1 Introduction
In recent years, Peer-to-Peer (P2P) networks have been extensively studied in order to increase the capacity of systems by having the nodes cooperating to alleviate data traffic at the servers. With the increasing use of mobile devices, such as smartphones and tablets, P2P networks could be an alternative to alleviate the traffic by accessing a wireless network as noted in [1].
Additionally, vehicular networks can also benefit from a P2P architecture for information dissemination of safety and comfort services [2] - [5]. Indeed, modern day vehicles are packet with nodes that recollect information about both the status of the car and the road conditions. This information can be shared among drivers and authorities in order to prevent or detect road accidents. Also, users can share files (music, video, social network data, etc.) among themselves in both pedestrian or vehicular environments either by the sensors inside the vehicles or the mobile devices of drivers, passengers, and pedestrians.
In this work, we are interested on analyzing the effect of different channel quality zones on the system’s performance and the impact of the inherent mobility of nodes in urban vehicular and pedestrian applications.
The issues of a wireless P2P network, as well as the impact of mobility of the nodes has been investigated before in [6] - [8]. In [6] - [8], different challenges on the implementation of a wireless P2P network are identified and discussed.
However, these issues are manly focused on the TCP inherent problems arising from an unreliable and shared channel as well as the impact on the different BitTorrent mechanisms. In [8], the problem from nodes leaving and entering the system, as well as their movement are presented.
In contrast, the case where nodes experience different channel conditions, typical in wireless networks, that are reflected on the data rate are not specifically considered. Nor is considered the effect of mobility affecting the overall system’s performance in terms of the available resources in the network. Specifically, the impact of having some peers that experience a bad channel condition and other peers experiencing better channel conditions have not been studied before. Moreover, we propose to take advantage of the nodes closer to the access point. Indeed, these peers experience a higher data rate. Hence, they provide more bandwidth to the network than peers farther apart from the access point which can only provide a marginal amount of resources to the rest of the peers.
Note that a user with high data rate, can provide a much faster download rate to other peers connected to it while a node with low data rate that serves other peers provides a much higher download time. Building on this, a priority scheme is proposed that first allocates the available resources to users with better channel conditions. Meanwhile, the remaining bandwidth is distributed to the rest of the peers. By doing so, leeches with higher data rates become seeds much faster than leeches with low data rates. This in turns improve the overall bandwidth in the system.
It is important to notice that the impact of the priority scheme is much higher when there are scarce resources in the system. This is because when the system has enough bandwidth (typically when there is a high number of peers connected in the network) all the peers can download at the maximum rate. Hence, there is no visible impact of assigning bandwidth first to leeches closest to the AP or the BS.
The system is studied using a Continuous Time Markov Chain that describes the evolution of the system in terms of the number of leeches and seeds in the different coverage zones.
As for the specific P2P protocol, we focus our attention to Bit Torrent. BitTorrent is a P2P application used to facilitate the download of popular files. The main idea is to divide the files into many pieces called chunks which peers exchange among each other. The BitTorrent protocol differentiates two types of peers: leeches, which are peers that have a part of the file or not data at all, and seeds, which are those peers that have downloaded the complete file and remain in the system for some time to share their resources.
In [9] and [12], the general P2P network is studied by means of analytical tools at the peer level. By this, we refer to a model where only arrivals, departures and file transfers (that correspond to the conversion of peers from leeches to seeds) are considered. These models are very accurate in representing the general behavior of a P2P network in terms of the number of leeches and seeds in the system, which in turns allow to calculate the average capacity of the network and the average download time. Unlike these models we consider the effect of mobility of nodes in wireless P2P networks.
In [1] the authors analyzed P2P models to Internet access in Cellular data networks. By simulations, they assure that the advantages offered by typical P2P networks (wired networks), such as less power transmission and better spacial reuse, does not mean a better performance in Cellular wireless networks. They conclude that this is due to the fact that the main protocols used in the wired networks are not designed to work in wireless environments.
Other works like [15] are focused on the issue of selecting the appropriate peers to download the file from. However, in this work, we focus on the effect of nodes’ mobility in terms of the available resources in the system.
