1. Introduction
In this document, an alternative way to improve a voice encryption quality is addressed. Some terms as fractional-order oscillators, chaos, complex networks, synchronization, data encryption and state variables modulation are shown. It is recommended to the reader interested in deepening on these topics to read [1-4].
The word chaos derives from the greek word χαοσ, commonly associated with disorder, irregularity, or erratic behaviors [2]. In 1963, Edward Lorenz, an American mathematician and meteorologist, discovered one of the principles of complexity, the chaos. During his research, he observed that the climate exhibits a non-linear behavior known as a sensitive dependence to initial conditions. Using a mathematical model to forecast the behavior of the climate, showed that starting from two nearby points, the trajectories of the system that is currently known as the Lorenz system, diverge rapidly. He explained that this phenomenon makes impossible the long-term weather forecast. Time later, it was known as the butterfly effect [2].
Due to their chaotic nature, the chaotic oscillators are sensitive to their initial conditions, generating apparently random. However, chaos is deterministic [2]. This makes possible to replicate their behavior, if the initial conditions are known. This feature can be used in a secure communication scheme to confuse the attackers.
In a transmitter-receiver communication scheme, it is important to ensure that the initial conditions of the receiver are identical to those of the transmitter in time. If this is not guaranteed, the recovery of the encrypted message can be partial or null.
This is due to the sensitive dependence on the initial conditions presented by the chaotic systems. To guarantee the correct recovery of the message, establishing a communication system that transmits the dynamics of the transmitter in the receiver is needed. This can be achieved by synchrony effect. This phenomenon is responsible for homogenizing the independent dynamics of each oscillator.
The term synchrony meaning “with, at the same time” comes from the Greek σúν “with” and from the Greek mythology χρóνoς “time”. Synchrony, refers to the fact that two different behaviors will be equal in time, if there exists a coupling medium. In 1990, Pecora & Carrol, managed to synchronize two identical chaotic systems with different initial conditions, proving the synchrony phenomenon [5]. Onthe other hand, in order to synchronize non-identical systems, the existence of a generalized synchronization between coupled systems has been studied [6]. Furthermore, the chaos synchronization has been demonstrated by several physical implementations, e.g., [7, 8].
In this paper, the synchronization between N non-integer order identical systems, commonly known as fractional-order systems, is achieved. These systems can be coupled in a complex network that can be defined as an interconnected set of oscillators (two or more).
It is important to mention, that the fractional calculus allows describing and model a real object, more accurately than the classical “integer” methods, [1]. The main reason for using integer-order models was the absence of solution methods for fractional differential equations [9]. At present, there are many methods for approximation of the fractional derivative and integral [1,10].
To encrypt the message using a complex network, for this case, it is needed to synchronize the network first. Once done, any oscillator in the network is selected. A state variable of the selected oscillator is used to encrypt the message, based on the criteria mentioned in Sec. 4. Then, the selected state variable is modulated and used to encrypt the same message to compare the results.
The modulation of chaotic signals has been applied to secure communications schemes. In [11], the authors use chaotic modulation schemes to generate chaotic symbols to improve the physical layer security. In this paper, the chaotic signals are modulated to improve the encryption quality by shifting the energy to the frequency band of the message to be encrypted.
This paper is organized as follows: Section 2 shows some notations and definitions of the fractional calculus. Section 3 shows the synchronization results of a regular complex network composed of N-coupled identical fractional order Lü chaotic oscillators. In Sec. 4, the chaotic encryption results are shown. In Sec. 5, a physical implementation is shown. Finally, in Sec. 6, the conclusions are given.
2. Preliminaries
The term of the fractional derivative was initially found in a letter written for l’Hopital by Leibniz in 1695. In it, the possibility of generalizing the operation of differentiation to non-integers was mentioned. In this section, the method used to solve the fractional order differential equations is shown.
