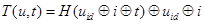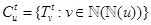1 Introduction
Wireless networks such as sensor networks or mobile ad hoc networks (MANETs) are usually composed of networked devices that rely on batteries and hence energy consumption is one of the most important aspects that designers have to consider when developing new protocols across the whole communication stack [23, 25, 14]. Practical studies [22, 5, 6] have established that the network interface is one of the most energy hungry components of a mobile device [7]. In this regard, Ye Wei et al. [25] identified collisions, overhearing, control packet overhead and idle listening as the major sources of energy waste. Therefore, reducing any of these four parameters will decrease the energy consumption in a wireless device. This calls for improved medium access control (MAC) protocols capable of efficiently managing the radios of the wireless nodes so that they are in receiving or transmitting state only if their are going to either successfully transmit or receive a data packet as an intended receiver.
Given the importance of having energy and bandwidth efficient MAC protocols, many propos-als that address these design goals have been proposed up to date. Unfortunately, as shown in Section 2, most of current proposals either make strong assumptions about the nature of the data flows (e.g., [25]) or explicitly publish future network channel access plans (e.g., [14, 13]). The first approach has the disadvantage of restricting the MAC protocols to particular scenarios, while the second tends to incur in excessive control overhead.
In this paper we introduce EE-MA (Energy-Efficient Multiple Access), a novel MAC protocol based on distributed elections [24, 2] implemented by means of a dispersion hash function. In EE-MA, time is slotted and at each time slot, nodes with a winning ticket can access the channel in an interference-free fashion. When a node doesn’t have a winning ticket nor it is the intended receiver of a node with a winning ticket, it switches its radio to sleeping state to avoid idle listening and save energy [22].
The remaining of this paper is organized as follows. Section 2 presents a sample of the large body of work on MAC protocols for wireless networks. Section 3 introduces the system model and formally states the problem. Section 4 presents a formal specification of EE-MA and a set of theorems that establishes the protocol’s correctness, namely, that it provides interference-free access to the channel and that whenever a node is the intended receiver of a winning ticket, it will be in receiving state. Section 5 presents a set of simulation-based experiments that show that EE-MA outperforms NAMA [2] in terms of energy efficiency while maintaining adequate channel access delay and goodput. Lastly, Section 6 presents our concluding remarks.
2 Related Work
MAC protocols are used when more than one device want to transmit using the same wireless channel. They can be divided into contention-based and conflict-free channel access protocols [18]. In the earlier, there is no guarantee that a transmission will be successful, while in the later, when a node transmits, no other node can interfere with the intended receivers. Conflict-free protocols can also be divided according to their channel allocation scheme into static and dynamic. In the static allocation case, nodes have an a priori agreement over the portion of the channel that each node will use. Examples of such protocols are TDMA, FDMA and CDMA [21]. In the case of the dynamic allocation schemes, nodes can dynamically change the portion of channel they use with the objective of optimizing channel utilization. Dynamic allocation protocols can be further divided into reservation-based and token passing protocols according to the way they allocate bandwidth. In the earlier approach, nodes must explicitly tell other nodes that they will use a given portion of the channel [8, 11], while in the latter, only the holder of a token can transmit [2, 1, 14, 13].