Unlike previous works, we consider a priority-based scheme which is different from the general idea of incentives such as [13, 14]. While the incentives are used as means of influencing a certain behavior in the peers any time the peers are connected to the network, our proposal is used only when the resources in the system are scarce. Meanwhile, when resources are sufficient in the network, there is no need to apply the priority scheme.
In [11] a priority model for a general P2P networks was proposed considering both cooperative and non-cooperative leeches as an incentive. However, this is done in the context of a typical P2P network. In this work, we propose a priority scheme based on the channel condition experienced by a particular peer. Specifically, peers that are closer to the access point are benefited from this scheme in order to have more bandwidth in case of penury. Hence, peers with higher data rates can download the file faster than nodes experiencing bad channel conditions. As such, peers with higher data rates can share the complete file to the rest of the nodes.
The rest of the paper is organized as follows: The main assumptions, variables used in this work are described in detail in Section II Also, the analytical model is developed. Section II presents the main numerical results. The paper finishes with relevant conclusions.
2 Experiments
In this section the basic assumptions and system’s variables of a wireless BitTottent-like P2P network are described. The dissemination of a non-real time data file in a P2Pnetwork is considered. To capture wireless channel impairments, differentiated zones of coverage are considered through the use of adaptive modulation and coding (AMC). That is, the coverage area in the WLAN or a cell in the cellular system is divided into z coverage zones. A node located in the i th coverage zone uses the i th data rate, denoted by µ i . Indeed, it is considered that inner zones have higher bit data rates than outer zones due to the better channel conditions.
In other words, it is considered that µ z < µ (z−1) < ... < µ (1). The total number of leeches in zone i is denoted by x i (for i = 1, 2, , z) while the total number of seeds in zone i is denoted by y i . The number of leeches downloading in zone i at time t is denoted by x i , assumed to be real in this fluid modeling approach.
The total number of leeches and seeds in the system is denoted respectively by
At any given time there is at least one seed in the system. All peers have complete knowledge of the system, i.e., all peers know which chunks have any other peer and peers always cooperate to upload data if they have available bandwidth. As such, if the number of leeches and seeds is sufficiently high, all leeches download the file at the maximum download rate c. This system condition is referred as abundance.
However, when there are not enough peers in the system, the leeches download at rate
A leech in the system aborts the file download in an exponentially distributed random time with mean 1/θ. Conversely, seeds remain in the system, after the file download an exponentially distributed random time with mean 1/γ.
2.1 Mobility Model
User mobility is considered by assuming that a node in zone i moves to zone i + 1 with rate m + and it moves to zone i − 1 with rate m −. In the former case, the user moves to a better coverage zone while in the latter, the user moves to a worst coverage zone. In order to study the effect of user mobility in different environments, two different cases are considered: a) WLAN, where users are typically aware of the location of the access point (AP). As such, a user that finds itself in a bad coverage area can move closer to the AP in order to improve its condition. Therefore, in this scenario, it is considered that m + > m −.
This is typical in pedestrian environments, both in indoor (commercial/business buildings, etc.) and outdoor (public plazas, concert and sportive arenas, etc.) scenarios. b) Cellular System, where users usually are not aware of the location of the Base Station (BS). Hence, in case that a user is in a bad coverage zone, it is not able to change to a better coverage zone in an explicit manner. As such, it is considered that m + = m −. These are typical vehicular and outdoor pedestrian scenarios where WiFi coverage is not available and nodes must transmit via an ad-hoc or cellular networks.
Finally, it is considered that a leech in zone i becomes a seed in the same zone i after it completes the download of the file with rate τ i . This is because the probability that a user finishes the complete download of the file in the same instant that it changes its coverage zone is considered to be a very low probability event.