2.1. Fractional order integrals and derivatives
One of the most popular methods for numerical solutions of the fractional-order integrals and derivatives is the Grünwald-Letnikov method. A numerical approximation can be obtained by the following expression derived from the Grünwald-Letnikov definition [1,12]:
The Eq. (1) represents a numerical approximation to de q - th derivative at points kh, where k, ∈ ℕ, k ≠ 0 and h is the time step. The constant Lm is the “memory length” and
are the binomial coefficients cj(q), j ∈ ℕ, calculated as follows:
A general numerical solution of the fractional-order differential equation can be obtained:
The Eq. (3) can be expressed as:
2.2. Complex networks and synchronization
Considering a complex network composed of N identical n-dimensional dynamic subsystems. Each chaotic oscillator is defined by:
with η =1, 2, … ,N.
The xη,i (t) and uη,i terms are the state variables and the control law respectively of the state η in the oscillator i. The control laws are defined as follows:
The constant c > 0 is the coupling strength. The constant δ = 0 if η is not the coupling state, δ = 1 otherwise. A = (aij) ∈ ℝN×N is a constant matrix that denotes the connections between the oscillators in the complex network. If there exists a connection between the oscillators i and j, then the element aij = 1, otherwise aij = 0 or i ≠ j. The diagonal elements of matrix A are calculated as follows:
The identical synchronization of the dynamical network is achieved, if the synchronization error between the state η of the oscillators i and j is zero as t → ∞, i.e. [13]:
with i ≠ j.
The coupling strength c is calculated according to the following lemma [14]:
Lemma 1. Consider network (5). Let λ2 be the largest nonzero eigenvalue of the coupling matrix A of the complex network. The synchronization state of the network (8) defined by x1 (t) = x2 (t) … = xN(t) is asymptotically stable if
where c > 0 is the coupling strength of the network and T > 0 is a positive constant such that zero is an exponentially stable point of the n-dimentional system
By the condition (12), the network achieves synchrony if λ 2 is negative enough. T is a constant such that the self-feedback term −Ty1 stabilizes an isolated system.
It is important to mention that the Lemma 1 is not adapted to the fractional-order systems case.
3. Synchronization of N-coupled fractional-order Lü chaotic oscillators via coupling matrix
In this section, the same principles of Lemma 1 are applied to calculate an approximate coupling strength c. This, to achieve the synchronization of a non-directed complex network composed by N identical fractional-order Lü chaotic oscillators coupled in a star topology.
3.1. Fractional-order Lü chaotic oscillator
The Lü system is known as a bridge between the Lorenz system and Chen’s system [1]. Its fractional version is described as follows [15]:
The set of Eqs. (11) exhibits chaotic behavior for parameters σ = 36, β = 3, γ = 20 and orders q1 = q2 = q3 = 0.95. Figure 1 shows the chaotic attractor of the fractional-order Lü chaotic oscillator.
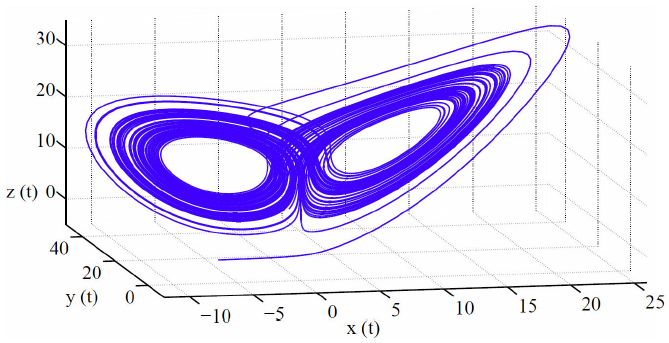
Figure 1 Phase space of the chaotic attractor of the Lü oscillator Eq. (12) for parameters: σ = 36; β = 3; γ = 20, and initial conditions (x(0); y(0); z(0)) = (1; 0:1; 2:5) proyected onto (x(t); y(t); z(t)) space.