In [2] Bao and Garcia-Luna-Aceves proposed NAMA and LAMA which are TDMA-based MAC protocols that compute channel access plans for accessing the channel in broadcast (NAMA) or unicast (LAMA) mode. Similar to the proposed protocol, for each time slot NAMA and LAMA assign priorities to nodes or links using a hash-based distributed election. When a node has the highest priority over it’s two hop neighbors, it transmits. A disadvantage shared by NAMA and LAMA is that nodes are always in either receiving or transmitting state, even if they won’t transmit or receive anything. HAMA [1] is a conflict-free MAC protocol that combines code and time division schemes to schedule transmissions for unicast and broadcast transmissions respectively. However, code division is not a good alternative for energy-efficient protocols since it does not allow nodes to switch interfaces to sleeping state [3]. TRAMA [14] is also a TDMA-based protocol that achieves energy efficiency by explicitly broadcasting future transmission plans so that nodes that will not transmit nor receive can set their radios in sleeping state in order to save energy. Nodes broadcast transmission plans during a specially designated slot. The main disadvantage of TRAMA is that it does not have a mechanism for balancing network load. FLAMA [13] is a flow-based MAC protocol that assigns weights according to the incoming flows. FLAMA assigns more weight to links whose node has more incoming information. A node transmits if it has the highest priority among its two hop neighbors. This priority is a linear function of the weight and a pseudo random function. The protocol is optimized for a tree topology and it does not always determine if a node must go to sleep, instead, nodes always listen for a period of time, and if they don’t receive a start symbol, then they switch to sleeping state.
Many energy efficient MACs have been pro-posed in the context of wireless sensor networks (WSN). One of the best known is S-MAC [25], which uses a contention approach similar to 802.11 but incorporates periodic sleeping times in order to save energy. These sleeping times are predefined according to the specific expected traffic patterns. When a node is about to go to sleep, it warns it’s neighbors in order to prevent any transmission intended to that node. This scheme is efficient for sensor networks, but if real-time traffic is needed, it’s not possible to wake up a node until its sleeping period concludes and some real-time packets might have large delays. On the other hand, using a contention scheme might lead to high contention in dense networks. An optimization of S-MAC is AEEMAC [19], which allows adaptive sleeping times and reduces contention by piggybacking control packets. Unfortunately, AEEMAC does not eliminate the disadvantages mentioned above. The receiver initiated X-MAC, also called RIX-MAC [10] uses a S-MAC-based approach, but incorporates the concept of short preambles which are beacons that a node sends when it wants to transmit. When a node receives a preamble intended for itself, it answers with an ack that notifies the transmitter that it can proceed with the transmission. If the transmitter node needs to transmit more information, it does that in the next scheduled wake up state.
Asynchronous WSN approaches include SE-MAC [16] which introduces a sub-layer called AAIA that lies between the network and MAC layers. AAIA combines network packets into a single MAC packet to reduce overhead. SE-MAC uses an asynchronous approach similar to that of RTS/CTS, which can lead to collisions.
Other alternatives used in synchronous net-works, such as the one proposed by Tavli and Heinzelman [23] work by forming clusters in the network where a cluster head node is in charge of granting coordinated access to the channel to the nodes on its cluster, thus avoiding collisions and reducing the time nodes spend in the idle state. Unfortunately, all these approaches need to rely on a centralized head node for each cluster and might incur into great overhead if cluster heads fail. It’s also good to note that in this type of protocols data packets might experience large delays.
ECR-MAC [9] is a multichannel approach that uses cognitive radio to jump across channels. It employs two radios: The first one is used for exchanging control packets and the second for transmitting/receiving data. ECR-MAC implements three phases, namely, sensing, reservation and data transmission. The sensing phase is performed to sense which channels are available. The reservation phase occurs in the control channel and it’s used to select a channel for the transmitter-receiver pairs. The disadvantage of using two radios is that nodes use more energy than using a single one. Moreover, for ECR-MAC, all nodes must be either transmitting or listening the whole time in the control channel.
3 System Model and Problem Formulation
We use a graph G = (V, E) to model the topology of a wireless network which is composed of a set V of wireless nodes located over a plane. The position of the nodes in the network is determined by a function p : V → ℝ2 that assigns x and y coordinates to the nodes. Two nodes u, v ∈ V are connected by a link (u, v) ∈ E, if and only if dist(p(u), p(v)) ≤ c, where dist is the Euclidean distance and c is the radio range. We use N(u) = {v|(u, v) ∈ E} ∪ {u} to denote the one-hop neighborhood of u, and N(N(u)) = ∪v∈N(u) N(v) to denote the two-hop neighborhood of u. Every node u ∈ V has a unique identifier denoted by uid.
