1 Introduction
A Peer-to-Peer (P2P) network is a distributed network with dynamic nodes, called peers. The peers in the system provide resources such as bandwidth, storage space, computing power, with the objective of exchange the data or of performing some collective task. In recent years, P2P systems have received a great amount of attention since applications based on these types of networks are dominating a considerable part of the traffic in the Internet, as noted in [4, 5]. Specially for TV streaming applications (live or stored), as studied in [6] and [7]. Indeed, a big effort has been done to implement IPTV services which consume high amount of bandwidth [8,9].
As such, a P2P architecture can be a good alternative for such services in future networks. One great advantage of a P2P system over conventional client/server applications resides in its robustness. This is because the data is no longer concentrated in one central entity such as a server; instead, they are distributed over the population of users.
Another advantage is scalability. This is due to the fact that all peers in the system share their resources and any new arriving peer, while increasing the demand, also increases the overall system’s capacity.
One basic disadvantage is that P2P networks suffer form the total absence of control on content distribution, as they are running on PCs and are managed by the users themselves. Users’ PCs are unmonitored, not secure, and almost impossible to control by a network provider (we exclude here the case of managed networks, that is, of networks belonging to some telco or ISP).
In this work, we focus on file distributing networks, and on the harmful effect caused by peers that enter the system and begin the file downloading process but leave before finishing it or just after finishing their own download. Hence, resources can be assigned to a peer that is not staying long enough in the network to cooperate with the rest of the users, that is, leading to a waste.
We explore here a reward-based P2P network where the peers that have a high probability of staying in the system long enough to share the file are served first. This mechanism is in part encouraged by the results presented in [1], where it is shown that in a cooperation game, rewards are as effective as punishments for maintaining cooperation. Also, the use of rewards leads to higher total earnings.
Applying this philosophy to a P2P network, our priority scheme rewards the peers that have a high delay tolerance to download and share the file. On the other hand, the peers that waste the system’s resources by leaving immediately after downloading their file or even before downloading the complete file are not punished in any way, they are just not rewarded. In fact, when the system has enough resources, the priority scheme does not affect the low tolerant peers at all. For this priority scheme, the BitTorrent application has been chosen.
As an additional contribution of this work, different transfer rate distributions are considered for the uploading and downloading bandwidths. The exponential model for the upload and download rates is a simple model that has the advantage of allowing a simple mathematical analysis. However, one big disadvantage is that it does not closely match a practical P2P network. This is because the exponential distribution has a very high variability. Hence, while it is a good approximation for arrival and leaving rates of nodes into the system, upload and download rates are not expected to have such a high variability. In some cases, these rates have been considered to be constant [14]- [17]. In this work, we are particularly interested on the limit case where the transfer rates are constant. This case can be used to model a managed P2P network where the communicating devices are provided by the service providers such as Internet and television services. In managed networks, the system’s parameters are typically under tighter control than in unmanaged networks. Hence, even the rates of aborting the download or leaving the system after the download can also be adjusted by the service providers. We only focus the discussion on the transfer rates and we leave the study of the impact of the departure rates on the system for a future work. Finally, the priority models are also studied for the constant transfer rates an compared to the exponential case.
For the priority scheme implementation and the study of the performance of the system with different bandwidth models, the BitTorrent application has been chosen.
1.1 BitTorrent
BitTorrent is a P2P application used to facilitate the download of popular files. The main idea is to divide the files into several pieces called chunks. To download a file, peers exchange these chunks following some rules.
The BitTorrent protocol differentiates two types of peers: leeches, which are peers that have a part of the file or not data at all, and seeds, which are those peers having downloaded the complete file and remaining in the system to share their resources. Both leeches and seeds cooperate to upload the file to other leeches. Whenever a peer joins the system with the objective of downloading the file, it contacts a particular node called tracker which has the compete list of peers that have part or the complete file. Then, the tracker returns a random list of potential peers that might share the file with the arriving peer. At this point, the downloading peer contacts the peers on the list and establishes which chunks it is willing to download from each peer it is connected with. The decision of which peers to upload to depends basically on how much chunks have downloaded the peers in question. Hence, the peers that have downloaded the most are the ones that have priority over the peers that do not share their chunks, discouraging the free riders (peers that only download but do not share their data).