2.2 Mathematical Model
The P2P network is modeled using a Continuous Time Markov Chain (CTMC), as shown in Fig. 2, that captures all the previously mentioned events in the network: node’s arrivals, node’s departures, change of coverage zone from nodes due to their mobility and complete file download (a node that finishes the download of the file and goes from leach to seed). The CTMC proposed for this analysis is as follows:
From the previous description, it can be seen that the transfer rate at which leeches become seeds, i.e., leeches download the complete file, τ i , can be expressed as:
From (1), it can be seen that when the system is in abundance conditions, peers download the file at the maximum download rate c. However, in penury conditions, the available resources (given by the number of peers, x + y, uploading the file) are uniformly distributed among the leeches in the different coverage zones as described by: xi/x.
The evolution in time of the previously described system in terms of the number of leeches and seeds in the different coverage zones satisfy:
Let us compute the equilibrium point of this dynamical system, denoted by
where:
A = αλ 1 cm −(γ + m +),
B = βλ 3 cm +(γ + m −),
C = c(αm + m −(γ + m +) + βm + m −(γ + m −) + (γ + m +)(γ + m −)),
α = c + θ + m + β = c + θ + m −. (3)
It is important to mention that this fluid model is developed considering a high amount of nodes in the system as described in [9]. The case of penury, where
— λ i , to state W(t) + e i , for i = 1, 2, 3.
— l i θ, to state W(t) − e i , for i = 1, 2, 3.
— τ i , to state W(t) − e i + e j , for i = 1, 2, 3, j = i + 3.
— (n i − 1)γ, to state W(t) − e i , for i = 4, 5, 6.
— l i m +, to state W(t) − e i + e j , for i = 2, 3, j = i − 1.
— l i m −, to state W(t) − e i + e j , for i, j = 1, 2, j = i + 1.
— n i m +, to state W(t) − e i + e j , for i = 5, 6, j = i − 1.
— n i m −, to state W(t)−e i +e j , for i, j = 4, 5, j = i + 1.
This Markov chain is solved numerically.
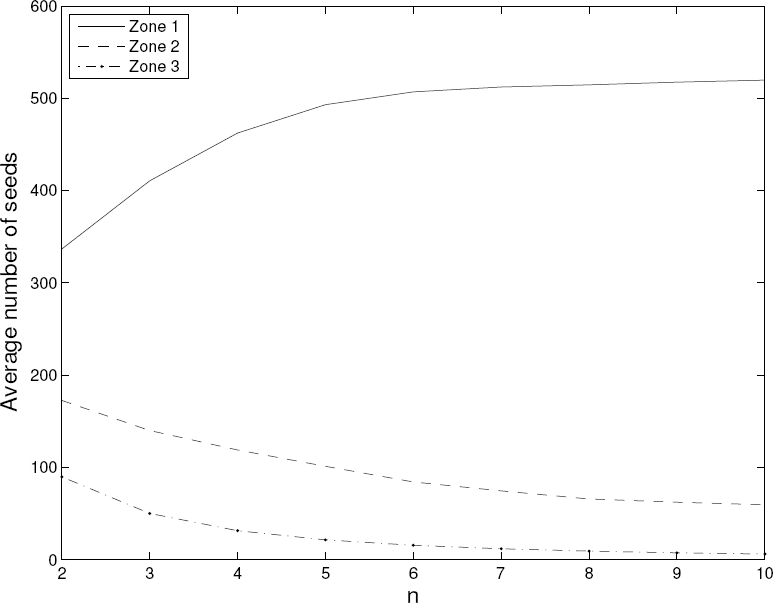
Finally, the number of peers in each zone is investigated for each environment. In Fig. 5, it can be seen that for the cellular system, the amount of users in each zone is very similar, as users are typically uniformly distributed in the service area. On the other hand, nodes in a WLAN can improve their channel quality by approaching the AP, as noted by the greater number of nodes in zone 1 compared to zone 3.

Fig. 3. Average number of peers (a) seeds, b) leeches) in zone 1 for different values of θ and γ in the cellular environment
2.3 Priority Model
As previously described, we propose a priority scheme that favors the leeches closer to the AP or the BS in order to be served before the leeches in the outer zones whenever the resources in the system are scarce. Thus, we can distinguish three cases:
— Abundance: In this case, there are enough resources. Hence, all peers download at the maximum rate, c;
— Semi-Penury: Now, the available bandwidth is high enough to serve all leeches in the inner zone at the maximum download rate, c, but not enough to serve the rest of the peers at this maximum rate. As such, leeches in zone 1 download at the maximum rate and the leeches in zone 2 and 3 share the remaining bandwidth.