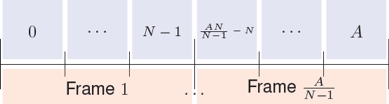
We assume that nodes share the same frequency band and that nodes access the common channel using a time-division multiple access structure organized into frames composed of N time slots. Slots have a duration of τ seconds and the channel can transport B bytes per second. Frames do not have a particular structure and any time slot can be used to transmit signaling or data. There is only one special purpose slot that is used to admit new nodes to the network. This slot occurs every A regular slots, with A >> N. Nodes join to the network by means of hello messages that are transmitted during that slot in a contention-base fashion. Figure 1 illustrates the structure of the frame. We use the position t ∈ [0, N − 1] of a slot within the frame as the slot identifier.
Nodes are equipped with a single radio that can be in any of the available states S = {Sx, Tx, Rx}, where Sx is the sleeping state, Tx is the transmitting state and Rx is the receiving state. The power consumed by a node during a time slot depends on the state of the node during the slot and is described by function φ : S → ℝ.
Iu(f, t) ⊂ N(u) denotes the set of intended receivers of the transmissions of node u at the slot t of frame f and we say that during an interference-free transmission by node u at slot t of frame f, the network can transport up to |Iu(f, t)|Bτ bytes.
A channel access schedule of node u is a function Cu : ℕ × {0, 1, ..., N − 1} → S that assigns a state to node u at every time slot. The network channel access schedule, denoted by CG, is simply defined as the union of the individual channel access schedules, more specifically CG = ∪u∈V Cu. From these concepts, we define a correct channel access schedule as follows.
Definition 1. A network channel schedule CG is correct if the following conditions hold. (i) It is interference-free: For any slot t of any frame f, and for every pair of nodes u, v ∈ V such that Cu(f, t) = Cv(f, t) = Tx, then N(u) ∩ Iv(f, t) = ∅ and N(v) ∩ Iu(f, t) = ∅. (ii) The intended receivers are always in receiving state: For any slot t of any frame f, and for any node u ∈ V such that Cu(f, t) = Tx, then ∀v ∈ Iv(f, t), Cv(f, t) = Rx.
Given a correct network channel access plan CG, the power consumed by the network G is described by Equation 1, where F is the total number of frames the network was active:
Similarly, the total number of bytes transported by a correct channel access plan CG is as by Eq. 2:
Lastly, we define an optimal network channel access schedule as a correct network channel access schedule that minimizes Eq. 1 and maximizes Eq. 2.
4 Energy-Efficient Node Multiple Access
4.1 Overview
Nodes share a single wireless channel, organized into time frames consisting of a fixed number of time slots. Accessing the time slots of each frame is based on distributed elections where nodes use their identifiers to compete against each other to gain interference-free access to the channel. When a node does not have a winning ticket for the current time slot and it is not the intended receiver of a transmitter with a winning ticket, it can set its radio to sleeping mode to save energy. Tickets are published by means of hello packets and everything is soft-state.
We assume that clock synchronization among nodes is achieved by means of a multi-hop time synchronization scheme such as the one implemented in Soft-TDMAC [4] which is a TDMA-based protocol that runs over commodity WiFi hardware. Other alternatives include GPS synchronization, cross-layer ad-hoc network syn-chronization (CLANS) [12] and hybrid alternatives such as the one presented in [20] that uses GPS if available, and a distributed algorithm if not.
4.2 Information Stored and Exchanged
In order to gain access to the channel, nodes use hello messages to publish their own tickets and the tickets of their one-hop neighborhood. Hello messages are sent periodically every H_PERIOD winning slots. Such messages are organized in two sections, the first section includes local information and the second section contains information regarding one-hop neighbors. The structure of a hello message transmitted by node u is shown in Fig. 2 where uid is the unique identifier of node u, k is the number of neighbors of u, v1, . . . , vk is the set of one-hop neighbors of u, and tktv is the number of tickets of node v.
