mosquitto MQTT server as the MQTT broker. Mosquitto acts as an intermediary between clients that broadcast messages using the mobile application and clients who want to receive notifications on cases of missing persons.
The latter include both security agents (AU) and the community at large (NAU). Messages circulate via Mosquitto and appear in the notification bar on every mobile device that receives the message. The mobile device hosts the MQTT client and waits for new messages. The MQTT client uses a minimal level of hardware resources, including RAM and processor memory. Thus, it has a minimal impact on the mobile phone’s battery charge [35], which is an important consideration for this application.
Another beneficial component of the system is cloud computing. Cloud computing brings scalability to the system. Since the application is theoretically available to the whole society, the system needs to adjust to any exponential user growth, which is directly proportional to growth in server hardware resources. Cloud computing also reduces the cost of implementing the server, since it depends solely on the number of resources utilized. By using cloud resources, the system can eliminate the need to make an initial investment in infrastructure for data server storage. Locating services in the cloud makes it easier to deploy the system throughout communities the minute it is ready for implementation.
Consequently, our validation testing better models’ reality. In terms of data security, the enterprise selected to provide cloud services will be in charge of making backups and secure copies, and safeguarding reliable functioning of the service offered.
At the other end, we have selected the mobile phone as the destination device because of its ubiquitous presence in society. For the smartphone, we have chosen the Android platform as the preferred operating system due to its popularity [36].
We have used Android Studio to develop the mobile application. With Android Studio we can access network connection sensors and GPS systems in order to consult missing persons data and determine the geographic location of the device. We can then determine whether the user is within a notification zone or not.
With these combined tools, we have been able to develop a real-time notification system that connects security agents (AU) to the community (NAU), thus supporting multi-agent collaboration. In additoin, cloud services guarantee minimal costs for infrastructure and technology distribution to the end user. The selected technology facilitates adaptation to continual changes in the business requirements and infrastructure. It models an intelligent and effective system that supports data storage, analysis, and broadcasting, placing Quito, Ecuador in the center of development and innovation for the smart city.