1.2 Contributions
— This paper proposes two simple priority schemes to serve first the peers that are statistically more likely to remain in the system until the download of the file is completed, and analyses the performances of both proposals. Priority schemes have not been the subject of significant research efforts so far, in this area. A simplified model of a P2P network is given, with the objective of understanding some aspects of the behavior of such a system. For implementation purposes, we chose the BitTorrent application since the tracker has access to all the necessary statistical information about the peers in the system. Specifically, the tracker can inform the rest of the peers about the average time that a leech remains in the network. We also study the conditions under which the priority schemes may be useful.
— The impact of different distributions for the transfer rates on the performance of the P2P system is analyzed. In particular, we are interested on the effect of the variability generated by the different rate distributions. Hence, the exponential distributions and the constant value models are considered. The mean and variance of the number of peers in the system as well as the downloading, waiting and life time of leeches are considered as performance metrics of the system.
The rest of the paper is organized as follows. Section II reviews the previous works related to mathematical modeling and incentives in P2P networks. Then, section III specifies the system model and assumptions, including the analysis of the system’ conditions where the priority schemes are suited, the models used in this work and the simulation model. Following this, section IV presents the relevant numerical results in order to evaluate the impact on the distribution of the transfer rates and the priority based mechanisms proposed in section III. The article concludes with a summary of our conclusions and contributions.
2 Related Work
We built our priority model based on [2], and using also [3, 4, 13]. Unlike these works, we consider a two-population model. Additionally, a priority mechanism is proposed and studied by means of a fluid simplification and a Markov chain. Fluid models as the one in [2], allow simple analytical discussions. We complete the analysis with a Markov chain model such as the one presented in [13] to get better insight into the performance of the system. In [12], two classes of users are considered, namely: high bandwidth users and low bandwidth users. This is done in order to approximate a real system where different users have different hardware characteristics. Unlike [12], we focus on the behavior of the different peers during the downloading procedure rather than the different bandwidth capacities that can be encountered in a real network. Moreover, an event simulator is implemented to study a managed P2P network where the transfer rates are considered to be constant. This model can no longer be studied using neither the Markov chain nor the Fluid model.
Additionally, unlike previous works, we consider two priority based schemes which are different from the general idea of incentives such as [10, 11]. While the incentives are used as means of influencing a certain behavior in the peers any time the peers are connected to the network, our proposal is used only when the resources in the system are scarce. Meanwhile, when resources are sufficient in the network, there is no need to apply the priority scheme. In other words, the priority schemes can be seen as a means of improving the performance of the system whenever the environment is adverse in terms of insufficient upload bandwidth. However, the incentive mechanisms can work in parallel with the proposed priority schemes in order to further improve the system’s performance. This issue is left to further future analysis. The priority schemes are studied for both the exponential model and the constant model.
In [14]- [17], a constant value on the transfer rates is considered. In [14, 16] an arbitrary value is assumed while in [15] different values on the upload and download rates are considered accor-ding to different system’s conditions. However, no further details on the nature of these rates nor a more detailed description is given. In contrast, in this work, we investigate the impact on the system when considering constant data rates (as the works previously described ) and random variables with exponential distribution as in [2] and [13].
3 System Models
First, we briefly describe the fluid process used in [2] for the single population model and then, the proposed two population and priority models. The system parameters used throughout the paper, unless specifically stated otherwise, are presented in Table 1 [2].