From the hello messages, nodes maintain a data structure that stores the information needed to construct the set of tickets that comprises their corresponding contending sets. On every time slot, the actual tickets are constructed by concatenating the result of a dispersion hash function, with the information about the ticket published in the hello messages. The hash function takes as parameter the concatenation of the node identifier, the index of the ticket, and the identifier t of the current time slot. More specifically, the i-th ticket of node u, at time slot t, denoted by T(u, i, t), is computed by means of Eq. 3, where H : ℕ → ℕ is a dispersion hash function, ⊕ is the concatenation operator, and uid is the identifier of node u. Please note that the node identifier uid and the ticket index i are used to break ties in case of collisions in the hash function:
4.3 Distributed Elections
Let  T be a ticket of node u at slot t and let
T be a ticket of node u at slot t and let  be the set of all the tickets of node u at slot t. We define the contending set of ticket
be the set of all the tickets of node u at slot t. We define the contending set of ticket  , as the set of tickets created on behalf of transmissions that can not occur at the same time as the transmission represented by a ticket
, as the set of tickets created on behalf of transmissions that can not occur at the same time as the transmission represented by a ticket 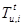 because they would cause collisions at any of the intended receivers. In particular, the contending set at time t of a ticket of node u (u’s contending set for short), denoted by
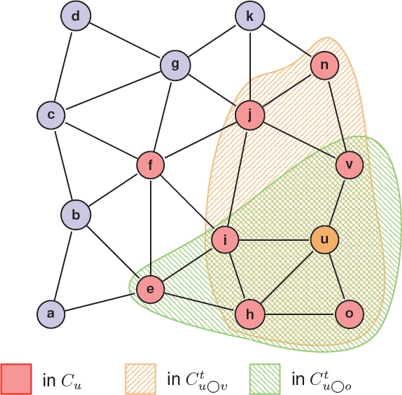
because they would cause collisions at any of the intended receivers. In particular, the contending set at time t of a ticket of node u (u’s contending set for short), denoted by 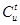 , is composed by the tickets of the nodes in u’s two-hop neighborhood and by the tickets of u itself. This contending set is computed by means of Eq. 4 and an example is shown in Fig. 3. In the figure, the tickets of nodes o, h, i and v belong to
, is composed by the tickets of the nodes in u’s two-hop neighborhood and by the tickets of u itself. This contending set is computed by means of Eq. 4 and an example is shown in Fig. 3. In the figure, the tickets of nodes o, h, i and v belong to 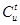 because they are intended receivers of u’s broadcast transmission. The tickets of nodes like e, f, j and n belong to
because they are intended receivers of u’s broadcast transmission. The tickets of nodes like e, f, j and n belong to 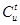 because these nodes are one-hop neighbors of an intended receiver:
because these nodes are one-hop neighbors of an intended receiver:
We also define the notion of the contending set of a ticket of node u, as seen by another node v. The information contained in this set is used by node v to determine whether it is the intended receiver of a neighbor node that holds a winning ticket for the current slot. If that is the case, v has to set its radio to receiving state. Eq. 5 shows the definition of the contending ticket set of node u as seen by node v, denoted by  . As it can be seen in Eq. 5,
. As it can be seen in Eq. 5,  includes the tickets of the one-hop neighbors of nodes in the intersection between the one-hop neighborhoods of nodes u and v.
includes the tickets of the one-hop neighbors of nodes in the intersection between the one-hop neighborhoods of nodes u and v.
Fig. 3 also shows an example of the contending sets of u as seen by nodes v and o. From the figure we can observe that  includes the tickets of nodes in N(u) ∪ N(v) because N(u) ∩ N(v) = {u, v}. The figure also illustrates that
includes the tickets of nodes in N(u) ∪ N(v) because N(u) ∩ N(v) = {u, v}. The figure also illustrates that 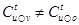 and that
and that  ,
,  . The latter property holds in general and is important for the protocol correctness:
. The latter property holds in general and is important for the protocol correctness:
The winning ticket of a contending set C at time slot t is simply computed as the largest ticket in the set. Note that ties are not possible because at a given slot, tickets are unique.