Currently, the technology used to develop this application is already being used by various smart cities in the developed world to implement real-time rescue systems and other projects [37]. Individuals accessing information with their mobile devices are guided to make better decisions, and well as contribute to the system when they send data from sensors on their smartphones. This project uses the same principle, that is, it uses popular distributed technology to propose solutions that optimize operational, economic, and social factors, thus improving quality of life and driving the economic and social development of Quito forward.
5 Communications
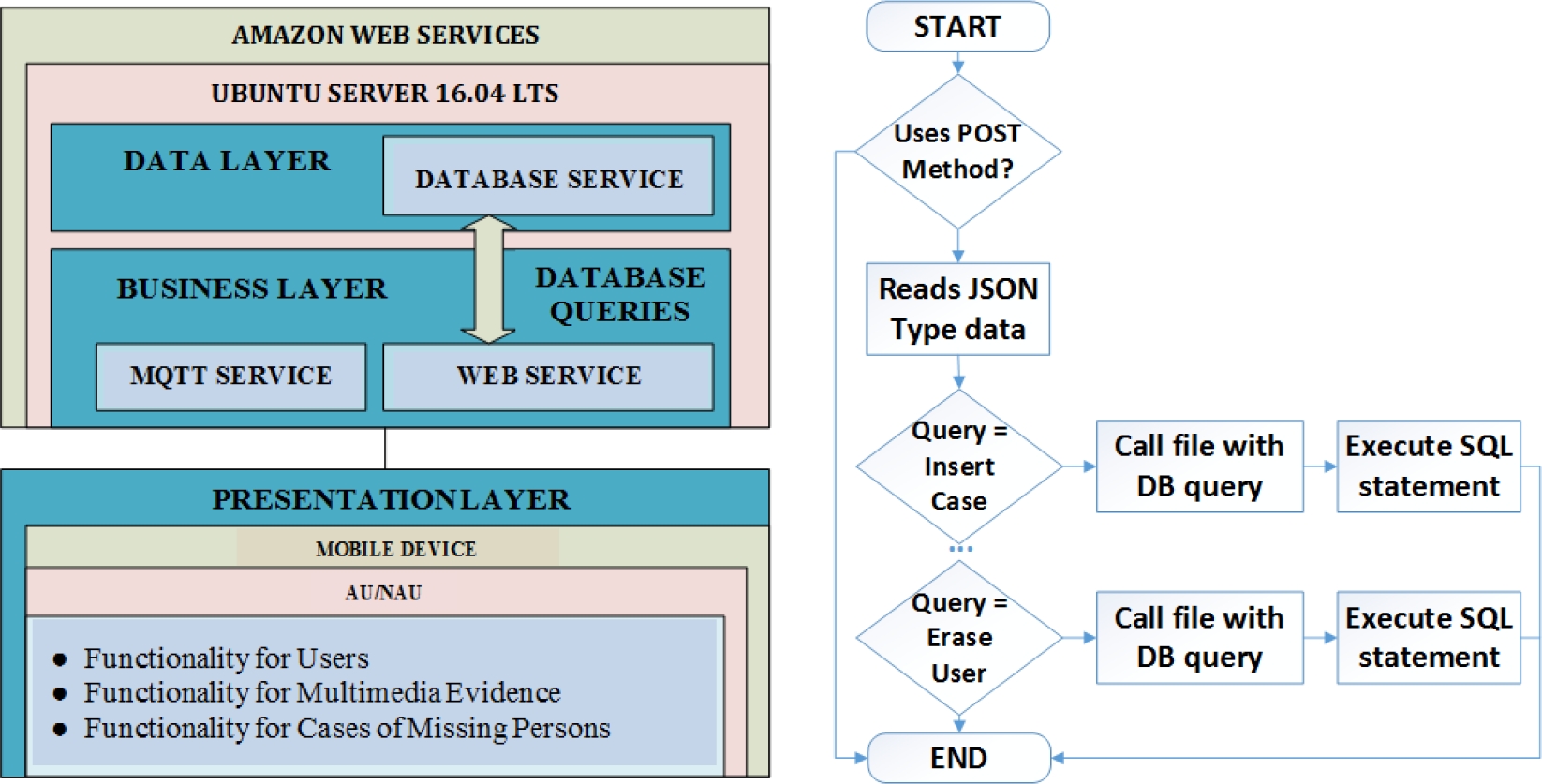
The QSSC software architecture is described in Fig. 3a. We are using a layered software architecture with three separate modules: the data layer, business layer, and interface layer. The data layer describes data storage. It uses MySQL for storage and Oracle Workbench for data management. The business layer, or business logic, encompasses all programs needed to implement system functionality. These include an IaaS (Infrastructure as a Service) cloud service from Amazon Web Services (AWS) for storing a server with an operating system:
Ubuntu Server 16.04 LTS. On top of the server rests the MQTT broker to support system notifications, and the Apache Web service to publish web-based services. The interface layer uses Android Studio to develop a mobile application that interacts with the end user. This application receives data transmitted by users and displays results.
Fig. 3 depicts how the MQTT communications protocol is hosted. This protocol is defined in the ISO/IEC PRF 20922 standard [38]. It is designed to transmit publisher/subscriber messages in a client/server environment that executes using a trustworthy TCP/IP protocol [38]. It is often used in IoT applications because it adds little to the load on the hardware resources of the host device, making it a common pick for transmitting sensor messages in industry [38].
Message delivery has been implemented at the QoS 2 quality of service level [38], defined as “exactly once.” QoS 2 is the highest level of quality that MQTT offers; it guarantees that network messages will neither be lost nor duplicated. In addition, the MQTT server is configured with access credentials to eliminate anonymous connections and improve server security. We should note that even Facebook’s instant messaging service, Facebook Messenger, [39] now uses MQTT because the protocol uses so few resources. MQTT saves on battery life and supports broadband service on smartphones. These are the same reasons that MQTT is the preferred protocol for transmission of sensor messages on the IoT.