Table 1 Parameters setting
| Parameter | Description | Value |
|
|
Arrival rate | 0.04, 0.4, 4 |
|
|
Downloading bandwidth | 0.002 |
|
|
Uploading bandwidth | 0.00125 |
|
|
Departure rate for Seeds | 0.001 |
|
|
Departure rate for Leeches | 0.001 |
| F | File size | 1 |
3.1 Single Population Models
The mathematical models presented in this section are a simplification of a BitTorrent-like network. Indeed, the real system is much more complex due to the numerous parameters and details involved in the file searching, node selection, and chunk selection procedures, among others. Specifically, the mathematical models assume that whenever a peer arrives, it is immediately served by the rest of the peers in the network, i.e., the total uploading bandwidth is uniformly distributed among all users in the system. Another important assumption is that all the peers in the system cooperate, or that all users have chunks that are of interest for the rest of the peers. This is a very important problematic that has been extensively studied before (for instance in [13], the effectiveness of the file sharing is studied with a parameter
New peers arrive to the system according to a Poisson process having rate
Observe that in these equations, stated in [2], the condition
In [2], this dynamical system is analyzed and its equilibrium point, denoted by
where
Consider now the evolution of the pair
This Markov chain is analyzed using simulation. Concerning its stability, it is easy to see that it is always stable by seeing the model as a tandem of infinite server queues, the first one containing the leeches, the second one the seeds. The second one is a simple
For the priority scheme, it is important to identify the system’s condition where the bandwidth is scarce due to the low number of peers. Then, numerical values of the number of seeds and leeches in equilibrium are obtained from both the Markov model and the fluid model. It can be seen from Fig. 1, that the Markov model (referred as simulation) achieves a very good match to the closed expressions presented in (3), when
In Fig. 1, we can see that when the departure rate of leeches is high, both the number of seeds and the number of leeches is low. This is because most of the peers that enter the system leaves in a small amount of time and there are almost no leeches that convert into seeds. Conversely, when the departure rate of seeds is high, the number of leeches does not decrease since there are still other leeches in the system who share the file with the rest of the peers. The number of seeds does not decrease as drastically as in case of high values of
3.2 Two Population Model
For the two population model, the behavior of two types of users is considered: cooperative leeches (also called high tolerance leeches) and defeat leeches (also called low tolerance leeches). For the former, they are peers that arrive to the system and usually stay throughout the entire download procedure. In other words, they have a high tolerance for download latency. Therefore, their departure rate
According to this, the fluid model presented above is extended for the two types of leeches as follows:
with the additional notation
The Markov chain presented in the previous subsection is also extended according to the two new 2-class model. The new model is the triple
3.3 P2P Network Simulation at Peer level and Constant Time Rates
In this section, the event simulation model at peer level is discussed in detail. The main objective of this simulator is to study a managed P2P network where the transfer rates are constant. Additionally, it allows to verify the results derived form the mathematical models and to obtain different performance metrics in order to have more insight of a P2P system.
As such, the simulations are performed as close as possible to both the Markov and Fluid models but without some important assumptions. Specifically, the aforementioned models consider that all the peers, from the moment of the arrival of the peer to the moment of the peer departure, always cooperate to share the file in the system. Conversely, the simulation considers that the peers can only share the file once it has downloaded the file. A more detailed simulation, considered for future work would consider the sharing of the file once it has downloaded at least some chunks of the file.
Another important difference is that, the simulator considers that whenever the active peers are uploading the file to other peers, they upload at the maximum rate
The pseudo-code of the event simulator is presented in Algorithm 1. Four types of events are considered: Arrival of a new peer, End of the download of the file, Departure of a Leech, and Departure of a Seed. Each arriving peer is assigned an individual and particular identifier id. Hence, in the pseudo-code, the identifier of the peer that is being attended according to the different events is referred as id. And the identifier of the peer that is uploading the file is referred as idupload.
In the peer arrival event, the new peer looks for an idle peer, i.e., a peer that is not uploading the file to any other peer. Indeed, since a peer that shares the file uploads at the upload rate
An additional advantage of this event simulator is that it allows the use of different distributions for the time variables. In particular, we want to investigate the system when the transfer rates are constant. The interest of fixing the download and upload rates to constant values, is that it models one important aspect of managed P2P networks. As such, it is possible to evaluate the impact of the priority schemes on these systems. Indeed, in a managed P2P network, the service providers use their own devices which typically have the same upload and download rates. This is an important difference compared to the case of a more general P2P system, where users typically use their PCs or mobile devices (laptops, smart phones, etc.). It is clear that these devices have very different capabilities for both hardware and software. Also note that the Markov model and Fluid model are no longer valid in this case. Finally, the implementation of the constant model in the simulator is straightforward.
4 Priority Models
Two different priority schemes are proposed. In the first scheme, the leeches that are more likely to remain longer in the system are served first over the leeches that in average leave earlier. In the second scheme, the seeds that are more likely to remain in the system are served first over seeds that leave earlier.