3.2. Regular star coupled network
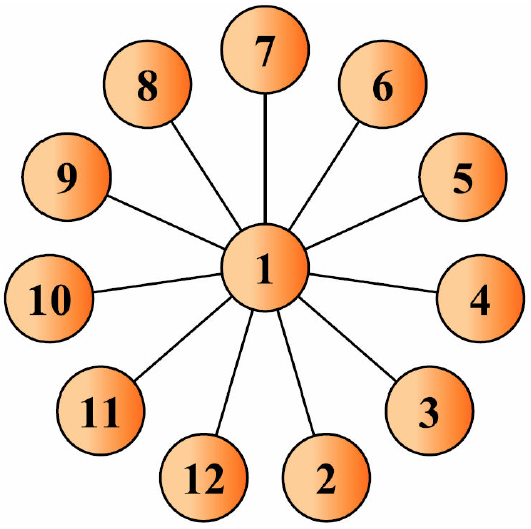
The following coupling matrix A ∈ ℕNxNN = 12, corresponds to the network topology shown in Fig. 2.
In this case, the chaotic oscillators are coupled by the second state variable, i.e., η = 2. By means of the Eq. (6), δ = 0 if η ≠ 2. Therefore, the control laws u2,i for i = 1, …, 12 are applied to the state yi (t) of the complex network. The mathematical model of the complex network is described as follows:
where i = 1, 2, 3, …, 12.
The control laws are defined by:
Table I shows the initial conditions of each oscillator present in the network.
Table I Initial conditions of the complex network.
| Oscillator | x(0) | y(0) | z(0) |
| 1 | 5.0003 | −8.3208 | −2.9502 |
| 2 | −1.3903 | 2.1136 | −8.3510 |
| 3 | 2.3582 | −6.0642 | 0.3310 |
| 4 | 3.2618 | 1.6353 | 5.4132 |
| 5 | 5.0304 | −3.2545 | 1.2853 |
| 6 | −4.7219 | −6.6089 | 4.6241 |
| 7 | 0.0002 | −0.2746 | 4.5556 |
| 8 | 2.9729 | 1.7510 | 6.2513 |
| 9 | 4.6489 | 1.1988 | −3.4518 |
| 10 | −3.2578 | 5.9605 | −8.0592 |
| 11 | −0.1223 | −9.7442 | 5.1025 |
| 12 | 4.3086 | 0.0058 | −0.3542 |
Applying the principles of Lemma 1, the network achieves synchronization with an aproximate coupling strength c = 19. The network achieves identical synchronization and can be graphically observed in Fig. 3.
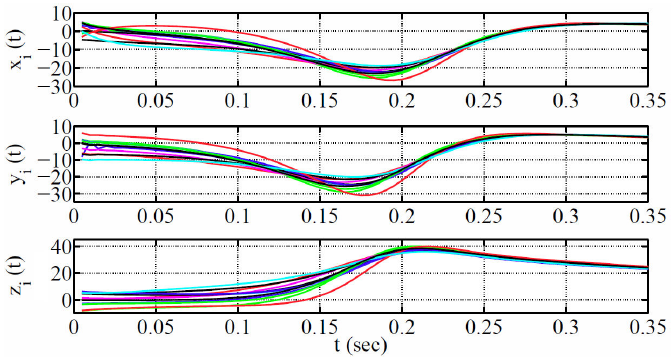
Figure 3 Temporal evolution of some state variables of the complex network: xi (t), yi(t), zi (t), (where i = 1; 2; …, 6).
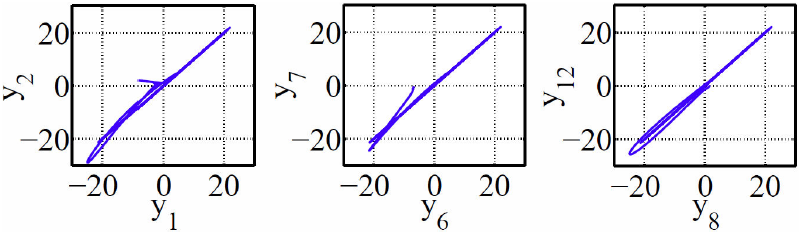
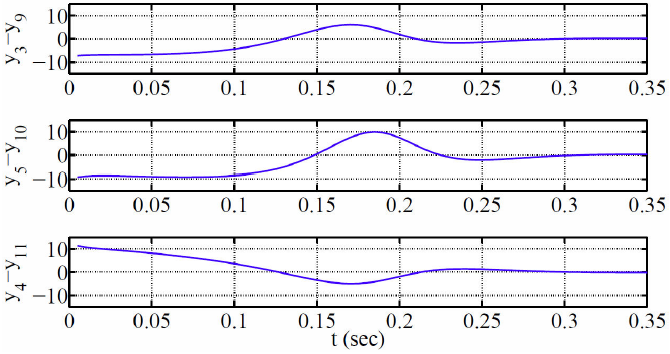
Additionally, Fig. 4 shows some phase portraits of yi (t) state variables of the network. The synchronization errors between some of the yi (t) state variables of the complex network are shown in Fig. 5.