We used the PHP scripting language to program the web service. PHP is compatible with Android, and therefore the application can have widespread distribution. Fig. 3b describes the web service logic. From the diagram it is clear that users only need to know the IP address of the server, or the domain name and, together with the file name of the web service [40], users can access the system.
Each one of the cases of missing persons can have associated multimedia resources that enhance the description of the disappeared person. The size of these resources depends on a device’s configuration. For example, a photo that is several MBs large increases the time needed to display the image on a mobile device.
In order to reduce display time, we make a low-resolution copy of the original image, so that display is faster on mobile devices. Users can also access video content.
Therefore, the QSSC system previews the video so that users can get an idea of its content. Specifically, the system captures the first second of the video and presents it to the user. These resources are hosted in a public folder on the Apache Web server, where they are easily accessed for viewing and download.
We should emphasize that in order for users to interact successfully with the prototype and communicate accurately on the server, each user must have an Internet connection, these connections determine how well the application operates in real-time. Moreover, the application must be permitted to manipulate the device’s GPS sensors in order to detect the user’s location, otherwise it will be impossible to receive notifications of ongoing cases.
We took these steps in lieu of two factors. First, since the goal of the QSSC system is to send notifications in real-time and optimize rescue times, that means that the person kidnapped should not move out of the range of a short-term rescue. According to the analysis carried out in Quito, this notification area is 370.39 km2, which is based on a previous analysis [41] defined for a 30 minute period, Quito’s longitude, and a maximum evasion velocity of 28.26 km/hr. Second, there is a need to avoid causing panic in communities outside the search zone, since they obviously will not be able to contribute relevant information to cases given their distance from events.
Fig. 3b describes the logic of the a) main web service file that receives b) web requests using the HTTP protocol. Client/server messages are in JSON (Javascript Object Notation) format. The system first receives an HTTP request, which is analyzed to see whether it is using the POST method. If this condition is true, the data (in JSON format) contained in the request is read in order to look for an instruction that allows the system to execute a specific function. For example, Fig. 3b illustrates the “insertCase” instruction, which indicates that a user wants to log a disappearance. In order to do this, the system queries the database appropriately and, according to the database response generator, the user is notified whether the transaction is accepted or rejected.
6 Technical Validation
Given that it is not possible to detect a real kidnapping for test purposes, we simulated a kidnapping scenario, as detailed in the Technical Architecture section of Fig. 1. We asked 50 people of various ages and professions who own smartphones with different capacities and features to use the prototype system over a 30-day period. These participants were divided into two groups: 25 NAU users and 25 AU users.
The test consisted of simulating several cases of missing persons in different neighborhoods of Quito; the goal was to determine the variation in rescue times. We should emphasize that for disappearances, the NAU users were unaware of specific data on the case, including how, where and when the kidnapping occurred, and other characteristics.
We defined a case range of 70 km2, justified beforehand and shown in Fig. 4. Our objective was to limit the notification range solely to users who could participate in the search.
Users who participated had Internet access from various providers with different web service plans, and used different GPS sensors to determine whether they were within range of the technical validation test area.
Our prototype was developed to authenticate users and register them when they published data about a missing person, since this information is key for police investigators who want to validate and broadcast cases of disappearance. During the test period, the system broadcast ten cases of missing person. Users interacted with it, broadcasting multimedia data related to the cases. From this validation test, we achieved a 60% high participation rate from the NAU community in each one of the simulated cases.
The results analysis is found in the next section. We should emphasize that during the test, AUs were able to successfully execute administrative functions (create, edit, and delete) on case evidence. However, the NAUs were restricted to reviewing case details and attaching multimedia evidence. Active participation from all users was vital to resolving test cases, since each person (AU or NAU) contributed a different clue that led to finding the missing person, improving rescue time, and fulfilling the main goal of the system.
In addition, the notifications displayed on the smartphones were able to inform final users about events local to their geographic location.
In this respect, several users who left the city before a missing person’s case was broadcast reported that, in effect, they did not receive any notifications regarding that case, thus demonstrating that the notification range limit worked successfully.