4.1 Priority Scheme for Cooperative Leeches
As stated before, the basic idea of the first proposed priority scheme model is to first share the file with the high tolerance leeches in case of penury conditions. It is important to notice that there can be two cases of penury. The first one occurs when the uploading bandwidth is not enough to serve at the maximum capacity all peers in the system but it is enough to do it for all thebcooperative leeches. In this case, the remaining bandwidth is shared among the defeat leeches. The second penury case corresponds to the situation where the uploading bandwidth is not enough to serve the cooperative leeches at maximum capacity. In this case, the defeat leeches are not served at all and the uploading bandwidth is only shared among cooperative leeches. In view of this and based on (4)-(6), the value of
Let us first focus on the case of abundance. In this condition, the equilibrium values for the number of leeches and seeds in the system are the same as the equations for the two population model in case of abundance, i.e., (7), and (8) with
where
Finally, for the second penury case where there is only available bandwidth for the cooperative leeches, i.e.,
4.2 Priority Scheme for Cooperative Seeds
In this second scheme, the peers that are statistically more likely to remain in the system longer once they have downloaded the file are served first over the peers that defeat once they become seeds. For this model, the number of cooperative and defeat seeds have to be considered separately. Therefore, the two population model presented before has to be extended accordingly. It is important to emphasize the difference between this priority scheme and the priority scheme for cooperative leeches. In the later, each peer is studied regarding their behavior as a leech and the leeches that are statistically more likely to rest in the system are classified as cooperative peers. These peers who have a high probability of staying in the system throughout the download procedure are served first in case of penury. For the former, each peer is studied regarding their behavior as seed and the ones that are statistically more likely to remain in the system as seeds are classified as cooperative peers.
These cooperative peers are served first in case of penury. As such, in the priority scheme for cooperative leeches, the peers are classified as having a high download aborting rate
First, the two population model with no priorities is presented. The fluid model presented above is extended for the two types of peers as follows:
with
However, the case of penury
The fluid model with priorities is basically the same as the model with no priorities except for the rates
The system in penury only for the defeat seeds is studied through the Markov model and the discrete event simulator due to its complexity. Similarly, the Markov chain is only modified in the following transition rates:
5 Numerical Results
In this section, we present some relevant results regarding the mathematical models and simulation results of the P2P networks studied above. We first present results considering exponentially distributed random variables to model the upload and download rates. Then we compare these results to the model where constant upload and/or download rates are used in the single population model. Also, we consider fixed transfer rates more suited to model a managed P2P system. Following this, the two population model is numerically studied. Finally, the priority models are extensively analyzed and discussed.
5.1 Exponential Distributed Download and Upload Rates