— Penury: In this case, there is not enough bandwidth for any leech in the system. Hence, only the leeches in zone 1 are served with a bandwidth lower than c while the rest of the peers are not served at all.
Following this, the transfer rate τ i can be expressed as follows:
In Abundance conditions, i.e.,
for i = 1, 2, 3. In Semi-penury conditions, i.e.,
for i = 2, 3. Finally, in Penury conditions, i,e.,
3 Results and Discussion
We now discuss some of the relevant results of this study. Recall that two different scenarios are considered in this work: A pedestrian (for ind-oor/outdoor emplacements) with WLAN coverage and a vehicular (for outdoor emplacement) with cellular coverage.
In Fig. 3, the case for the cellular system is presented, i.e., m + = m − for both the Markov and Fluid models developed in the previous section. As expected, the system has the best performance when peers remain longer in the system, increasing the available bandwidth. This occurs when θ and γ are low. As γ increases, the number of seeds decreases and this in turn causes a rapid decrease on the system’s resources which is reflected by a higher number of leeches. Indeed, as resources are scarce, it takes much longer for peers to become seeds. As θ increases, the number of leeches decreases since peers leave the system much faster, even before downloading the file, which in turn causes a decrease on the number of seeds. However the impact of θ is lower that the impact of γ in the network’s performance.
Additionally, it is clear from these results that the number of seeds is more important that the number of leeches in the system.
Observe, for instance, that a high number of leeches does not imply a good system’s performance. It can also be seen that, in general, there is a good correspondence between both models, except for the case where there are a few seeds in the system. Recall that the fluid model is appropriate for a high number of peers. As such, in these conditions, the Markov model is more accurate. The main disadvantage of the Markov model is that it presents a numerical solution rather than a closed expression. Hence, the use of both models presents a more complete view of the system’s performance. In the following, for reasons of space, we present only results from the Markov model, and for the number of peers.
In summary, the equations obtained by the fluid model are well suited in abundance conditions, which usually entails a high number of peers. The great advantage of this mathematical tool is that it renders close expressions for the number of seeds and leeches in the system. On the other hand, with the Markov Model we can analyze any system in any condition. However, the system is solved numerically.
We now compare the cellular (m + = m −) and WLAN (m + = 2m −) environments for different values of the seed’s departure rate, γ, leech’s departure rate, θ, and peers arrival rate, λ, as shown respectively in Fig. 13. For these results, the following parameters were used: c = 0.002, µ 1 = 0.00125, λ = 0.04, m + = 0.002. For the Cellular scenario m − = 0.002 and for WLAN m − = 0.001. Also the case where nodes are fixed is considered, i.e., m + = m − = 0.