4.4 Operation of EE-MA
In this section we present the specification of the proposed algorithm. We first define the set S = {Tx, Rx, Sx} as the set of possible states for the radio of a node at a given time, where Tx is the transmission state, Rx the reception state, and Sx is the sleeping state in which the node cannot transmit nor receive.
The purpose of EE-MA is to compute a state s ∈ S for each node u at each time slot t in such a way that the number of concurrent transmissions without interference at the intended receivers is maximized, and at the same time that the energy consumed by the nodes is minimized. As we already mentioned, EE-MA assumes that nodes are synchronized and hence, that the value of the current time slot t is the same at all the nodes.
At each time slot t, every node u uses Algorithm 1 to verify if it currently holds a winning ticket in its corresponding contending set (line 2). If this is the case, u sets its state to Tx, and transmits as many packets as possible. Otherwise, u checks if a one-hop neighbor v holds a winning ticket. u does this by computing the winning ticket in v’s as seen by u contending set (line 5). Lastly, if u is neither a transmitter nor an intended receiver, it sets is radio to sleeping state to save energy (line 9).
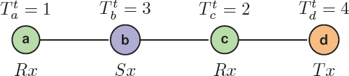
There is one special case where nodes might incur in false positive receptions. Such scenario is shown in Figure 4. Following the algorithm, node a may assume that b holds a winning ticket (because nodes only have information about their 2-hop neighborhood). However, in this example b will set its radio to Sx state since d holds a bigger ticket. In this case node a will waste energy by switching to Rx state and not receiving anything from b.
In order to increase energy savings and reduce the impact of false positives, when a node in Rx state does not receive any information during TxTime << τ seconds, then that node assumes that it will not receive any information during that slot and will switch its radio to Sx state (line 7 of the algorithm 1), thus saving energy during the remaining portion of that slot. TxTime must be large enough to receive any packet allowed by the network.
4.5 Correctness
In this section we present a set of theorems that establish the correctness of the proposed protocol, namely, that it provides interference-free communications, and that the intended receivers are always in receiving state. For all the proofs we assume that nodes know the constituency of their two hop neighborhoods.
Theorem 2. Transmissions are collision-free at the intended receivers.
Proof. We proceed by contradiction and assume that there is a collision at a intended receiver u. Let us assume two different nodes x, y ∈ ℕ (u) transmit at the same time. This is not possible because 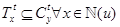 ,
,  and only one ticket can win the election.
and only one ticket can win the election.
Theorem 3. The intended receiver u, of a transmission by a node v ∈ ℕ(u), is in receiving state.
Proof. Since v is transmitting, it means that it has a winning ticket  for a given index i. Therefore, u does not have a winning ticket in
for a given index i. Therefore, u does not have a winning ticket in 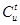 . Now, since
. Now, since 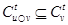 then T(v, i, t) is also a winning ticket in
then T(v, i, t) is also a winning ticket in  and hence, u is receiving state.
and hence, u is receiving state.
5 Performance Analysis
This section presents a set of experiments based on realistic simulations that characterize the performance attained by EE-MA and NAMA [2] which is a representative of the state of the art in MAC protocols based on distributed elections. We use goodput, energy consumption and average channel access time as performance metrics. The goodput is measured in terms of the amount of data bytes received by nodes without considering the control information generated by the protocols. The channel access time is computed as the average time between two consecutive slots that are won by the same node.
5.1 Experiments Setup
In order to assess the performance of the protocols under different density conditions, the simulations were performed within a squared area ranging from 500m × 500m to 1100m × 1100m. For all the experiments, 100 nodes were placed uniformly at random. We performed 20 independent runs with different seeds. The details of the simulation parameters are shown in Table 1. For the results, we computed the confidence intervals with a 95%confidence level.