4. Encryption process
In this section, the process to encrypt a voice message is shown. First, the message is encrypted using a selected state variable of a fractional-order Lü chaotic oscillator. Then, the state variables are modulated and used to encrypt the same message. The results are compared.
4.1. Chaotic encryption
By the conventional additive method, a chaotic signal and the message signal are added. This encrypted signal is sent through a public channel. A second chaotic signal is sent and used by the receptor to reproduce a dynamic equivalent to the chaotic signal used to encrypt the message. This signal is subtracted from the encrypted signal, and the message is restored [16]; this is illustrated in Fig. 6.
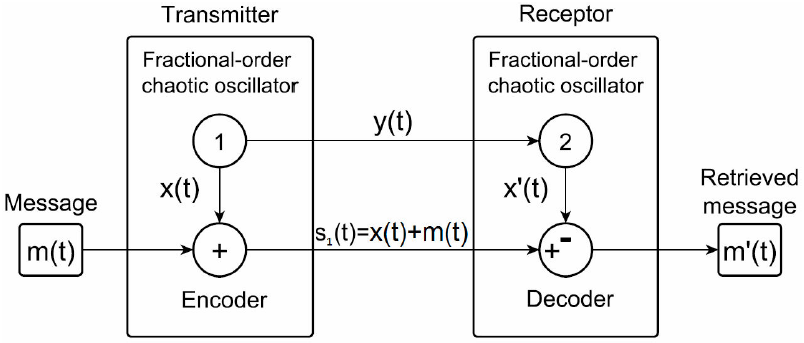
Figure 6 Communication scheme using the conventional additive encryption method. Message m(t), encrypted message s(t), and retrieved message m’(t).
In [17], the authors select a state variable from the network in order to encrypt the message, based on the total energy provided by the chaotic signals and the frequency location of the message. It is important to mention that, once the complex network achieves synchrony, any chaotic oscillator can be selected from the network to use its state variables.
According to the previously mentioned criteria [17]:
Criterion J1: selection based on the chaotic signal energy
with the chaotic signal xc (n) and the message signal m(t), the criterion J1 compares and calculate how many times the energy of xc (n) is higher than the energy of m(t). If J1 >> 1 leads to a good encryption.
Criterion J2: selection based on the chaotic signal energy in the frequency domain
with the chaotic sampled signal Xc (k), the message sampled signal Xm (k), and μ(k) the frequency weighting function. The criterion J2, based on the frequency band of the message, shows how many times the energy of the weighted signal Xc (k) is higher than the energy of the weighted signal Xm (k). If J2 >> 1 leads to good encryption in the selected frequency band.
For numerical solutions, a discrete time criterion is used due to the integration step. The Fast Fourier Transform is used in order to transform the signals from time domain to a frequency domain.
Table II shows the resilts of the criteria J1 and J2 in numerical values. The message to be encrypted: data encrypted with fractional-order chaotic oscillators", is a voice message located in a frequency band of 0.3 kHz - 3kHz recorded with a sampling frequency Fs = 11.025kHz.
Table II Criteria values for the chaotic signals of the synchronization of the complex network.
| State | Ec (107) | J1(104) | J2 |
|---|---|---|---|
| x(t) | 0.2943 | 0.2406 | 26.5344 |
| y(t) | 0.3172 | 0.2593 | 44.1517 |
| z(t) | 1.9887 | 1.6257 | 35.6678 |
From Table II, by the J1 criterion: z(t) provides the highest value. The y(t) state is needed to achieve synchrony. In order to retrieve the message, y(t) is sent via a public channel. We consider x(t) and z(t) as the only possible candidates to encrypt the message. The z(t) state provides the highest energy value in the frequency band in which our message is located. However, we have selected the x(t) state to encrypt the message in order to compare the results obtained after the state variables modulation. Hence, it is selected as the state variable to encrypt the message; the additive chaotic encryption is used.