Fig. 6. Number of seeds with the priority scheme enabled for the Cellular and WLAN environments for different values of γ and θ

Fig. 7. Average number of seeds and leeches in zone 1 for WLAN environment for different values of γ and θ

Fig. 8. Average number of seeds and leeches in zone 2 for WLAN environment for different values of γ and θ

Fig. 9. Average number of seeds and leeches in zone 3 for WLAN environment for different values of γ and θ

Fig. 10. Average number of seeds and leeches in zone 1 for Cellular environment for different values of γ and θ

Fig. 11. Average number of seeds and leeches in zone 2 for Cellular environment for different values of γ and θ
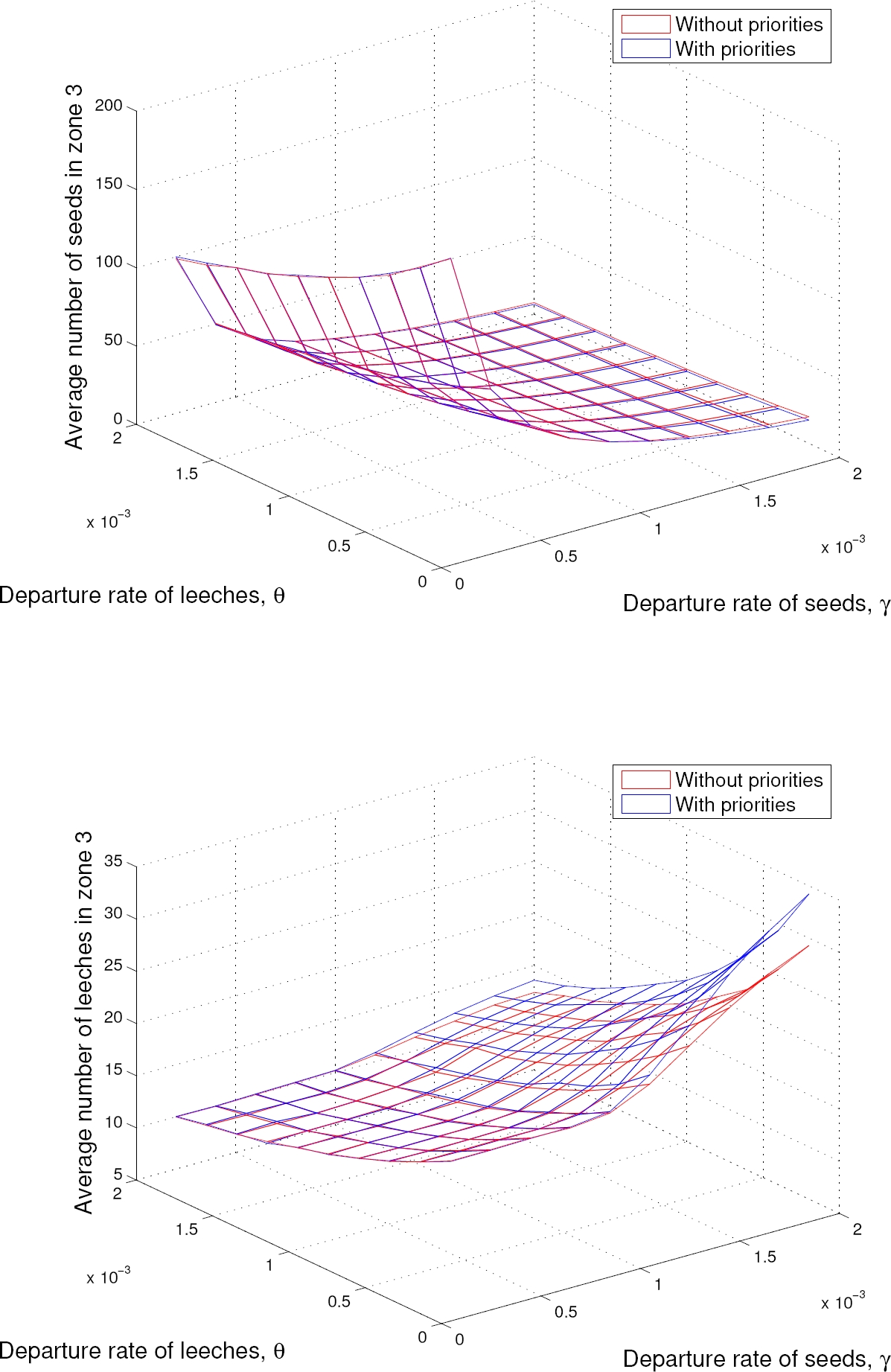
Fig. 12. Average number of seeds and leeches in zone 3 for Cellular environment for different values of γ and θ

Fig. 13. Comparison of Cellular, Fixed and WLAN environments for different values of a) γ b) θ and c) λ
Note that the fixed and cellular environment have a very similar behavior for any conditions of the system, i.e., nodes do not benefit from the existence of better coverage zones. On the other hand, in the WLAN environment, nodes can improve their channel quality, which in turns improves the overall system performance, as seen by the higher number of seeds in the network. This is not as clear when γ is increased, since the number of seeds drastically decreases when γ is high. This result shows the importance of node’s cooperation in P2P networks.