In this subsection, the exponential distributed model for the transfer rates in the simulation at peer level and mathematical models are considered. Recall that the simulation under the exponential model is constructed in order to recreate as close as possible the scenario considered by the Markov and Fluid model presented above, i.e, the download and upload rates are modeled as exponentially distributed random variables with mean
In Fig. 2, the evolution in time of the number of leeches and seeds normalized by the arrival rate is presented. It can be seen that there is a very good match between the simulation at peer level results compared to the fluid model, specially for high values of

Fig. 2 Evolution in time of the number of Leeches and Seeds in the network, Simulation at peer level vs Fluid Model
In Fig. 3, the average download (time since the arrival of the peer to the instant that the complete file is downloaded), waiting (time form the arrival of the peer to the moment of the leech departure before downloading the complete file) and life time (time form the arrival of the peer to the moment when the peer either completes de download of the file or leaves the system aborting the download) as leech and the proportion of successful downloads is presented. Various interesting observations can be made from these results.
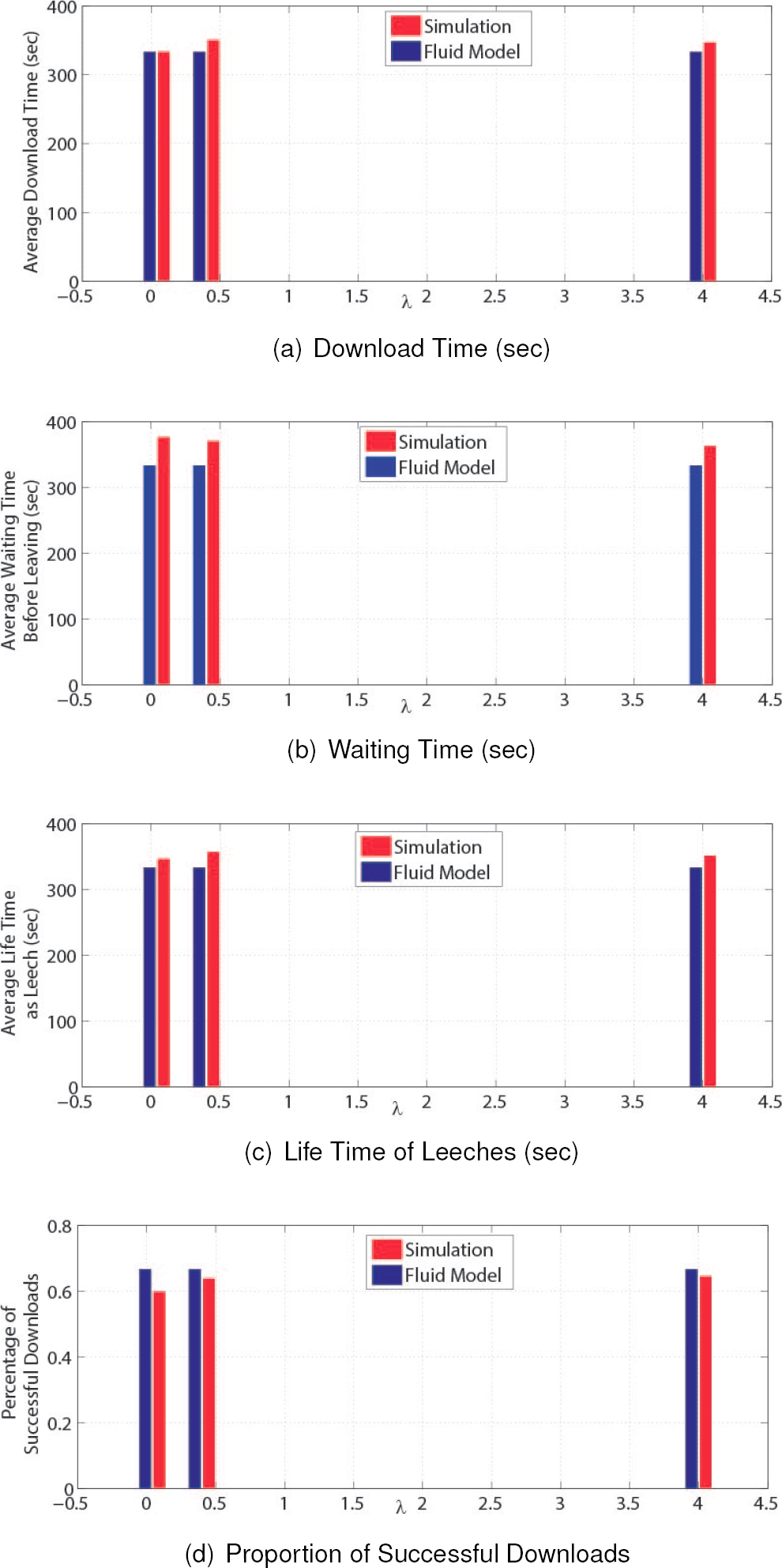
Fig. 3 Average Download, Waiting, Life Times for Leeches (sec) and Proportion of Successful Downloads
First of all, it can be seen that the analytical average times derived analytically (under the fluid model), are always the same, independent of the arrival rate. The reason for this can be explained as follows: Any leech can either leave the system either because it abandons the download, with rate
A second observation is that the simulation results show a slightly higher average times compared to the analytical results. The reason for this is that, in the analytical model, whenever a new peer arrives, it is assumed that it immediately starts to share the file with other peers and at the same time it begins to download the file. On the other hand, the simulation considers that whenever a new peer arrives, it can not upload the file to other peers since it has not yet downloaded the file. And also, if the rest of the peers are already uploading to other peers and there is not an idle peer, it can not start the download of the file. Hence, the download time is slightly higher. And because leeches spend more time in the network before becoming seeds, there is a higher chance of quitting the download, therefore the waiting time is also incremented and consequently the average life time as leech also increases compared to the analytical model. These observations are further reaffirmed by observing the probability that a leech successfully downloads the file in Fig. 3 (d). In the analytical model the probability that a leech becomes a seed is simply
5.2 Fixed Download and Upload Rates for Single Population Model
In this subsection, the results when the transfer rates are constant instead of random variables are presented and compared to the exponential model. In Fig. 4, the number of leeches and seeds normalized to
It can be seen that by leaving any of the transfer rates constant, the number of leeches is higher than the exponential model and consequently, the number of seeds is smaller. In particular, when both
Indeed, it is clear form these results that the exponential model allows a fastest download time and corresponds to an optimistic model for a P2P network. Hence, the average time that a peer stays as leech in the system is also the highest when the transfer rates are fixed as observed in Fig. 7(c) and also, the successful download percentage is the lowest for the same case observed as seen in Fig. 7 (d).
Another interesting observation is that for the case where
5.3 Two Population and Priority Models for Exponential Transfer Rates
In this section, the performance of the proposed priority mechanisms are evaluated.