One should note that the prototype can be feasibly personalized to fit any city search, according to its characteristics. Users can adjust the range of geographic notification according to how the MQTT protocol is implemented. To receive an MQTT message, users must be subscribed to MQTT topics, which are diffusion media embedded in the protocol. The geographic limit is abstracted out as if it were an MQTT topic. Thus, each topic, also called an MQTT theme, can represent different “cities,” covering areas up to and including whole countries in the future.
Therefore, each user, via the applied system, automatically provides her or his geographic coordinates to that system so that the system can determine whether they are within range. If they are verified as within the limit, their subscription to the theme (topic), i.e., geographic area, is confirmed. However, they can also be subscribed to another topic representing another nearby city.
Likewise, the different diffusion media within the protocol have been validated. For example, AUs were subscribed to a specific them that allowed them to receive messages indicating a missing person’s case had been registered. In contrast, NAUs only received messages on themes that represent areas of geographic location. By segmenting the diffusion media, the system offers users a more organized and structured communications service.
Finally, based on its performance in the simulation, the system has fulfilled its objectives exactly in terms of the requirements specified by the DINASED police force. It is clear that the system’s effectiveness was directly proportional to the number of users that used the prototype, that is, as the crowdsensing indicates. As the number of individuals in the system increases, less time is needed to locate the missing person, and fewer errors are made.
7 Results and Analysis
The QSSC notification system for missing persons was tested in Quito, the capital of Ecuador. Given the uncertainty involved in verifying a kidnapping, we tested our proposed system by simulating ten cases of missing persons. Results are given in Table 2. The results obtained correspond to the comprehensive testing conducted during the kidnapping scenarios and their characteristics, as detailed in the previous section. Security agents and 50 community members assisted the project in completing the simulations over a period of 30 days.
Table 2 Results from Cases of Missing Persons
| Number | Time to register a missing person’s case (min) | Time to broadcast missing person’s case (min) | Number of multimedia contributions | Community participation | Distance to point of solution (km) | Time to solve missing person’s case (min) | Missing person’s case solved by user type |
| 1 | 5 | 10 | 10 | 50% | 31 | 11 | NAU |
| 2 | 7 | 8 | 8 | 45% | 35 | 18 | NAU |
| 3 | 6 | 6 | 6 | 23% | 29 | 13 | NAU |
| 4 | 9 | 10 | 11 | 52% | 45 | 14 | AU |
| 5 | 11 | 13 | 13 | 58% | 16 | 16 | AU |
| 6 | 8 | 12 | 12 | 43% | 22 | 19 | NAU |
| 7 | 6 | 8 | 16 | 38% | 31 | 18 | AU |
| 8 | 12 | 10 | 12 | 25% | 8 | 13 | NAU |
| 9 | 14 | 11 | 11 | 19% | 12 | 11 | AU |
| 10 | 8 | 15 | 8 | 13% | 16 | 20 | NAU |
| Average | 8,6 | 10,3 | 10,7 | 37% | 24,5 | 15,3 | 60% (NAU) |
Consequently, we were able to obtain optimal results. Results included the following achievements. The time to record a disappearance was less than 9 minutes, which indicates that the community responded immediately whenever a person disappeared. The average time to broadcast the missing person’s case was 10.3 minutes; this demonstrates that AUs intervened rapidly to validate the case. The average time to solve a case was 15.3 minutes, depending on the number of NAUs that participated. Whenever this latter number is higher, the probability of finding a missing person rises. We can thus conclude that community cooperation is a priority; in the simulations, 60% of cases were solved by a NAU. To these results we can add the fact that there was 37% participation among community members, with an average of 11 multimedia contributions per missing person’s case. In addition, the simulations reveal that the average rescue distance was 24.5 km2, indicating that cases were solved within the city limits. The prompt response on the part of the community prevented kidnapping victims from leaving the city.
The notification system was also evaluated for usability (ease of use) to the end user and system performance. These are important factors to our real-time system model. We prepared a questionnaire in which users could rate ease of use. We also measured the interval of time (in seconds) that users needed to complete a task. Specifically, the measurement started when the user pressed the send data button and ended when the server returned a successful response message.