Now, we investigate the impact of the node’s mobility on the system’s performance. Since in a cellular system, users are typically unaware of the placement of the BS, nodes in a bad coverage zone cannot move to a better zone explicitly. As such, we focus our attention on the WLAN environment. In this case, we consider different ratios for users moving closer to the AP compared to users moving away from the AP. As such, we define this ratio as r = m +/m −. From these results, it is clear the big impact of a directional mobility of nodes (towards better coverage zones) has on the system’s performance. As r increases, the number of seeds in the good coverage zone also increases rapidly (around 42% from r = 2 to r = 5).
However, after r = 5 there is no longer such a high increase. The reason for this is that for high values of r (r > 5) almost all the nodes are already in zones 1 and 2 and there are almost no peers in zone 3. This implies that r does not have to be too high in order to obtain a good system performance. In Fig. 4, the number of seeds in the three coverage zones are presented for different values of r.
Then, the effect of the priority scheme is analyzed. From Figs. 7 to 9 the average number of seeds and leeches respectively are shown for WLAN environment. In zone 1, it can be seen that when the system is in penury (when the resources are scarce), i.e., high values of θ and/or γ, there are more cooperative seeds and less cooperative leeches with the priority scheme enabled. Note that more seeds means more resources. In zones 2 and 3, there are more cooperative leeches and almost the same amount of seeds. The fact that there are more seeds means that more users complete their downloads successfully, and fewer leeches means that the users complete their downloads in less time.
From Fig. 10 to 12 the average number of seeds and leeches respectively are shown for the Cellular environment. As in the WLAN scenario, It can be seen that when the system is in penury (when the resources are scarce), i.e., high values of θ and/or γ, there are less leeches with the priority scheme enabled in zone 1. Hence, the system has a better performance with the priority scheme than without it. Also, it can be seen that in abundance condition, i.e., low values of θ and/or γ, the effect of the priority scheme is almost null. This is an important result, since it is desirable that the priority scheme has the higher impact when the resources are scarce.
3.1 Priority Scheme
In this section, some relevant results are presented for the priority scheme for mobile nodes in both scenarios: Cellular and WLAN. For these results, the following parameters are used: c = 0.002, µ 1 = 0.00125, λ = 0.04, m + = 0.002. For Cellular scenario m − = 0.002 and for WLAN m − = 0.001.
First, we compare both scenarios, WLAN and Cellular. From Fig. 14, we can see that in the WLAN scenario there are more leeches than in the Cellular scenarios, this is because in WLAN networks there are more peers in zone 1 than in Cellular networks because in WLAN the users try to get close to the AP to get a better connection.

Fig. 14. Number of leeches with the priority scheme enabled for the Cellular and WLAN environments for different values of γ and θ
From Fig. 6, we can see that in the WLAN scenario there are more seeds than in the Cellular scenario, this is because in WLAN networks the users tend and are able to move to better zones of coverage much more easier than in Cellular networks. Therefore, in WLAN networks there are more users in the best zone which in turn diminish the download time since in this scenario, there are more resources. For space reasons we only present the peers in zone 1.
4 Conclusions
In this paper, the effect of the quality of the wireless channel and node’s mobility in pedestrian and vehicular networks are studied and analyzed. We analyzed the node’s mobility through different scenarios and using two different mathematical analyses: First, we obtained a set of closed equation that can describe the system in abundance conditions. Additionally, we developed a Markovian model that is able to describe the system in any condition, but this model can only be solved numerically. We compared these two models and we found that in fact, the best match occurs when the system is in abundance, thus validating our assumptions.
Also, it is shown that the priority scheme proposed can improve the performance of the system when the resources are scarce and it has a minor effect when there are enough resources. As such, the use of these types of priority schemes can indeed improve the performance of the system.
As future work, different performance para-meters like delay, and percentage of successful downloads can be considered, as well as different probability distributions can be used to model these kind of systems.











 nueva página del texto (beta)
nueva página del texto (beta)