5.3.1 Priority Model for Cooperative Leeches
For these results, different portions of high tolerance leeches are considered, ranging from 1% through 90% of the total leech population. Also, two different system conditions are considered: abundance, where the number of seeds in the system is high enough as to have most of the time all leeches downloading at the maximum capacity. As such, a value of
The case of abundance can be seen as a case where most peers remain in the system even after the download of the file in order to cooperate with the file download. And the case of penury can be seen as the case where once the file is downloaded, the peers almost immediately leave the system. It is important to keep in mind that seeds’ behavior analysis is a different issue than the one investigated in this work. Recall that we are focusing on the behavior of the leeches while they are downloading the file, i.e., if they have a high probability of aborting the download or not. Nevertheless, this priority scheme can also be implemented focusing on the behavior of the seeds, which we plan to study in a future work.
Another important remark about the results presented in this section is that, as stated in [2], the fluid model is more accurate when the arrival rate
In Fig. 8, the normalized equilibrium values for the number of leeches and peers under the proposed priority scheme is presented using the fluid model when

Fig. 8 Normalized Equilibrium Number of Leeches and Seeds for Different Portions of High Tolerance Leeches, Fluid Model, Abundance
The normalization is made with respect to

Fig. 9 Normalized Equilibrium Number of Leeches and Seeds for Different Portions of High Tolerance Leeches, Markov Model, Abundance
Indeed, the priority scheme has no impact on the system when the uploading bandwidth is high enough as to allow all leeches to download at the maximum capacity
In Fig. 10, the probability that a leech successfully downloads the file is presented. Again, there is no difference between the conventional system and the system with the priority scheme enabled. It is important to notice that as the number of high tolerance leeches increases, the probability of successful download also increases.
This is because high tolerance leeches remain longer in the system and have a high probability of remaining throughout the whole downloading process. Conversely, when the fraction of high tolerance leeches is low (for example
In penury conditions, the priority mechanism has a visible impact on the system since, in that case, high tolerance leeches are served first. For instance, Fig. 11 shows the normalized equilibrium value of the number of leeches and seeds for

Fig. 11 Normalized Equilibrium Number of Leeches and Seeds for Different Portions of High Tolerance Leeches, Fluid Model, Penury
This effect is more visible when there is a high portion of high tolerance leeches in the system, since in this case there is more cooperation among peers. Therefore, there are more leeches that download the file and become seeds. This is “paid” by the low tolerance leeches that are not being served and leave the system before having a chance of downloading the file.
This observation is reinforced by observing the results in Fig. 13 (a) which shows the probability of successfully downloading the file. It can be seen that for different values of

Fig. 12 Normalized Equilibrium Number of Leeches and Seeds for Different Portions of High Tolerance Leeches, Markov Model, Penury
Conversely, the probability that a low tolerance leech downloads a file is almost zero. Recall that low tolerance leeches are not rewarded, but notice that not rewarding the low tolerance leeches is different from being punished. The difference is that the peers are not wasting resources in punishing these leeches, they are just ignoring them whenever the system is in penury conditions. Since the low tolerance leeches are not likely to remain in the system throughout the complete download process, the global resources are better used by serving first the more tolerant users. Also, the less tolerant leeches do not get served unless there are enough resources in the system, and they are more likely to abort the download reducing significantly the successful download probability.
Notice that the results from the Fluid Model in Fig. 11 are validated by the results from the Markov model presented in Fig. 12. Observe that there is a better fit between these two models when
Finally, the total successful download probability is presented in Fig. 13 (b). In this case, the percentage of leeches (both high and low tolerance) is lower when the priority scheme is enabled compared to the conventional system. The reason behind this is that, as already stated, the high tolerance leeches are rewarded by serving them before the low tolerance ones.
Hence, these low tolerance leeches, which already have a low latency tolerance, are more prone to leave the system. That is, for the conventional system with the priority scheme disabled, the probability that some low tolerance leeches download the file is not zero because the peers cooperate with any leech independently of its tolerance to the download delay. As such, the probability that a leech in general downloads the file is higher when no priority scheme is being used.