The majority of actions took only a few seconds to complete, as depicted in Fig. 5. We also analyzed technical aspects of the mobile application. If these parameters had displayed inappropriate results, they could have justified deinstalling the mobile application [42].
In summary, in terms of storage time and downloading resources associated with cases of disappearance, the results obtained from the validation reveal than, on average, users need 5 seconds to store an image on the server and around 2 seconds to download that image using a wireless access point. However, these times triple when the user accesses a 3G network. For LTE connections, times improve considerably. These data are summarized in Fig. 6, which gives average transmission times for images and video using WiFi, 3G, and LTE.
The validation tests also measured the performance of the MQTT protocol on the client mobile application. Results show that the protocol completed its functions satisfactorily. That is, the MQTT protocol successfully sent and received messages using different logic diffusion media (MQTT themes). With this technology, users can divide the message recipient group into different sectors according to each city’s requirements. Based on observations made by end users, the time needed to deliver an MQTT message is immediate, i. e., less than one second.
These results confirm that the prototype is indeed a system capable of optimizing search and rescue times for missing persons within a given city. One virtue of our prototype is that it can be adapted for other Latin American cities that share similar social problems, regardless of whether is problem is more or less severe in that city.
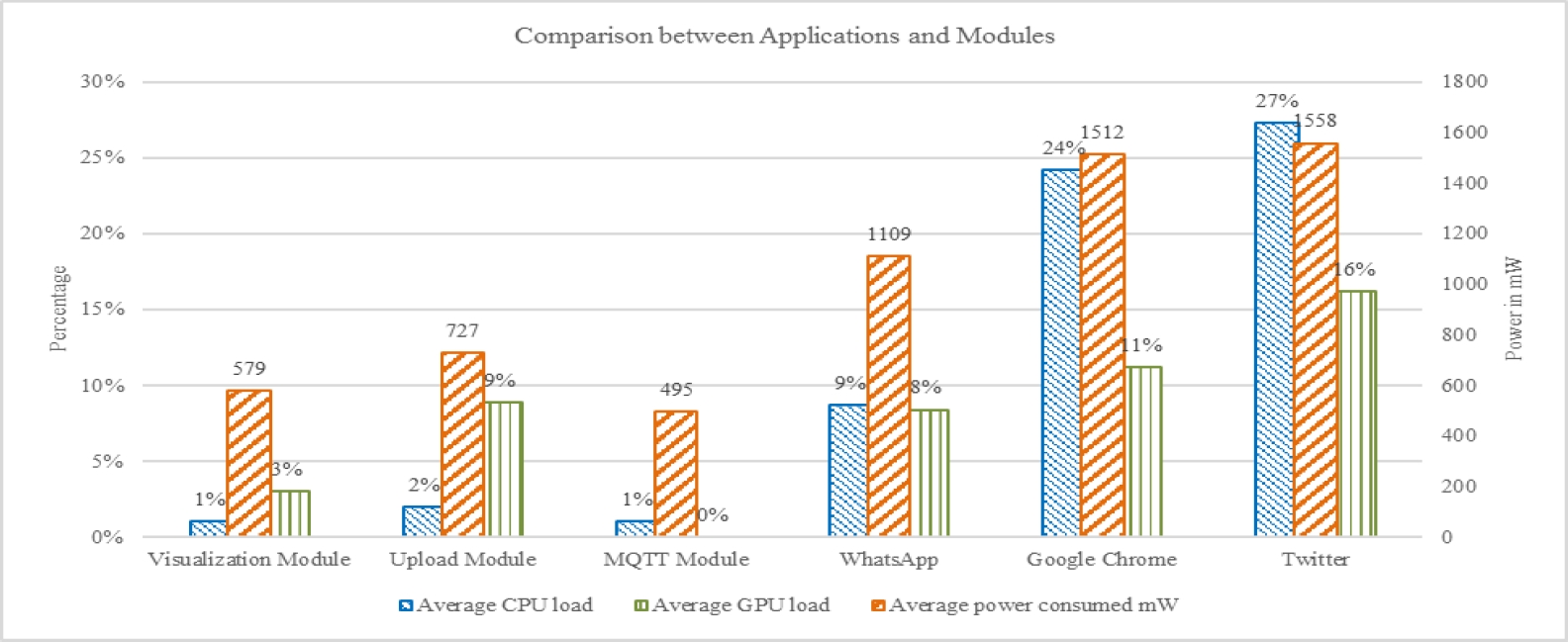
We measured the performance of the notification application using tools packaged with Android Studio and third-party applications. We set the measurement interval at 5 minutes. Results are given in Fig. 7. For example, the MQTT module consumed 0.495 Watts of power, in comparison with WhatsApp, which consumed more than 1 Watt of energy. That is, the power consumed by the prototype is minimal and does not have a significant impact on the end user’s smartphone battery.