The encryption results are shown in Fig. 7. Where (a) m(t), is the message to encrypt, (b) s1(t) = x(t) + m(t), is the encrypted message, and (c) m’(t) = s1(t) - x’(t), represents the retrieved message. In Fig. 8, the error between the message m(t) and the retrieved message m’(t) is shown.
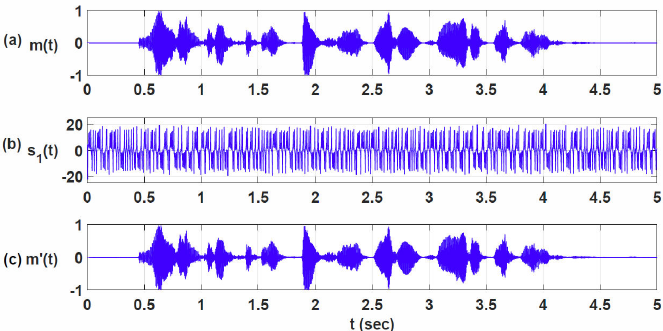
Figure 7 a) Message to be encrypted m(t), b) Encrypted message s 1(t), and c) Retrieved message m’(t).
4.2. Modulation of the fractional-order Lü chaotic oscillator state variables
In this section, the chaotic state variables are modulated and located in the frequency band of the message as an alternative way to ensure that the highest possible energy values provided by the chaotic signals are utilized. The above, leads to an encryption quality improvement.
The resulting product of a sequence x(n) and ejωon is equal to a frequency translation of the spectrum X(ω) by ω0 [4]. The state variables modulation of the first chaotic oscillator of the previously synchronized network is performed as follows:
where ω0 = (2πf0 / Fs). The chaotic signal is shifted to the frecuency band f0. Considering the message m(t) used in Subsec. 4.1: ω0 = π(300 Hz/5512.5 Hz). The communication scheme applying the state variables modulation is shown in Fig. 9.
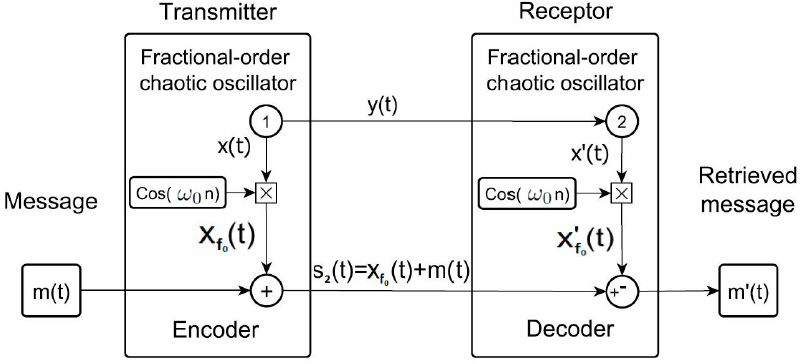
Figure 9 Communication scheme using the conventional additive encryption method and x(t) state variables modulation.
In Table III, J2 represents the total amount of energy provided by the chaotic signal at the frequency band of the message. J2m represents the total amount of energy provided by the chaotic signal at the frecuency band of the message after the state variable modulation. The constant B represents a relation between J2m compared with J2.
It is important to mention that the energy values do not increase by a gain application. The increase of energy values shown in this paper is the result of correctly locating the chaotic signals to the frequency band of the message.
As previously mentioned, the second state of the chaotic oscillator, in this case yf0 (t), is the coupling state variable. It is needed to achieve synchrony and therefore, it is unavaiable to be selected as a candidate to encrypt the message.
From Table III, it is observed that xf0 (t) employing criterion J2m, provides the highest energy value at the frecuency band in which the message is located. Therefore, x(t) is selected to encrypt the message.