5.3.2 Priority Model for Cooperative Seeds
In this section, the case where the cooperative seeds are served first is discussed in detail. For these experiments, the system parameters are:
Let us first discuss the Markov model. In Fig. 14 the normalized (on

Fig. 14 Number of Peers for Different Portions of Cooperative Peers, Priorities for Seeds,

Fig. 16 Number of Peers for Different Portions of Cooperative Peers, Priorities for Seeds,
We now consider the simulation’s results. The performance of the system under the two priority schemes is presented For
On the other hand, for the second priority scheme, the two classes of seeds is shown. From these results it is clear that as the number of cooperative peers increases, also the total number of seeds increases. This is because the peers rest in the system longer times either as leeches, completing a higher number of downloads, or as seeds, remaining longer times after the download.
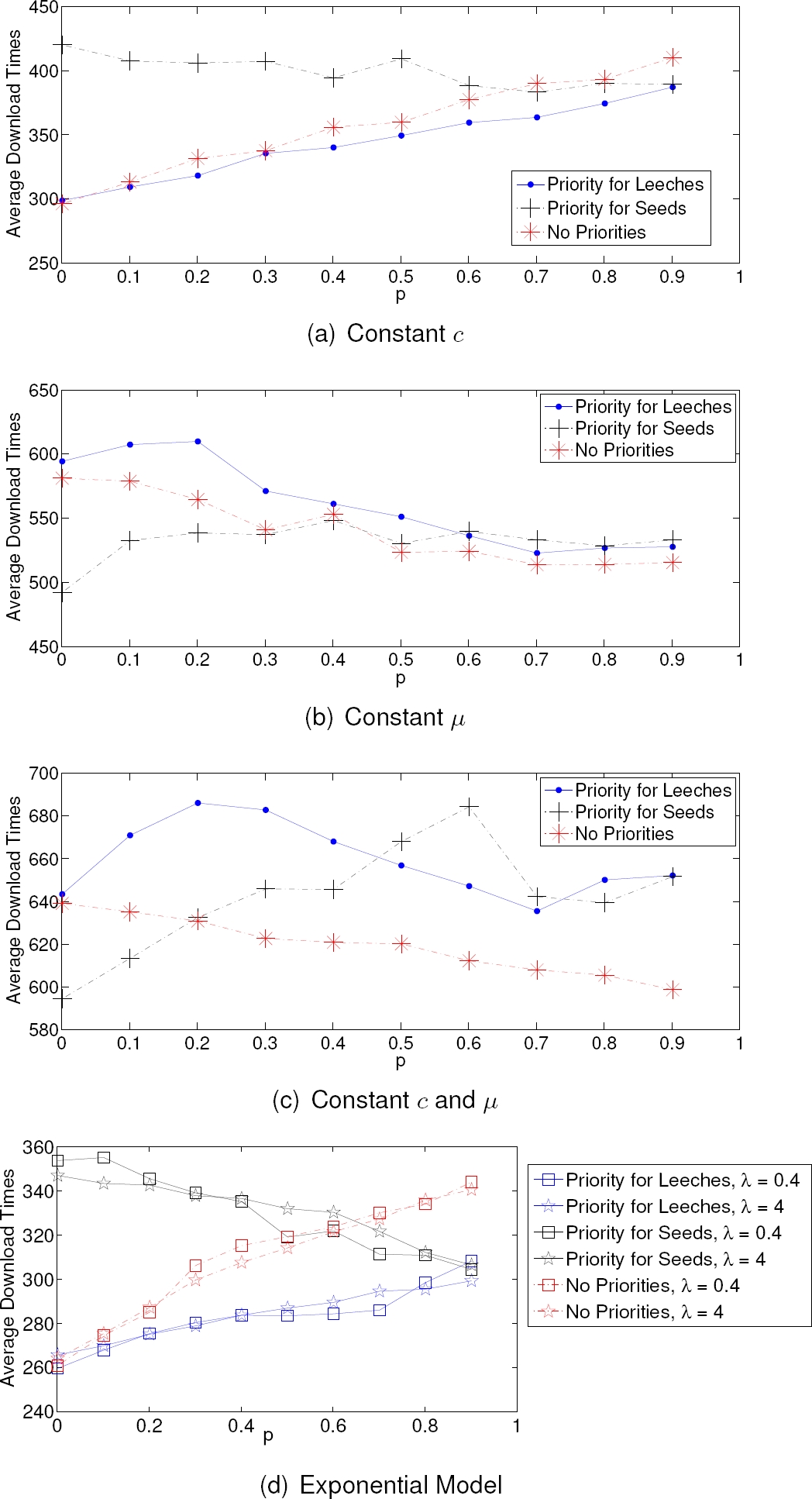
In Fig. 20, the average download time for the two priority schemes and the system with no priorities is presented. for reasons of clarity, only the results for
For the priority scheme that favors the coopera-tive leeches, the download time is higher because it only benefits the peers that stay longer during the download procedure. However, these peers may quit the system almost immediately after downloading the file. As such, it is more profitable to benefit the peers that stay longer sharing their resources once they complete their download than favoring those who are more likely to stay throughout the download but may act selfishly afterwards.