Table 1 Simulations parameters
| Parameter | Value |
|---|---|
| Sim time | 1000s |
| Tickets per node | 1 |
| Number of nodes | 100 |
| Slot duration | 9.9ms |
| Slot guard | 100ns |
| Slots per frame | 100 |
| Radio transmit rate | 1Mbps |
| Confidence level | 95% |
| Seeds | 20 |
Simulations were performed using the network simulator 3 (ns3 [17]). We implemented the EE-MA and NAMA models, as well as 802.11. All protocols were simulated using the Constant Speed Propagation Delay Model and the Log Distance Propagation Loss Model [15] which are included in ns3. All the simulations use the default radio parameters for the 5GHz version of 802.11. As shown in Table 1 all nodes have a single ticket, and their queues are in saturation.
For the energy consumption analysis, we assigned realistic values of the power consumed by a network interface in each of the four valid states. These energy values are shown in Table 2 and were obtained from [6].
5.2 Results
Figure 5 shows the goodput attained by each of the three protocols. Since we defined the goodput as the amount of useful data transported by the network, when the intended receiver of a packet is a unicast address, only the actual receiver will consider the data received as useful. On the other hand, when a broadcast transmission occurs, multiple receivers will count the data received as part of their goodput. From the figure, we can observe that the goodput attained by EE-MA is similar to that of NAMA. This indicates that the energy efficiency provided by EE-MA has no cost in terms of network capacity. On the other hand, we can denote that both conflict-free protocols outperform 802.11. This reflects that conflict-freedom leads to more bandwidth utilization. This is a salient characteristic of EE-MA because most of previous solutions similar to 802.11, impose an intrinsic trade off between energy efficiency and network capacity.
Figure 6 shows the energy consumed by the network when using the three different channel access protocols. From the figure we can observe that EE-MA is able to reduce the energy consumed by the network in around halve of that of NAMA and 802.11 (which perform very similar) for all the different values in node density. The energy savings come from setting the wireless transceivers in sleeping mode when the protocol detects that the winner of the distributed election is a node located two hops away. As already mentioned, the other source of energy savings is the reduction of false positives, namely, the reduction of the cases in which a node incorrectly infers that it is an intended receiver of a one-hop neighbor who is not the actual winner of the distributed election.
Lastly, Figure 7 shows the mean channel access time incurred by the simulated protocols. Similar to the case of the goodput attained by the protocols, these experiments show that the energy savings attained by EE-MA have no cost in terms of delay (compared to NAMA).
It also shows that both conflict-free protocols perform much better in very dense networks while behaving very similar to 802.11 in less dense networks (close to 1100 × 100m2. This is another salient property of the proposed protocol that contrast with other approaches based on 802.11 that set the radios of the nodes in sleeping state periodically, which tends to induce quite large channel access delays. Unlike these approaches, EE-MA uses an opportunistic strategy that sets the radio of a node in sleeping state only if that node is not going to be neither transmitting nor receiving as intended receiver.
6 Conclusion and Future Work
We introduced the Energy-Efficient Multiple Ac-cess (EE-MA) protocol which is a time-slotted protocol based on lottery scheduling where nodes reach a consensus on which nodes can transmit at every time slot. In order to take advantage of the spatial reutilization of bandwidth, many nodes are allowed to concurrently transmit under the condition that the intersection between the sets composed of their intended receivers is empty. During each time slot, the proposed algorithm identifies the set of nodes that are neither transmitting nor receiving as intended receivers and sets their radios to sleeping state to save energy. Detailed simulations using ns3 revealed that EE-MA significantly reduces energy consumption while maintaining adequate goodput and channel access delays. Simulations showed that conflict-free protocols perform much better than contention based protocols in terms of goodput and channel access delay. Due to these properties, EE-MA is well suited to scenarios where nodes have energy constraints such as in the context of wireless sensor networks.











 nueva página del texto (beta)
nueva página del texto (beta)