Table III Criteria values for the chaotic signals of the synchronization of the complex network.
| State | J2 | J2m | B |
|---|---|---|---|
| xf0 (t) | 26.5344 | 957.1 | 36.1 |
| yf0 (t) | 44.1517 | 1019.6 | 23.1 |
| zf0 (t) | 35.6678 | 713.6 | 20 |
Figure 10 shows the encryption results are after the state variables modulation. Where (a) m(t), is the message to encrypt, (b) s2(t) = xf0(t) + m(t), is the encrypted message, and (c) m’(t) = s2(t) - x’f0 (t), represents the retrieved message.
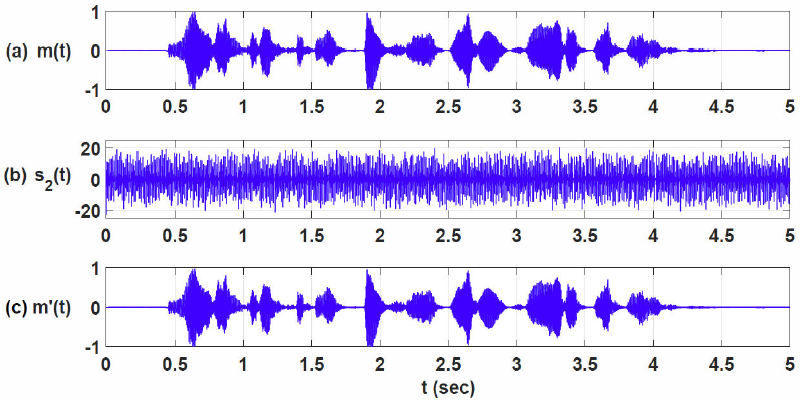
Figure 10 a) Message to be encrypted m(t), b) Encrypted message s2(t), and c) Retrieved message m’(t).
Figure 11 shows the error between the message m(t) and the retrieved message m’(t) when xf0(t) is used.
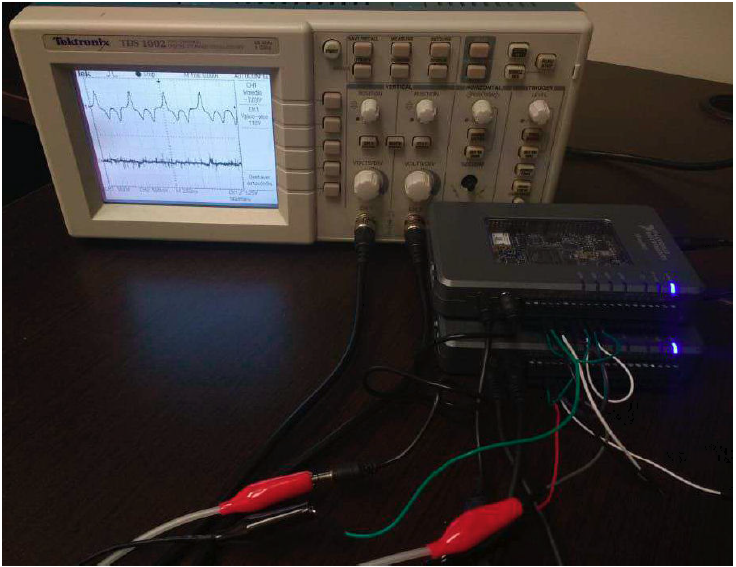
5. Physical implementation
In this section, FPGA realization of a communication scheme composed of two identical fractional-order systems is presented.
We use two National Instruments MyRIO 1900 for implementation. Both MyRIO are connected following a transmitter-receiver scheme. Their technical characteristics are identical and they are described as follows:
Xilinx Z-7010 processor 667 MHz (ARM Cortex A9 x 2 cores 28mm process NEON SIMD, VFPv3 Vector Float). Memory: NV: 256 MB, DDR3 512 MB, 533 MHz, 16 bits. FPGA type: same as the processor. Wireless: IEEE 802.11 b, g, n ISM 2.4 GHz 20 MHZ. USB 2.0 Hi-Speed, breakout board support, 2 ports of 16 Digital I/O lines, 3 axis accelerometer. Max power consumption: 14 W, typical idle: 2.6 W and LED’s.