Also, when no priorities are enabled in the system, the average download time is the highest. The highest download time for the defeat peers corresponds to the priority scheme that favors the cooperative seeds. Again, this is due to the fact that defeat peers are only served after the cooperative peers are served. Hence it takes more time for them to download the file. One important issue is the total download time in the system.
It can be seen that the priority scheme for the cooperative leeches achieves the lowest download times for all peers in the system while the priority scheme for cooperative seeds achieves a low download time only after a certain number of cooperative seeds are in the system.
The rationale behind this can be explained as follows: when the cooperative seeds are favored and the number of cooperative seeds is low, the system serves first these few peers which does not have a great impact on the system since most of the seeds quit the system very fast after their download.
Hence, the download time for the rest of the peers (which are defeat seeds) is high. As the proportion of cooperative peers increases, the probability of having cooperative seeds in the system increases, reducing also the download time. For the case when the cooperative leeches are favored, when the number of cooperative peers are in the system the download time is low since the model considers that all seeds remain in average the same amount of time
In Fig. 21, the proportion of successful downloads for the two priority schemes and the total number of downloads is presented. In the case of the cooperative peers, the scheme that achieves the best results is the one that favors the cooperative leeches, as it is shown in Fig. 21 (a). Conversely, for the defeat peers the priority scheme that benefits the cooperative peers achieves the highest proportion of successful downloads. Also, this scheme obtains the highest total proportion of successful downloads for all peers in the system. Indeed, as the system serves first the peers that as seeds stay longer in the system, all peers benefit from having a higher probability of finding a peer with the complete file willing to cooperate. As such, the proportion of total successful downloads is higher.
On the other hand, for the cooperative peers, the scheme that benefits the seeds that remain longer has the lowest proportion of downloads specially for low concentration of cooperative peers. This is because there is a high number of non cooperative peers which leave the system almost immediately after downloading the file. In the same conditions, the priority scheme that benefits the cooperative leeches, considers that all seeds have the same rate
5.4 Two Population and Priority Models with Constant Transfer Rates
In this section, the effect of the constant transfer rates are discussed in detail. The cases where the download and/or the upload rates are constant are considered. For these experiments the system parameters are as follows:
It can be seen in Fig. 22 that in the system where
Also, from these results, it can be seen that by considering only
Conversely, when
Therefore, the impact of the model of the transfer rates is independent on the system’s conditions. It is worth noting that the priority schemes are no longer effective when
Similarly, for the probability of successful download, a similar effect is presented as shown in Figs. 24 and 25. First, this probability is lower for the all exponential case. Second, the case where only
Again, we conclude that the parameter
6 Conclusions
This work has focused on studying the benefits of serving first the peers that have a high download delay tolerance over peers that have very low tolerance. The resulting P2P networks have been modeled, simulated, and studied. The model developed describes a BitTorrent-like network. It calculates the number of leeches and seeds in the system in equilibrium and the probability of successful download for different system conditions.
The results are obtained using both a simple fluid model and a Markov chain model. It has been shown that the priority schemes are well suited when the uploading bandwidth in the system is scarce.
As such, it prevents for resources wastage by attending first the leeches that are more likely to become seeds as well as the case where peers that are more likely to remain longer in the system once they become seeds are served first.
Consequently, these cooperative peers can share their resources with the rest of peers. It is important to mention that the BitTorrent application is considered in this work for reasons of simplicity.
However, the proposed priority mechanism can be applied to other P2P applications. Also, since the objective of this work is to study the potential benefits of rewarding cooperative leeches in P2P networks, it can be used as a guideline for future practical implementations.
This work also studies different models for the transfer rates,
Also, it can be seen that the parameter
In further work, we will exploit more in deep these models by proposing different distributions for the transfer rates and we will extend them to analyze other factors of global performance not considered here, such as the abort download rate θ and seed’s departure rate










 text new page (beta)
text new page (beta)