8 Conclusions and Future Research
In Latin American countries, the problem of vulnerable people going missing is alarming. Thousands of cases of missing minors are registered each year.
For example, in Ecuador an average of 500 reports of disappearances are reported per month [7], which instills a state of fear in the public with regard to the security the government provides to citizens. Despite the efforts of the National Police to halt this problem, the disappearances continue, making it clear that a better solution is needed. This study proposes a system for alerting the community about missing persons in order to locate them. The system is built on a distributed platform adaptable to the urban conditions of a city like Quito. Its goal is to disseminate real-time alerts with attached multimedia data that assists in locating and rescuing missing persons.
Getting the whole community involved in the solution is the key to our proposal. To maximize the chance of rescuing individuals who have disappeared, all citizens must be considered possible agents within the rescue assistance operation. The tests performed in Quito show that the more robust the crowdsensing network, the more the time to rescue decreases. Crowdsensing is strengthened with multi-agent participation. The autonomous and free movement of each agent leads to system decentralization and more effective responses to emergencies. Connectivity between police and the community makes for a better notification system with more robust features, beating out projects with the same goals such as Amber. The average times recorded for our prototype are much lower than times derived for similar projects.
In terms of technical and userbase features, the QSSC notification system has surpassed other related projects that are mentioned in the State-of-the-Art section. In technical terms, time to rescue has decreased to 34.2 minutes. For the userbase, the local community expressed its approval and trust in the system because notifications and broadcasts can only be sent by authorized people.
The system puts Quito among the elite of Smart Safe cities. Information recompiled by mobile devices can be used to alert the community about any type of risky situation. This capability creates a collective situation awareness that allows community members to make appropriate decisions when faced with different types of problems facing society.
During the project’s development, we used state-of-the-art technology that contributes notable benefits in regards to exchanging and sharing information. The AWS (Amazon Web Services) cloud adds a high level of trust that is available to all services offered by the system. AWS allows users to access the system via the Internet from any location under any circumstances. In addition, the AWS platform is flexible enough to satisfy the QSSC user requirements. It can cover large-scale catastrophes, adjusting to scale for increases in quantity of information and user requests to the system. That is, the server’s hardware resources adjust dynamically to the situation.
In addition, the end-to-end architecture, along with the features of the MQTT protocol, allow users to send messages under adverse conditions, such as during an emergency with long delays, high levels of web traffic, low bandwidth, etc. MQTT offers devices low impact functioning and low levels of resource consumption, making it the preferred protocol for implementing alert and notification systems.
Future research is aimed at developing a web application to partition the notification area for optimal coverage. One idea is to implement a hierarchy of MQTT servers to eliminate failure points in the notification system. Another idea is to use the MQTT protocol’s hierarchical topics to emulate districts and divisions within the country in general. This would allow authorized users to select the canton or province that should receive notifications. This feature would also be useful to create notification groups associated with hospitals, shelters, morgues, social service centers, etc., according to the services they offer.
Finally, we plan to implement data processing and analysis technology to handle large amounts of data, such as BIGDATA. We want to generate prognostics and construct maps that indicate the locations most susceptible to kidnapping events.










 nova página do texto(beta)
nova página do texto(beta)