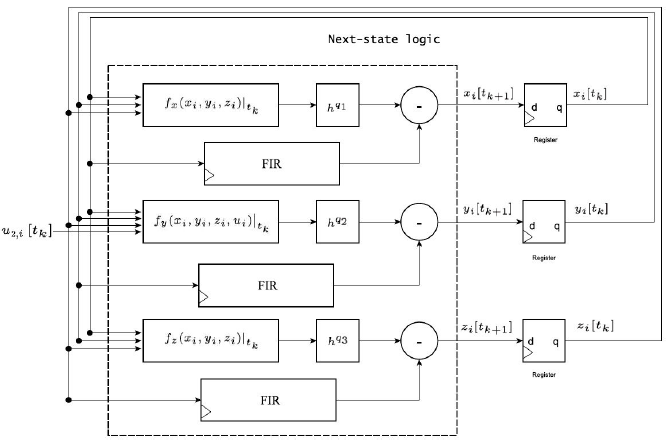
By using the Grundwald-Letnikov method to solve the fractional order numerical integration, the Lü digital aproximated system is defined as:
Where
and
Due to hardware storage capacity limitations, we use a simple master-slave topology and a memory length Lm = 8. The parameters previously shown in the subsection 3.1 are used.
Consider the encoder modulated states defined by x[tk], y[tk], z[tk], and the decoder modulated states defined by x’[tk], y’[tk], z’[tk].
Figure 12a) shows the 2D atractor x[tk] vs y[tk]. Figure 12b) shows x[tk] (above) and y[tk] (under) time evolution. Figure 12c) shows y[tk] vs y’[tk] portrait, providing a graphical demonstration of synchrony.
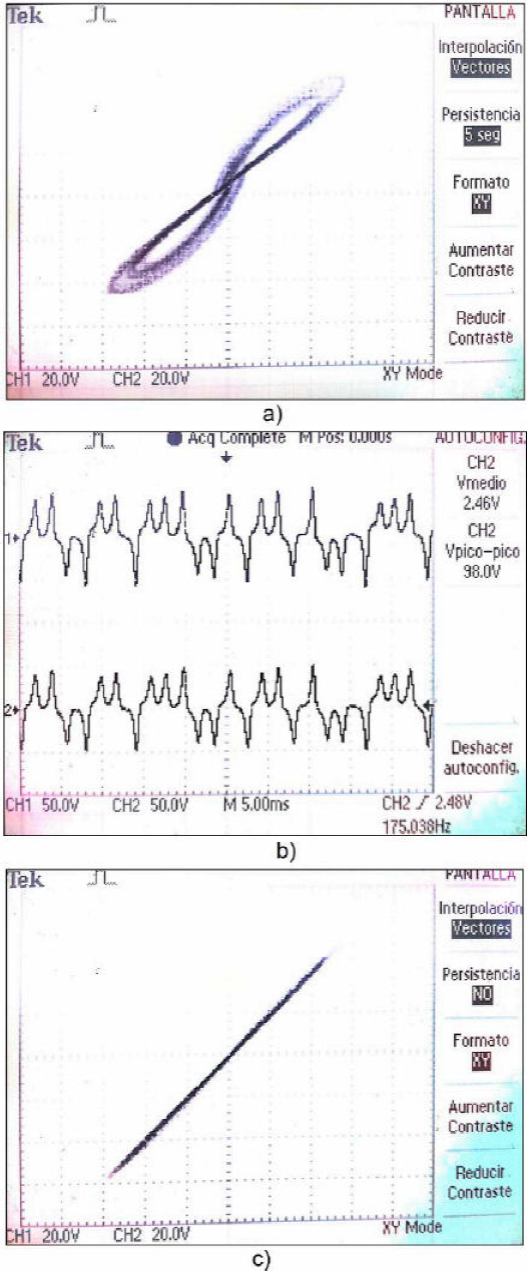
Figure 12 a) 2D chaotic strange attractor formed by x[tk] vs y[tk], b) Time evolution of x[tk] and y[tk], c) Confirmed synchronization of the second state y[tk] vs y’[tk].
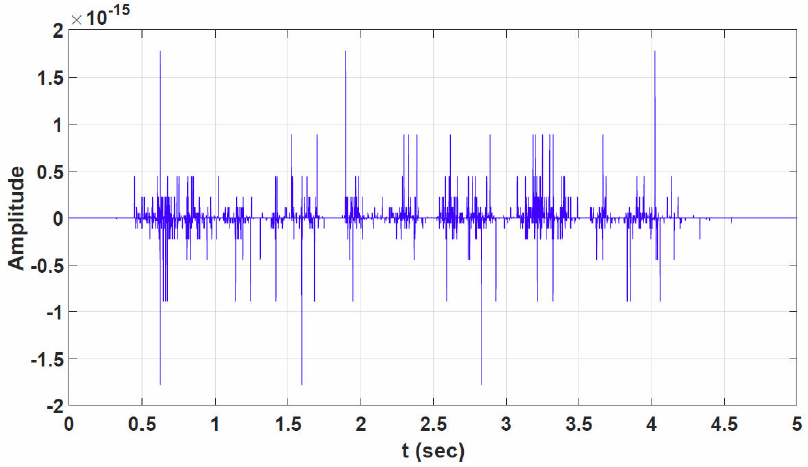
Figure 13a) shows y[tk] time evolution (above) and the synchronization error defined by e[tk] = y’[tk] - y[tk] (under). Figure 13b) shows y[tk] (above) and the encrypted data defined by s[tk] = s[tk] = x[tk] + m[tk] (under).
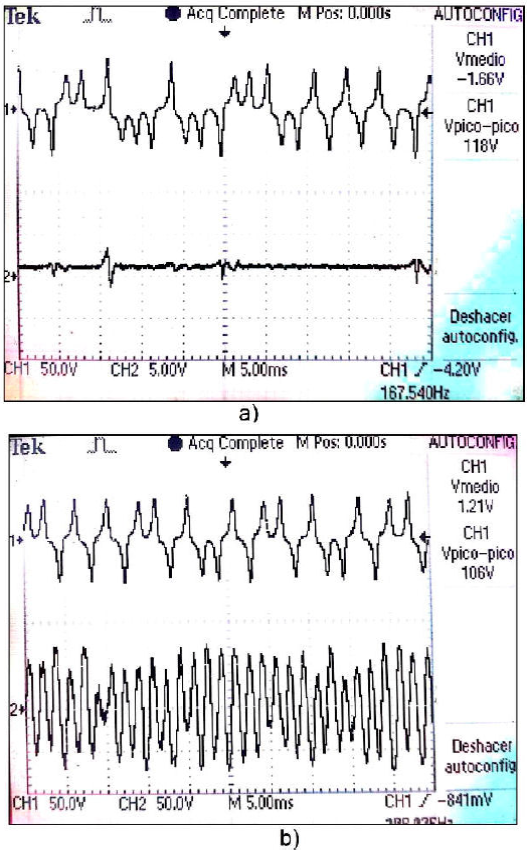
Figure 13 a) Time evolution of the state variable y[tk] (above) and the time evolution of the synchronization error e[tk] = y’[tk] − y[tk] (under), b) Dynamic of the state variable y[t k], and the encrypted data signal s[tk] = x[tk] + m[tk].
Figure 14 shows the hardware used for physical implementation.
Figure 15 shows the block diagram corresponding to (22). We use a memory length Lm = 8 in order to save resources of the FPGA. The FIR blocks correspond to the filtering process of the states through the binomial coefficients
6. Conclusions
To retrieve the message, y(t) is used to achieve synchronization. Thereby, y(t) is not eligible as a candidate to encrypt the message. We only consider x(t) and z(t) as candidates to encrypt the message. Providing the highest value of energy is not enough property to select a signal as a good candidate to encrypt a message. Considering the frequency band in which the message is located is recommended. The J2 values show how z(t) provides the highest energy value. However, using the criterion J2m, we can observe that the energy of xf0 (t) is higher than the energy provided by zf0 (t). By modulating the fractional order Lü chaotic oscillator state variables, we shifted the energy to the frequency band of the message, helping us to improve the encryption quality by an approximate factor of 36.











 nueva página del texto (beta)
nueva página del texto (beta)